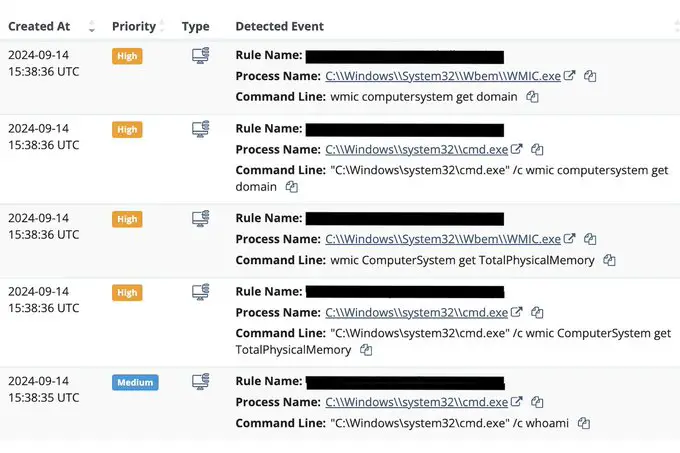
Attacker commands enumerating machine details | Image: Huntress
Recently, the cybersecurity company Huntress reported a new wave of cyberattacks targeting the widely-used Foundation Accounting Software, popular among contractors in the construction industry. Since September 14, attackers have been exploiting this software en masse, employing brute-force attacks and default credentials to gain access to victims’ accounts.
According to Huntress, the affected companies operate in sectors such as plumbing, heating, ventilation, air conditioning, concrete work, and other construction subfields. In every case, the Foundation was accessible via the internet, which allowed the attackers to infiltrate the system.
Experts explain that databases are often kept within internal networks and protected by firewalls or VPNs. However, Foundation Software offers remote connectivity through a mobile app, which leaves TCP port 4243 open to public access. This port is directly linked to the MSSQL server.
During the attack, hackers exploit the system’s administrator account in MSSQL, granting them full control over the server and its databases. The issue is further exacerbated by the presence of additional high-privilege accounts, in some instances, left with default passwords. These accounts enable attackers to access extended stored procedures in MSSQL, allowing them to execute operating system commands directly through SQL queries.
Huntress notes that scripts are being used to automate the attacks, as identical commands were executed across multiple servers within a short time frame. In one case, hackers made approximately 35,000 password-guessing attempts before successfully breaching the system and initiating command execution.
To date, Huntress has identified 33 publicly accessible hosts running Foundation, where default credentials had not been changed. Affected clients have been notified, and warnings have been issued to other companies using this software.
Organizations at risk are advised to change all passwords associated with the Foundation, disconnect the system from the internet, and deactivate vulnerable procedures to enhance security.
Related Posts:
- ScreenConnect Abuse: Hackers Leverage Remote Access Tool for Healthcare Intrusion
- Researchers to release SysAid CVE-2023-47246 exploit
- North Korean Hackers Exploit VPN Vulnerabilities to Breach Networks
- Fake Browser Updates Lead to Malicious BOINC Installations
