Graph of PaaS communication flow | Image: Cisco Talos
A new, sophisticated phishing-as-a-service (PaaS) offering has been discovered by researchers from Cisco Talos, dubbed “Greatness.” Active since at least mid-2022, Greatness combines multi-factor authentication (MFA) bypass, IP filtering, and Telegram bot integration. Currently, it focuses on Microsoft 365 phishing, making it a significant threat to businesses worldwide.
Greatness provides its users with a link and attachment builder, crafting convincing decoy and login pages. It’s capable of pre-filling victims’ email addresses and displaying appropriate company logos and backgrounds, making it increasingly potent against unsuspecting business users.
The primary targets so far have been companies in the U.S., U.K., Australia, South Africa, and Canada, with the manufacturing, healthcare, and technology sectors being the most commonly hit. Interestingly, Greatness seems to have a slight geographic focus in each campaign, but collectively, over half of all targets are based in the U.S.

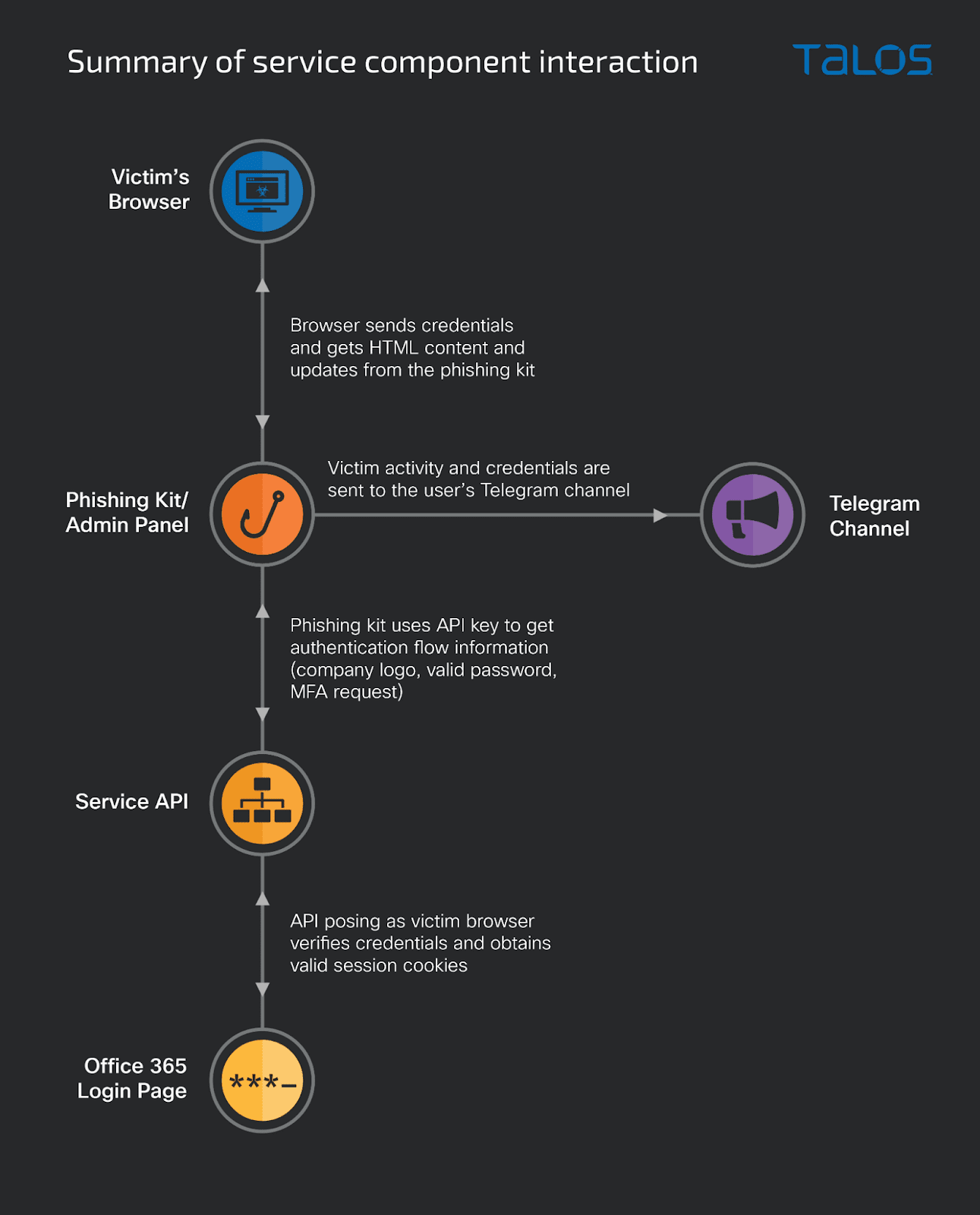
Greatness operates by providing a phishing kit to affiliates, which includes an API key enabling even unskilled actors to exploit the service’s advanced features. The phishing kit and API work in concert, acting as a proxy to the Microsoft 365 authentication system, and stealing the victim’s credentials through a “man-in-the-middle” attack.
The attack unfolds in multiple stages. Initially, victims receive a malicious email containing an HTML file, masquerading as a shared document. Opening the attachment launches obfuscated JavaScript code that fetches the phishing page HTML code from the attacker’s server. The page then redirects the victim to a convincing Microsoft 365 login page, pre-filled with the victim’s email address and the company’s custom background and logo.
When the victim enters their password, the PaaS connects to Microsoft 365, impersonates the victim, and attempts to log in. If MFA is deployed, the service prompts the victim for MFA authentication. Upon receiving the MFA, it continues the impersonation, completes the login process, and collects the authenticated session cookies. These are then delivered to the affiliate either through their Telegram channel or directly via the web panel.
The service comprises three components: the phishing kit (including an admin panel), the service API, and a Telegram bot or email address. The phishing kit delivers the HTML/JavaScript code for each step of the attack, forwards the credentials from the victim to the PaaS API, and receives information on which page it should deliver next to the victim. The kit also stores the stolen credentials for the affiliate and sends them to the affiliate’s Telegram channel, if configured to do so.
An administration panel allows the affiliate to configure the service API key and Telegram bot and track stolen credentials. It also generates malicious attachments or links to be sent via email to the victims.
In conclusion, the Greatness phishing service is a significant new threat to businesses worldwide. Its advanced features, combined with its focus on Microsoft 365 users, make it a potent tool in the hands of cybercriminals. Companies need to be aware of this new threat and implement robust security measures to safeguard their sensitive information.