How App-Bound Encryption Works
In a move to bolster user protection against cookie theft and infostealer malware, Google Chrome has introduced a new security feature called App-Bound Encryption for Windows users. This enhancement aims to safeguard sensitive data like cookies, passwords, and payment information from unauthorized access.
Cybercriminals have long exploited cookie theft to compromise user accounts, track online activity, and even steal financial information. While Chrome has implemented several security measures like Safe Browsing and account-based threat detection, the risk of cookie theft remains a persistent concern.
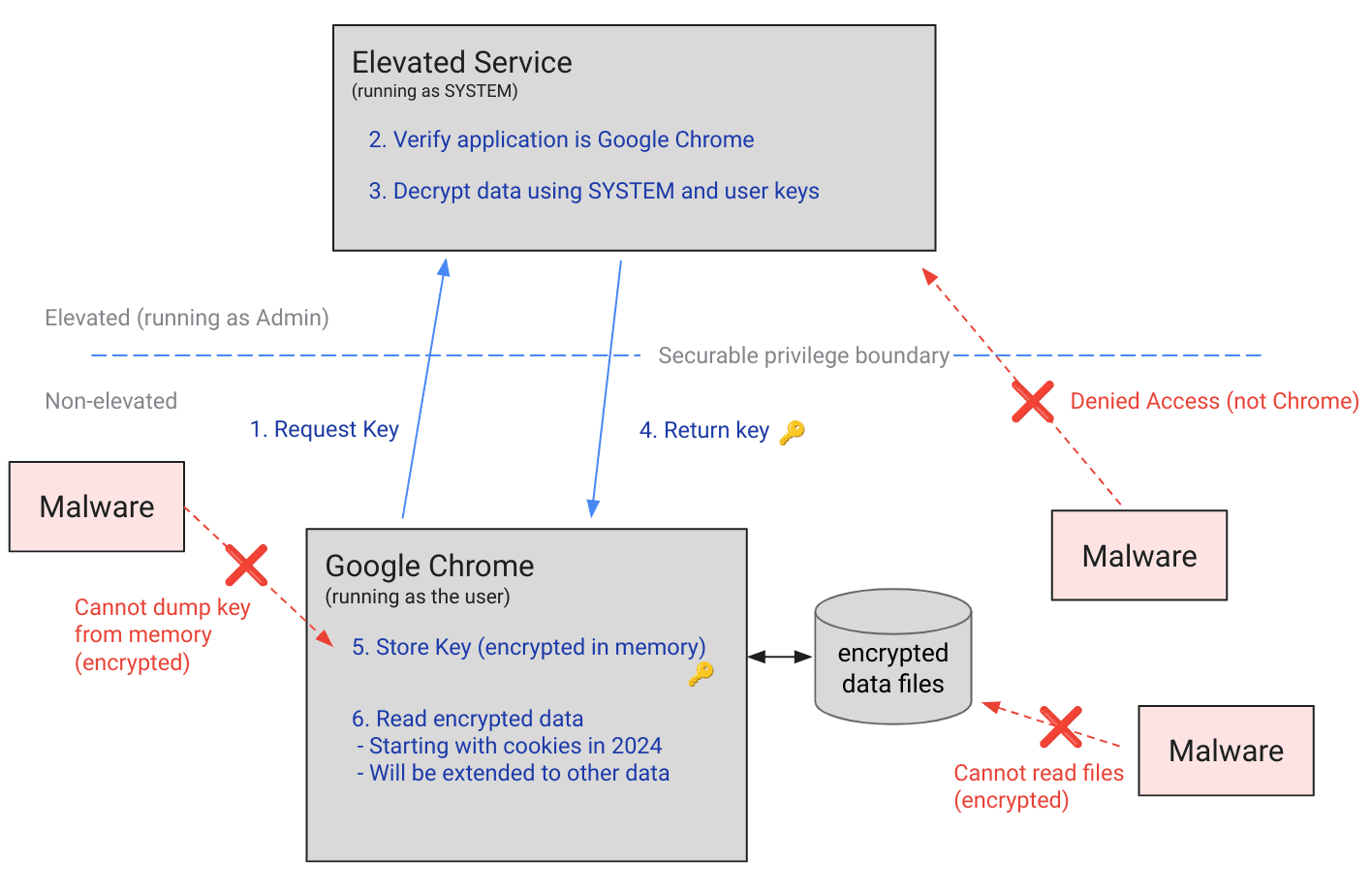
With App-Bound Encryption, Chrome takes a significant step forward in protecting user data on Windows. This feature leverages the operating system’s Data Protection API (DPAPI) but goes further by binding encryption keys to specific applications. This means that only Chrome itself can decrypt its encrypted data, effectively preventing unauthorized access from malicious software.
App-Bound Encryption relies on a privileged service to verify the identity of the requesting application. When Chrome encrypts data, it embeds its unique identity into the encryption process. Any attempt to decrypt this data by another application will fail, even if it runs under the same user account.
This added layer of security makes it significantly more difficult for infostealer malware to steal sensitive data. In the past, malware could simply execute code under the user’s account to gain access to Chrome’s data. Now, attackers must escalate privileges to the system level or inject code directly into Chrome, actions that are more likely to trigger security alerts and be detected by antivirus software.
Related Posts:
- Crafty Infostealer Campaign Leverages Fake Adobe Reader Installer, Advanced Tricks to Evade Detection
- Inside a Python Infostealer: How Attackers Abuse Legitimate Platforms for Credential Theft
- Agent Tesla Loader Evolves: New Evasive Techniques Pose Rising Threat