The latest report from FireEye security companies shows that hackers are inserting backdoors into victims through security vulnerabilities in older versions of Microsoft Office. The above vulnerability Microsoft has been fixed in the second half of last year, so users weren’t affected by the vulnerability after installing the latest update.
FELIXROOT backdoor program:
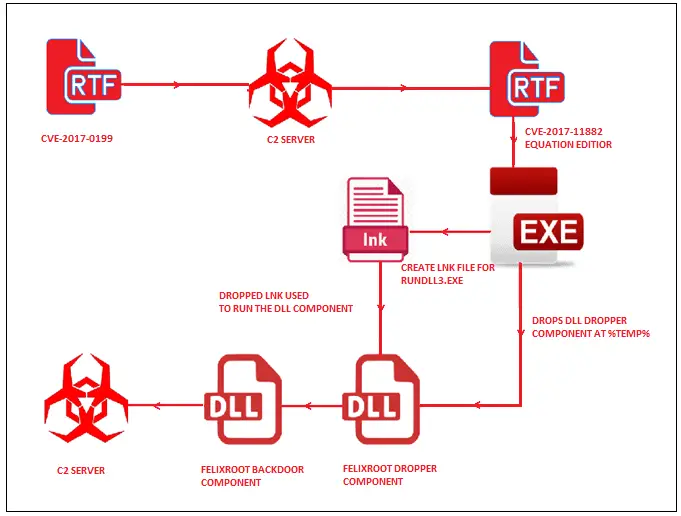
This attack was initiated by phishing emails carrying RTF files containing malicious code. Once opened, the exploits can be exploited to exploit the vulnerability.
The hacker claimed in the phishing email that this is a document about the environmental protection seminar, so the unknown user would be induced to download and open the RTF document.

After opening, the malicious code starts running and contacts the remote control server to get the instructions. The system process runs a backdoor named FELIXRROOT.
After the backdoor program loaded successfully, it can start collecting private information on the victim’s computer, then package and compress it and upload it to the remote C&C server for saving.
Self-cleaning after the collection is completed prevents the discovery:
For espionage, the backdoor program only collects information and does not cause any damage to the computer, so it does not want to be discovered after the purpose of receiving.
Therefore, after collecting the information, the backdoor program stops executing the action and then starts to clean up the data, and deletes all the traces of its documents and its self and destroys itself.
Currently, the security company has not completed tracking of the backdoor program, so it is not clear which interest-related hacking gangs the backdoor program may involve.
Routine safety reminder time:
Most attacks against Microsoft Office rely on vulnerabilities and documents that carry malicious code and induce users to open to load other malware.
Keeping Microsoft Office updates is the best solution for users, and continuing updates can block security vulnerabilities that have already been discovered.
Besides, do not open any documents of unknown origin. In most cases, the attachment documents sent by non-contacts are not advertisements and contain malicious code.
Source, Image: FireEye