goscan v2.4 releases: Interactive Network Scanner
GoScan
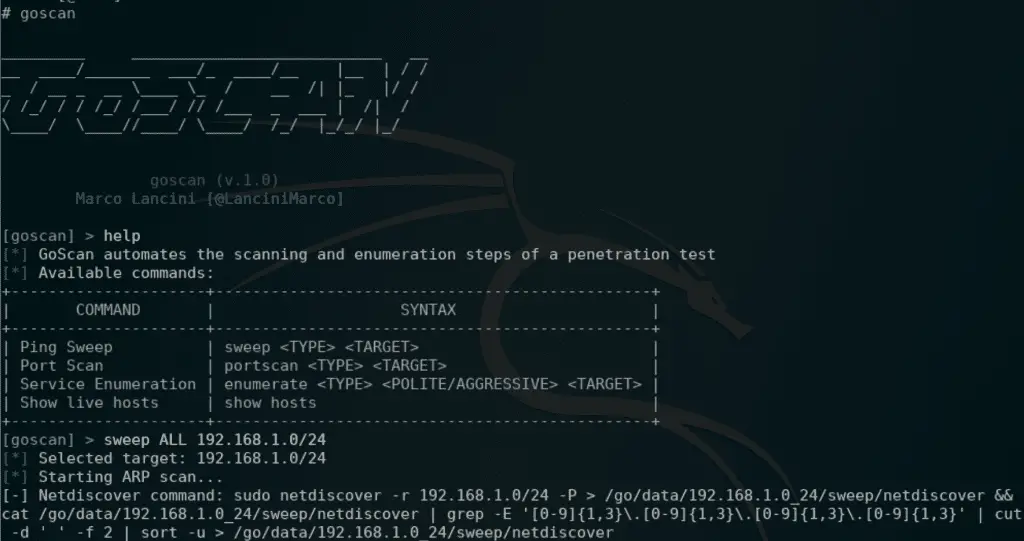
GoScan is an interactive network scanner client, featuring auto-complete, which provides abstraction and automation over nmap.
It can be used to perform host discovery, port scanning, and service enumeration in situations where being stealthy is not a priority, and time is limited (think of CTFs, OSCP, exams, etc.).
GoScan supports all the main steps of network enumeration:
- Host Discovery (ARP + ping sweep): sweep <TYPE> <TARGET>
- Port Scanning: portscan <TYPE> <TARGET>
- Service Enumeration: enumerate <TYPE> <POLITE/AGGRESSIVE> <TARGET>
Plus some more:
- DNS enumeration: dns <DISCOVERY/BRUTEFORCE/BRUTEFORCE_REVERSE> <DOMAIN> [<BASE_IP>]
- Domain enumeration (Extract windows domain information from enumeration data): domain <users/hosts/servers>
In addition, it has a few supporting commands:
- Change the output folder (by default ~/goscan): set_output_folder <PATH>
- Modify the default nmap switches: set_nmap_switches <SWEEP/TCP_FULL/TCP_STANDARD/TCP_VULN/UDP_STANDARD>
- Modify the default wordlists: set_wordlists <FINGER_USER/FTP_USER/…>
- Show live hosts: show hosts
- Show detailed ports information: show ports
- Reset the database: db reset
External Integrations
The Service Enumeration phase currently supports the following integrations:
| WHAT | INTEGRATION |
|---|---|
| ARP |
|
| DNS |
|
| FINGER |
|
| FTP |
|
| HTTP |
|
| RDP |
|
| SMB |
|
| SMTP |
|
| SNMP |
|
| SSH |
|
| SQL |
|
Changelog v2.4
Fixed
- Improved documentation related to building from source
Use

Copyright (c) 2018 Marco Lancini





