After months of testing, the Google Chrome development team has now enabled site isolation for desktop users to protect against Spectre and Meltdown flaws.
Spectre and Meltdown flaws are problems in the modern processor design process. Unfortunately, this vulnerability has a wide range of effects and cannot completely fix.
Attackers can use the vulnerability to read sensitive data from other threads, such as the password of the system login user or the application download or pending data.
Attacking malicious code through a browser is more convenient, and the Google Chrome development team uses site isolation technology to mitigate the vulnerability.
Google Chrome defaults to site isolation technology:
The so-called site isolation technology means that all websites opened by users use different processes, and each process is isolated from each other and must not access each other’s data.
This multiple process sandboxing method prevents malicious code from exploiting the Spectre and Meltdown flaws of modern processors to read sensitive information from other processes.
Of course, the Google development team also stated that this method is only defence and mitigation, so it is not 100% completely preventing malicious code from exploiting processor vulnerabilities.
Unexpected circumstances allowed Google to enable the technology in advance:
Initially, this feature is still in the testing stage. In previous versions of the updated article, Blue Point Network mentioned that Google is collecting opinions from web developers.
Because this feature may cause compatibility or functional issues on some sites, developers need to test this before submitting it to the Google team.
But two researchers at the Massachusetts Institute of Technology’s Computer Science and Artificial Intelligence Laboratory recently discovered a more serious vulnerability to the Spectre.
Therefore, the Google development team decided to open this feature in advance to help users deal with potential attacks, and improve security for users who frequently browse the web.
Site isolation technology can also defend against UXSS attacks:
UXSS is a universal cross-site scripting attack that belongs to the branch of XSS cross-site scripting attacks. I haven’t seen too many attack cases using UXSS.
This type of vulnerability usually allows an attacker to bypass the same-origin policy of the renderer process, although it does not allow the attacker to control the process fully but is potentially harmful.
However, the child process and sandbox generated by the site isolation technology will take up more memory, but Google promises to continue to optimise the memory to improve response speed.
Known issues:
After opening the site isolation technology, the average memory occupied by Google Chrome is about 10% more than usual, and Google will continue to optimise to reduce the memory footprint.
For WEB developers: Google Chrome browser tools that enable this feature will not fully support cross-site iframe inline frame content.
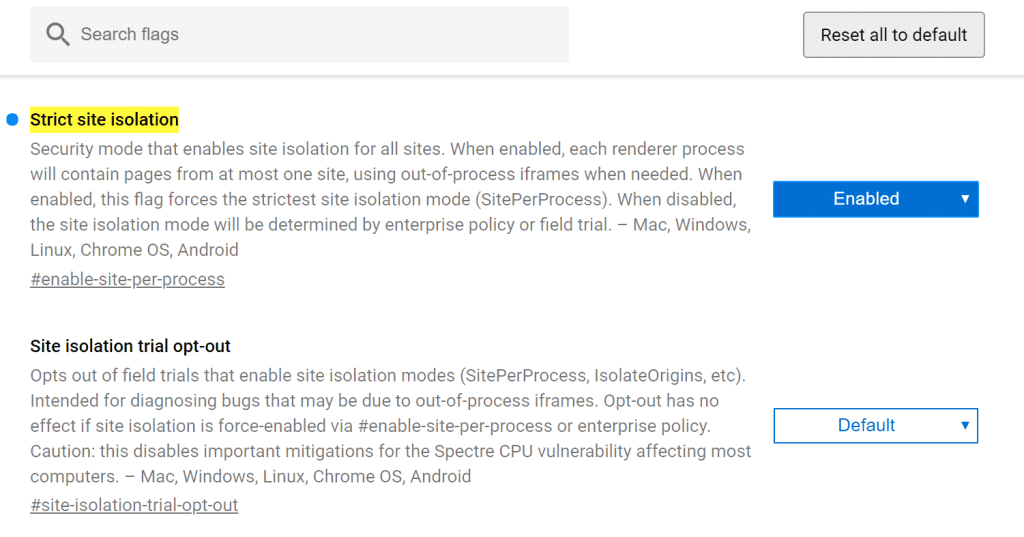
Domestic users please manually open:
For some reasons, the Google Chrome cloud adjustment policy may not be sufficient for users, so users should manually enable the feature for security reasons.

In the Google browser address bar, type chrome://flags/#enable-site-per-process and change the default setting of the policy to Enabled.