Image: Rapid7
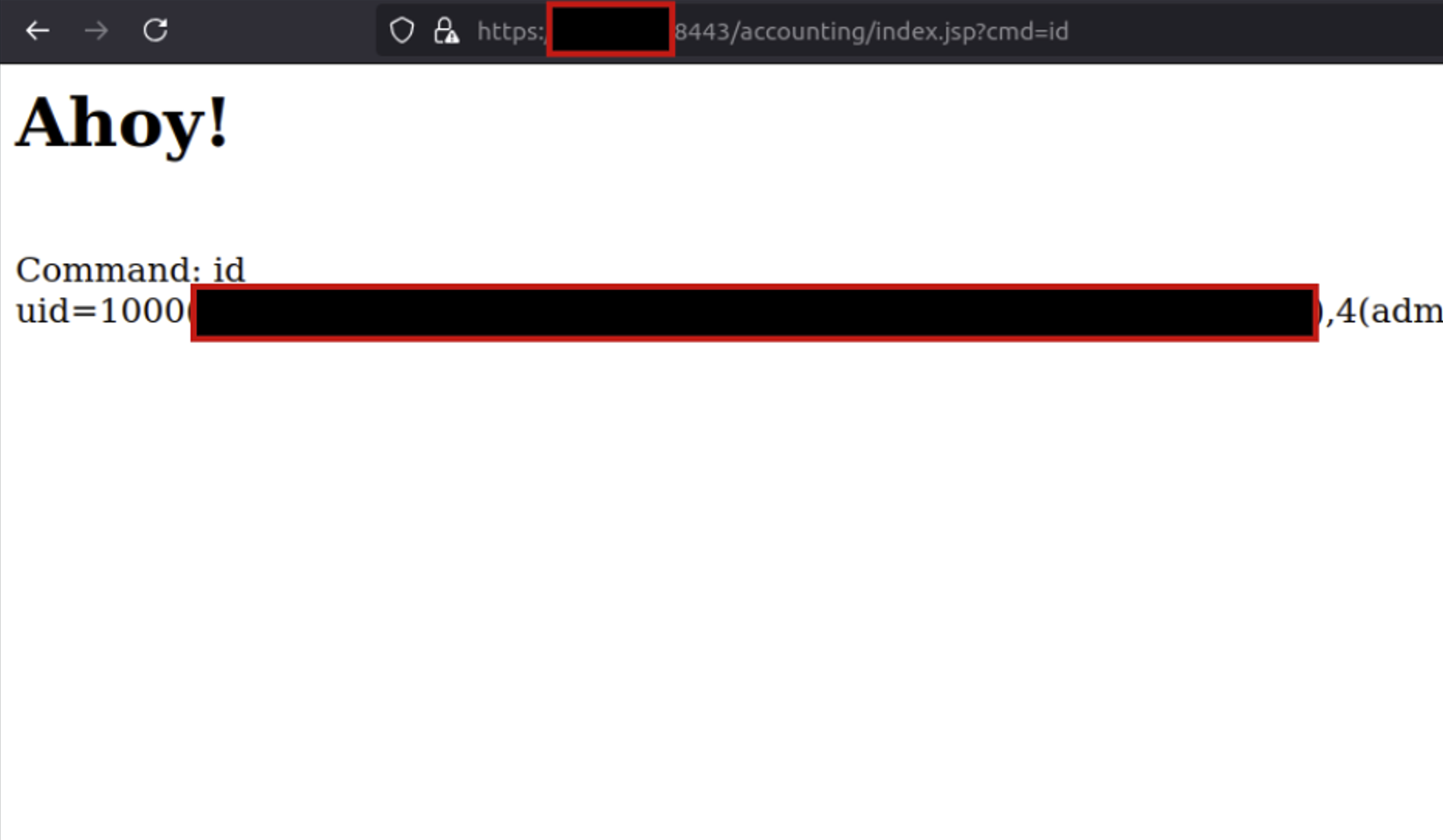
According to a report from Imperva, over 25,000 malicious requests targeting 4,000 unique sites have been detected since the CVE-2024-45195 vulnerability in Apache OFBiz was disclosed. These attacks, primarily targeting the financial services industry (FSI) and business sectors, have relied on malicious bots and custom exploitation tools written in Go to probe for and exploit vulnerable systems. Attackers seek to deploy malware, steal sensitive data, or disrupt business operations by exploiting this flaw.
CVE-2024-45195 (CVSS score: 7.5) allows attackers to bypass authorization checks and execute arbitrary code on the server, even without valid credentials.
Alarmingly, CVE-2024-45195 is a bypass for a series of previously addressed vulnerabilities (CVE-2024-32113, CVE-2024-36104, and CVE-2024-38856), highlighting the persistent nature of this security issue. Shockingly, CVE-2024-32113 and CVE-2024-38856 have already been actively exploited in the wild, with the former used to deploy the notorious Mirai botnet malware.
All versions of Apache OFBiz before 18.12.16 are affected. The latest patch introduces critical changes, including proper validation to ensure that view authorization is correctly enforced. The patch also blocks unauthorized users from exploiting the controller-view desynchronization flaw, providing much-needed protection for enterprise systems. Organizations using OFBiz are strongly urged to update to the latest version immediately to mitigate this critical risk
In addition to addressing CVE-2024-45195, Apache OFBiz version 18.12.16 also fixes a critical server-side request forgery (SSRF) vulnerability (CVE-2024-45507, CVSS score: 9.8) that could lead to unauthorized access and system compromise.
Related Posts:
- Actively Exploited Apache OFBiz Flaw Triggers Urgent Security Alert
- CVE-2024-38856: Critical Apache OFBiz Flaw Opens Door to Unauthorized Code Execution
- PoC Exploit Released for Apache OFBiz Remote Code Execution Flaw (CVE-2024-38856)
- CISA Warns of Actively Exploited Apache OFBiz CVE-2024-38856 Vulnerability, PoC Available
- Multi security vulnerabilities was found on Apache OFBiz
- Malicious apps change their name to come back on the Play Store
- Vulnerable Microsoft SQL Server are being targeted by hackers
