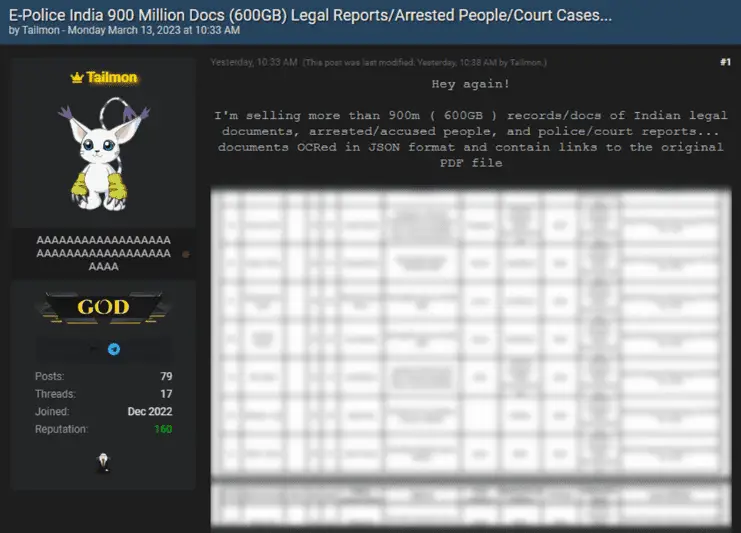
On a certain forum, a user claims to possess a database containing over 900 million Indian legal documents, including detailed information on Indian police records, reports, court cases, as well as defendants and arrested individuals. It is understood that this user is selling this data on the forum, with a total file size of about 600GB, in JSON format, and providing links to the original PDF files. At present, the authenticity of this data has not been confirmed, and it is unclear how the hacker obtained this data. It should be noted that the open sale of such sensitive information could lead to serious subsequent consequences, such as personal information abuse, fraud, and extortion.
The hacker who posted this on the leak website is a “God” level user, using Tailmon as their profile picture. On March 13, 2023, Tailmon wrote in a post on the leak website that “I am selling over 900 million (600GB) records/docs of Indian legal documents, arrested/accused people, and police/court reports… documents OCRed in JSON format and contain links to the original PDF file.”

In recent years, numerous incidents of data leaks and cyber-attacks have highlighted the importance of data security and privacy. This legal document sale event further emphasizes the need for strict measures to protect sensitive information.
For the Indian government, it is necessary to take immediate action to investigate this matter, and if this data leak is true, it must take measures to prevent the spread of data. Subsequently, Indian authorities may enforce stricter regulations to ensure that companies and individuals handling personal information comply with data protection laws.
Furthermore, this security incident also serves as a warning for individuals and organizations to take appropriate measures to protect their data. This includes strengthening network security, training employees on data security awareness, and regularly updating their security protocols to address potential threats.
Via: izoologic