h8mail v2.5.6 releases: Email OSINT and password breach hunting
h8mail
Email OSINT and password finder.
Use h8mail to find passwords through a different breach and reconnaissance services, or the infamous “Breach Compilation” torrent.
Features
- 🔎 Email pattern matching (regexp), useful for all those raw HTML files
- 🐳 Small and fast Alpine Dockerfile available
- ✅ CLI or Bulk file-reading for targeting
- 📝 Output to CSV file
- ➿ Reverse DNS + Open Ports
- 👮 CloudFlare rate throttling avoidance
- Execution flow remains synchronous and throttled according to API usage guidelines written by service providers
- 🔥 Query and group results from different breach service providers
- 🔥 Query a local copy of the “Breach Compilation”
- 🔥 Get related emails
- 🌈 Delicious colors
APIs
| Service | Functions | Status |
|---|---|---|
| HaveIBeenPwned | Number of email breaches | ✅ |
| Shodan | Reverse DNS, Open Ports | ✅ |
| Hunter.io – Public | Number of related emails | ✅ |
| Hunter.io – Service (free tier) | Cleartext related emails | ✅ |
| WeLeakInfo – Public | Number of search-able breach results | 🛃 |
| WeLeakInfo – Service | Cleartext passwords, hashes and salts | 🔜 |
| Snusbase – Service | Cleartext passwords, hashes and salts – Fast ⚡️ | ✅ |
Changelog v2.5.6
- fix snusbase API
- fix breachdirectory search limitation
- fix format string in output
What’s Changed
- Breachdirectory domain change by @noraj in #131
- Fixed “TypeError: can only concatenate str (not “int”) to str” in print_json.py by @shifoc in #143
- 2.5.6 by @khast3x in #144
Install
Local env
Docker
Usage
examples
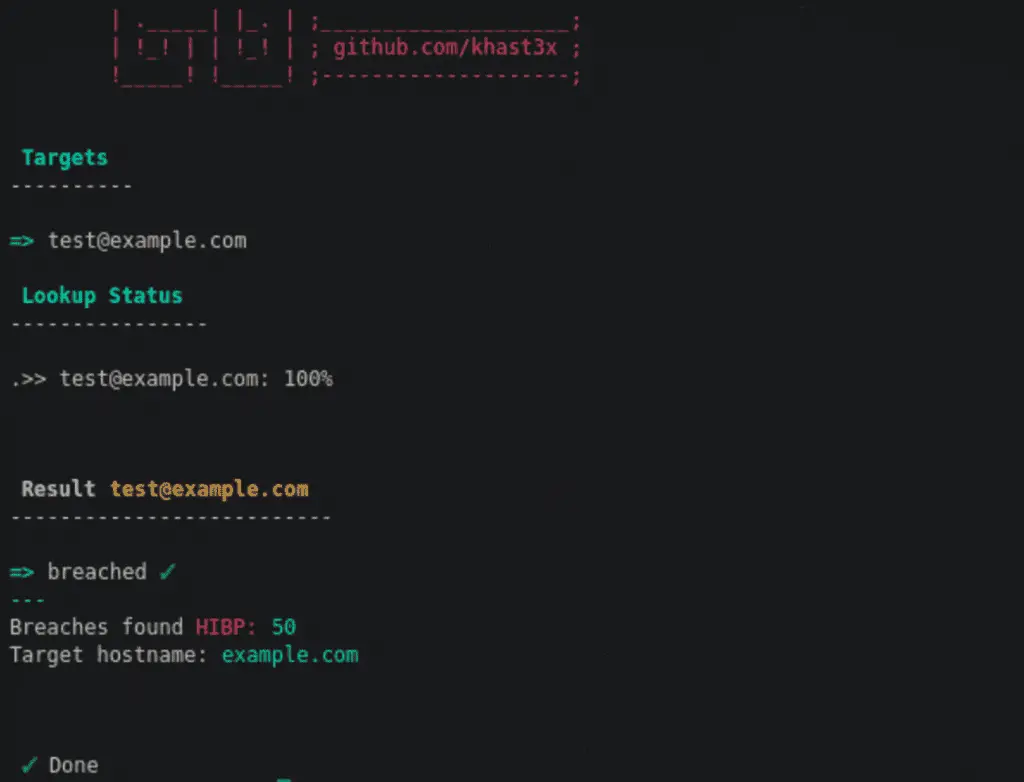
Query for a single target
python h8mail.py -t target@example.com
Query for the list of targets indicate config file for API keys, output to pwned_targets.csv
python h8mail.py -t targets.txt -c config.ini -o pwned_targets.csv
Query a list of targets against a local copy of the Breach Compilation, pass API keys for Snusbase from the command line
python h8mail.py -t targets.txt -bc ../Downloads/BreachCompilation/ -k “snusbase_url:$snusbase_url,snusbase_token:$snusbase_token”
Query without making API calls against a local copy of the Breach Compilation
python h8mail.py -t targets.txt -bc ../Downloads/BreachCompilation/ –local
Copyright (c) 2019, khast3x
All rights reserved.
Source: https://github.com/khast3x/





