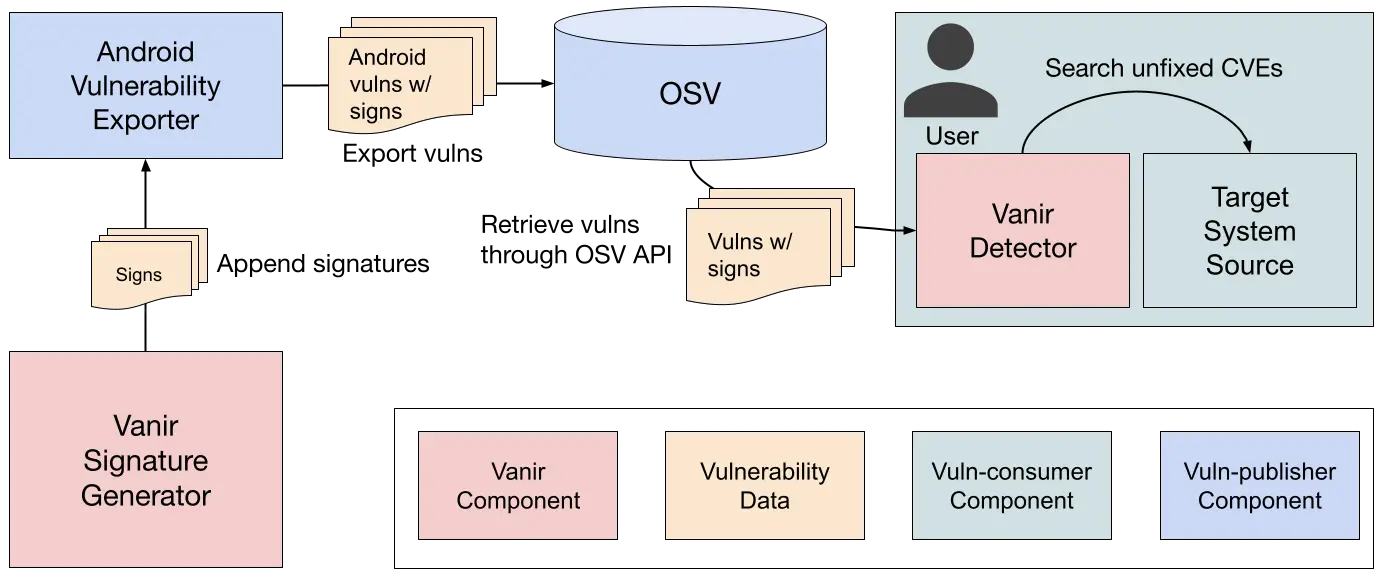
In a move set to redefine security patch validation, Google announced the public availability of Vanir, an open-source tool designed to revolutionize how developers identify and address security vulnerabilities.
Initially developed for Android, Vanir offers a potent solution to the complex challenge of managing security patches across a myriad of devices and software versions. As Google’s blog states, “This strengthens the security of the Android ecosystem, helping to keep Android users around the world safe.”
What sets Vanir apart?
- Source-Code-Based Static Analysis: Unlike traditional methods that rely on potentially error-prone metadata, Vanir delves directly into the source code, providing a more accurate and comprehensive analysis.
- Automated Patch Identification: Vanir automates the laborious process of manually identifying missing patches, significantly reducing the time and resources required.
- Versatility: While designed for Android, Vanir can be readily adapted to other ecosystems, making it a valuable asset across the software development landscape.
“A main focus of Vanir is to automate the time consuming and costly process of identifying missing security patches in the open source software ecosystem,” Google emphasizes in their blog.
Early Success and Future Potential:
Early adoption of Vanir has already yielded impressive results. Google reports that a single engineer, using Vanir, was able to “generate signatures for over 150 vulnerabilities and verify missing security patches across its downstream branches – all within just five days.”
With its open-source nature, Vanir promises to foster collaboration and drive innovation in the security community. “By open-sourcing Vanir, we aim to empower the broader security community to contribute to and benefit from this tool, enabling wider adoption and ultimately improving security across various ecosystems,” says Google.
Vanir is available now on Github.