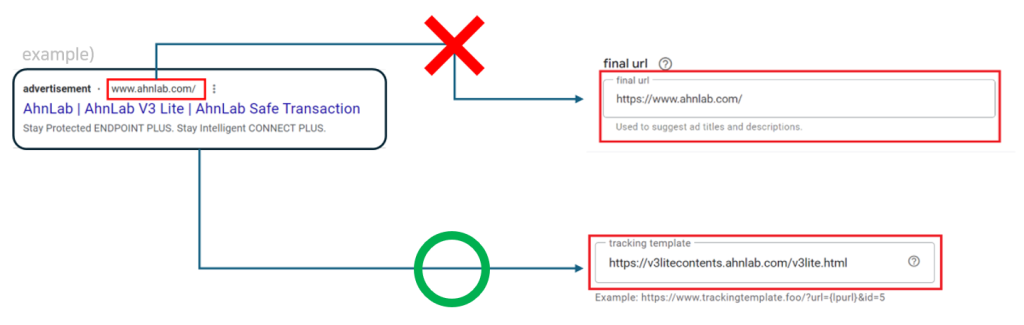
Redirection sequence upon clicking the ad
A new report released by AhnLab Security Intelligence Center (ASEC) uncovers a disturbing tactic hackers are using to spread malware: they’re leveraging Google Ads tracking features to redirect unsuspecting users to malicious websites.
Key Findings
- Hackers are creating fake ads for popular groupware software programs like Notion, Slack, Trello, and GoodNotes.
- These ads contain hidden tracking URLs that redirect users to download sites hosting malware instead of the intended software.
- The malware is designed to steal sensitive user information.
How the Attack Works

The hackers’ strategy is devious in its simplicity:
- Crafting Fake Ads: They create advertisements masquerading as popular productivity tools like Notion, Slack, Trello, and GoodNotes. These ads are designed to appear legitimate within Google search results.
- Malicious Redirects: The attackers embed hidden tracking URLs within these ads. When a user clicks, expecting a legitimate software download, they’re instead stealthily redirected to a malicious website.
- Mimicking Trusted Sites: These fraudulent websites cleverly mimic the appearance of official software download pages, further deceiving the victim.
- Malware Delivery: The “download” button delivers a payload of the Rhadamanthys infostealer malware, capable of stealthily exfiltrating sensitive user data.
A Growing Threat
This report highlights a trend of hackers exploiting legitimate advertising platforms to spread malware. Users must be hyper-vigilant, as even familiar services like Google Ads can be weaponized.
How to Protect Yourself
- Exercise extreme caution: Always verify a website’s address (URL) before downloading software. Download software directly from official developer websites.
- Use an updated antivirus and anti-malware solution: Invest in reputable security software that can detect and block suspicious downloads.
- Be wary of search engine results: Even top search results can be manipulated. Double-check any software vendor websites before interacting with them.
- Consider ad blockers: While not foolproof, ad blockers can reduce your exposure to potentially malicious advertisements.
The Bottom Line
Hackers are continually finding innovative ways to infiltrate our devices. This latest report underscores the importance for users and companies alike to be extra cautious with online activity, especially when it comes to software downloads. Remember, cybercriminals are counting on users to click first and think later.