Image: Group-IB
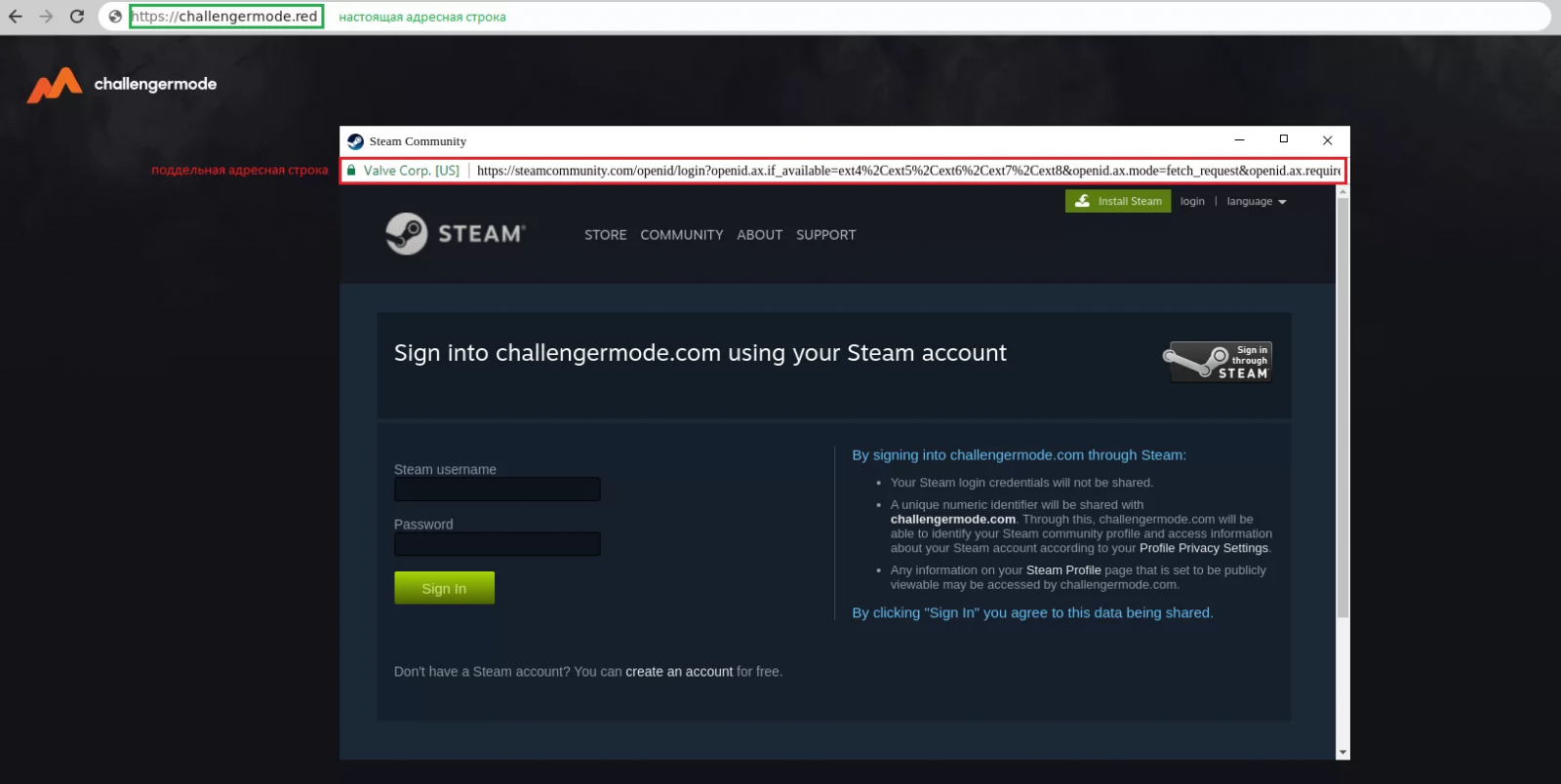
Hackers impersonate some well-known gaming tournaments to invite targeted Steam accounts to participate in so-called tournaments. The hacker’s own website imitates the websites of various competitions, and players must log in to their Steam accounts if they want to sign up.

When you click to log in, the website will pop up the official Steam login address (in fact, it is fake), which is nested in your browser windows by hackers using iframes.
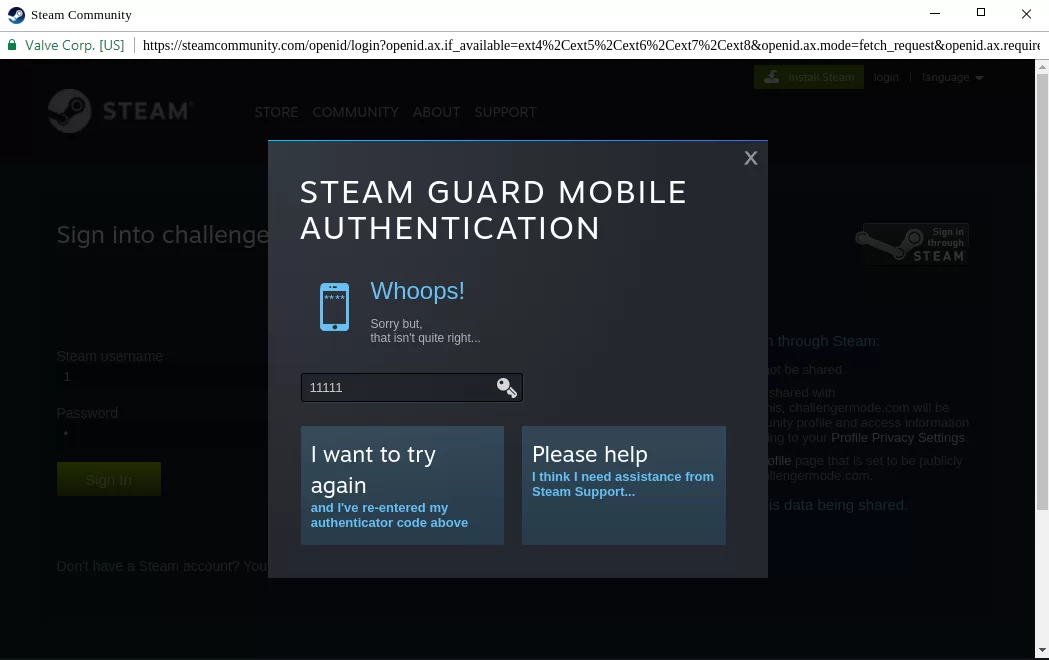
Once the player enters their credentials, a new form prompts them to enter the 2FA code. After logging in, the player must also provide a 2FA verification code. Once the account authority is provided, the hacker will control it, and then the information will be changed so that the real player cannot control his account.
Browser-in-the-browser phishing differs significantly from traditional phishing:
| Traditional phishing | Browser-in-the-browser phishing |
|---|---|
| Displays a phishing data entry form or redirects users to it. | Displays a data entry form in a pop-up browser window. |
| The address bar displays a URL that differs from the legitimate one. It is therefore obvious to users that entering confidential information on this website is not safe. | The address bar contains the URL of a third-party website that the victim wants to visit. The URL in the pop-up window is identical to the legitimate one. |
| The phishing resource cannot have an SSL certificate. | The fake window always displays an SSL certificate lock symbol. |