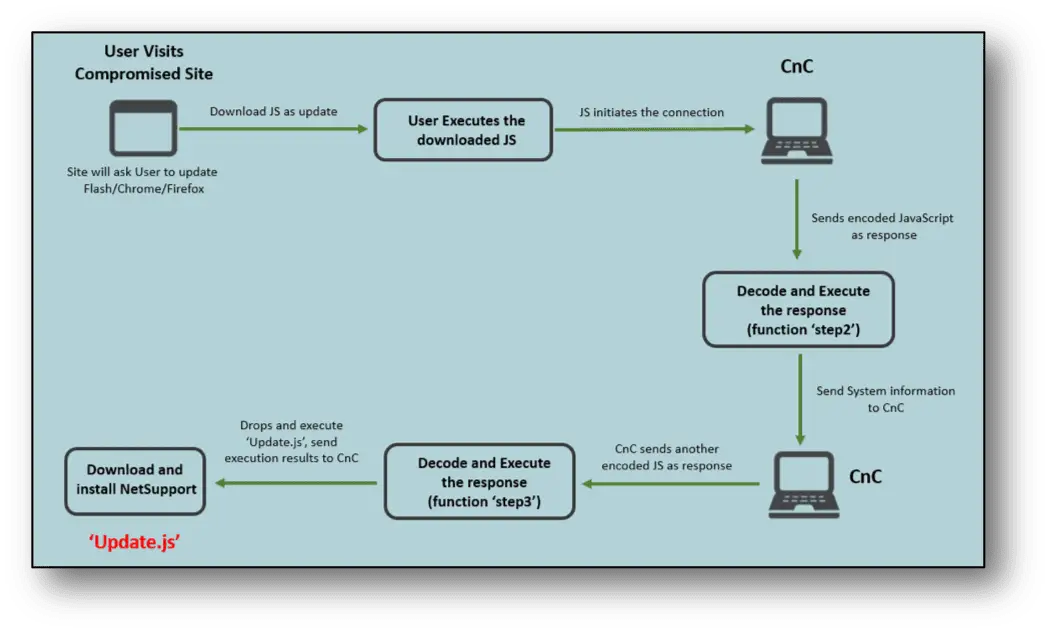
FireEye released a report that traces a special cyberattack campaign that has used infected websites to spread bogus software updates over the past few months in order to install NetSupport Manager remote access tools on victim devices.
NetSupport Manager is a commercial RAT that allows administrators to access client computers remotely. However, the researchers found that the malicious attacker was misusing the RAT and silently installed it on the victim’s computer to gain unauthorized access to the device.
Malicious attacker misuse infected websites to spread fake Adobe Flash, Chrome, and FireFox. Once users accept updates, they will download malicious JavaScript files.

Image: FireEye
FireEye pointed out that JavaScript malware collects basic system information and sends it to the server, receives other commands from the server, and then executes JavaScript commands to deliver the final Payload. This JavaScript named Update.js is executed from %AppData% with the help of wscript.exe.
The developer of this malware made multiple layers of obfuscating the original JavaScript and managed to make the analysis of the second JavaScript file more difficult. By using the call and called function code to obtain the decryption key, the attacker can ensure that once the analyst adds or deletes content, the script does not retrieve the key and causes the exception to terminate.
After the initial execution, JavaScript will open a connection with the Command & Control (C&C) server and send the value named tid and the current date of the system in an encoded format. The script then decodes the server response and executes it as a function named step2. This function is responsible for collecting various system information and sending it to the server. The collected information includes: “Architecture, ComputerName, UserName, Processors, OS, Domain, Manufacturer, Model, BIOS_Version, AntiSpywareProduct, AntiVirusProduct, MACAddress, Keyboard, PointingDevice, DisplayControllerConfiguration, ProcessList.“
After that, the server responds with the encoded content: Update.js named step3 function and downloading and executing the final payload.
The software uses PowerShell to download multiple files from the server, including a 7zip stand-alone executable, an archive containing this RAT, a password-protected archive, and a batch script to install the NetSupport client on the target system.
Batch scripts can also disable Windows error reporting and application compatibility, add remote control client executable files to the firewall’s list of licensed programs, add a running registry, or download shortcut files to the startup folder to maintain persistence. Hide files, delete Artefact, and execute the RAT. Researchers also found that malicious software regularly updates this script.
With the help of NetSupport Manager, an attacker can remotely access infected systems, transfer files, launch applications, obtain system location, and remotely retrieve directory and system information. The final JavaScript also downloads a text file containing a list of IP addresses that may be the infected system. Most of these IP addresses belong to the United States, Germany, and the Netherlands.