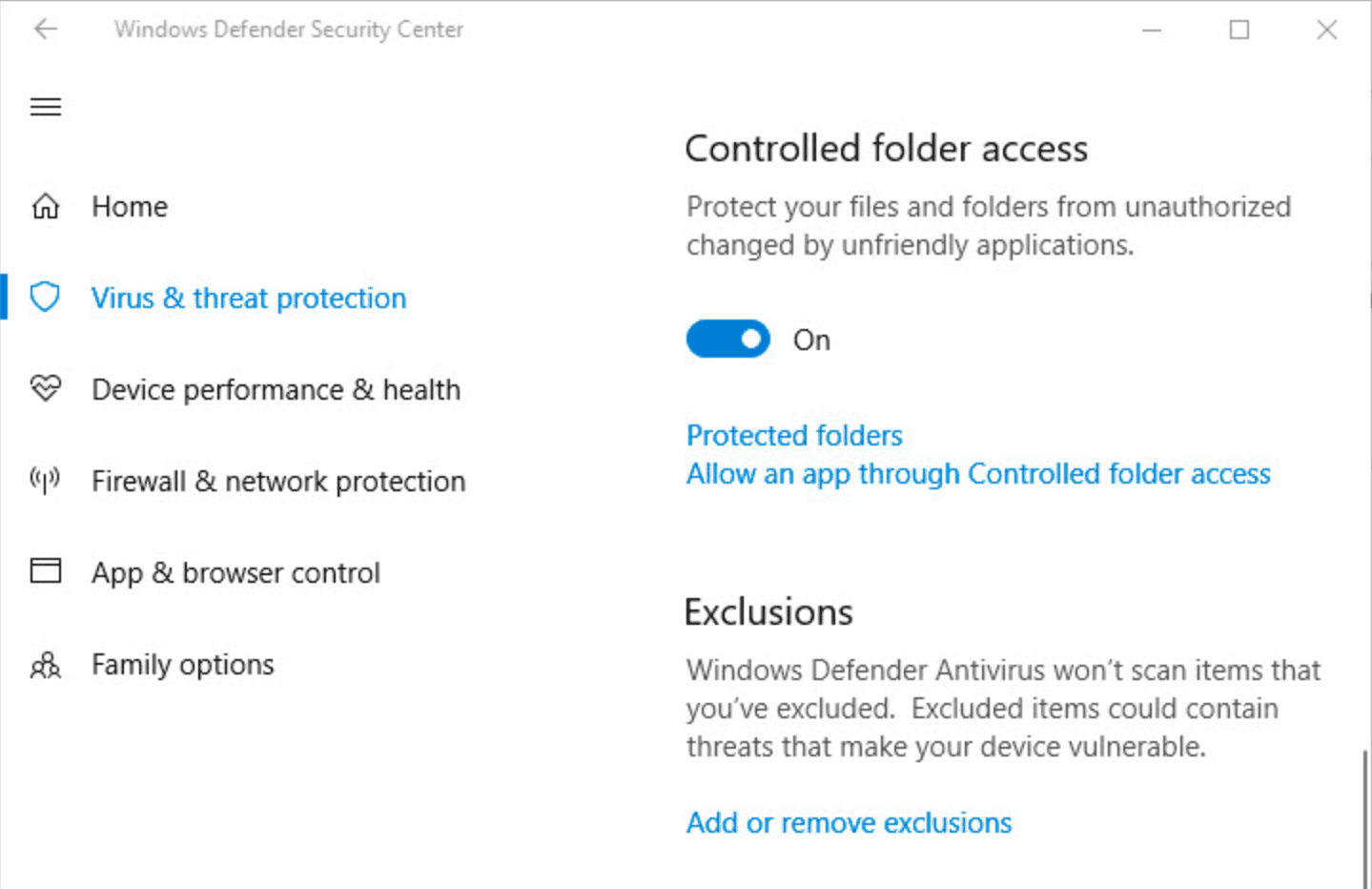
In October 2017, cybersecurity officers found a way to circumvent Controlled Folder Access (CFA), a built-in file protection feature in Windows 10 systems, that protects files on your computer from ransomware attacks. Users only need to select which files in the folder need to be protected, you can modify the read and write permissions of these folders to prevent unauthorized changes to the permissions of these folders.
However, Yago Jesus, a Spanish researcher, found that this feature whitelisted all Microsoft Office applications by default, which means that as long as it’s an office application, permissions on all folders can be changed. This presents ransomware with an opportunity to bypass CFA’s file-protection features by using OLE objects from Microsoft Office. He also released three examples. The first example can be used to cover the contents of other office files protected by the CFA after downloading the malicious office files sent by spam. You can also set the file password protection, copy and paste files, or even delete Files within the CFA protected folder. The second and third examples imitate that ransomware needs to pay a ransom for the CFA-protected folders and files to be locked for use again.
Yago Jesus reported the situation to Microsoft and did not attribute the vulnerability to a security breach in his email response from Microsoft, saying only that it would further improve the CFA’s capabilities. This also means that he will not get Microsoft rewards for reporting vulnerabilities.
Source: bleepingcomputer