Hackers use three malware simultaneously in cyber espionage against Ukraine
ESET, a security company based in Bratislava, Slovakia, recently released a 19-page technical analysis report detailing three types of malware that they are using simultaneously in cyber espionage against Ukrainian government agencies. Includes features of malware and techniques to circumvent security detection and how attackers spread them.
ESET pointed out in this report that they have been tracking the hackers since mid-2017 and can track their activities back to October 2015, even earlier. Although hackers do not seem to have a high level of skill or the ability to use zero-day vulnerabilities, they have successfully used social engineering to achieve the goal of spreading malware and have not been discovered for years.

The latest activity aimed at Ukrainian government agencies, who use three different .NET malware at their time – Quasar RAT, Sobaken (a Quasar-based RAT) and a custom RAT called “Vermin” Currently, targets are monitored, and data stolen from their systems.
According to its telemetry data, hackers use malicious spam as the primary source of communication for these three types of malware and have succeeded in using social engineering to lure targets to download and execute malware. In most cases, file names are written in Ukrainian and cover specific topics related to the target occupation.
In addition to using junk e-mail and basic social engineering techniques, hackers have used three more technical methods to increase the probability of success of their activities further.
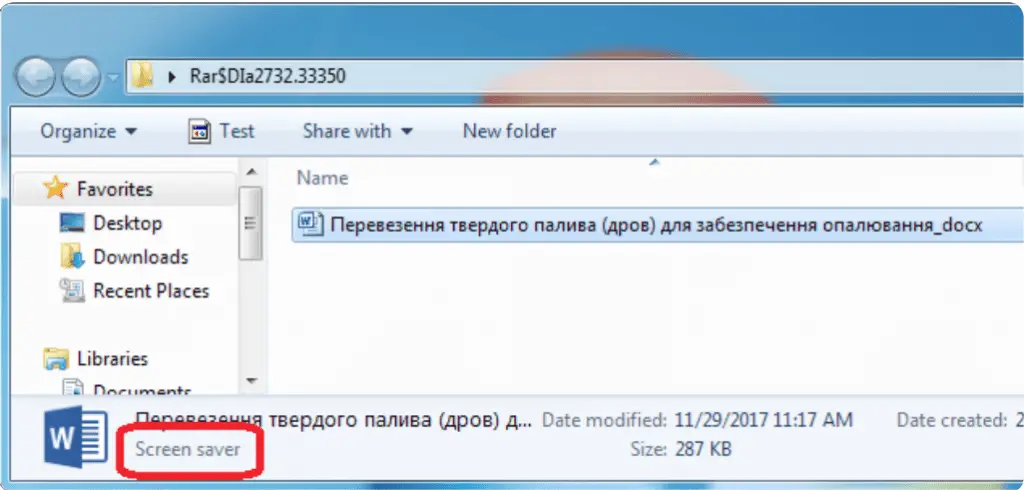
“Method #1: Email attachments using Unicode right-to-left override in their filenames to obscure their
real extension. These are actually executable files using Word, Excel, PowerPoint or Acrobat Reader
icons to appear more trustworthy.Method #2: Email attachments disguised as RAR self-extracting archives.
Method #3: Word document plus CVE-2017-0199 exploit. This vulnerability is triggered when the victim
opens a specially crafted Word document. The Word process issues an HTTP request for an HTA file that
contains a malicious script, located on a remote server. The malicious script will then be executed by
mshta.exe. The first public information about this vulnerability appeared in April 2017 and Microsoft fixed
it by issuing Security updates for all versions of Windows and Office.”
Although the hackers have been active for at least three years, their attacks have not caused much public attention, which may be open sourced before they develop their malware (Vermin).
Using multiple malware in the same event may indicate that the hacker is composed of various teams and is developing malware independently, while using much malware at the same time may be because they are testing malware and some attack techniques.
In any case, in the past three years, the hackers have indeed developed a variety of malware and successfully implemented the attack using some of the most fundamental technologies (such as social engineering). This fully demonstrates how critical is the personal security awareness and related knowledge in the computer network security protection system.
Read the full report:
QUASAR, SOBAKEN AND VERMIN: A deeper look into an ongoing espionage campaign





