SafeBreach has engineered the first entirely undetectable cloud-based cryptocurrency miner, exploiting Microsoft Azure’s automation service without any incurred expenses. There are three methods for initiating the miner, one of which can operate within an external environment while remaining invisible to monitoring systems.
SafeBreach has observed that the miner is of significant relevance not only to the cryptocurrency realm but also could have serious implications across a broader spectrum of applications, as the disclosed methods are adaptable to any tasks that require code execution on the Azure platform.
The primary objective of the research was to identify an ideal cryptominer that would ensure unlimited access to computing resources, demand minimal maintenance, be cost-free, and most crucially, be imperceptible. This opportunity is provided by the Microsoft Azure Automation service, which automates the creation, deployment, monitoring, and maintenance of resources in Azure.

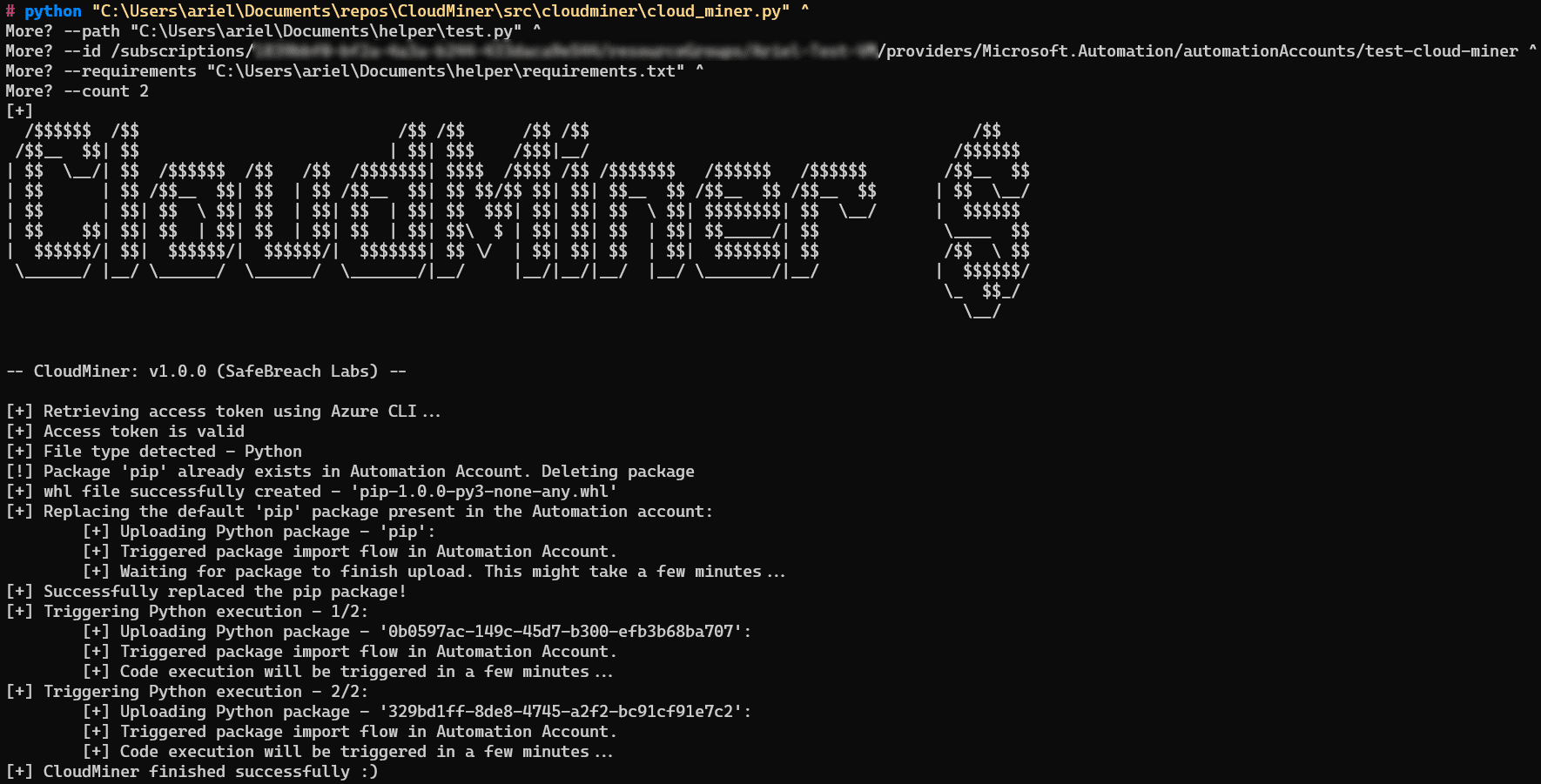
A key discovery was a flaw in the Azure cost calculator that allowed for an unlimited number of operations to be performed without charge. Although Microsoft has rectified this vulnerability, SafeBreach has showcased alternative methods. One involves creating a test mining job, causing it to fail, and then establishing a dummy test job, thereby concealing code execution within Azure.
Malefactors could exploit these methods by creating a reverse connection to an external server and connecting to an automation endpoint to achieve their objectives. It was also found that code execution could be facilitated through the Azure Automation function, which allows for the uploading of custom Python packages. This presents a pathway for the insertion of malicious code under the guise of legitimate packages, such as “pip”.
As a proof of concept, SafeBreach introduced CloudMiner—a tool designed to extract free computational power from the Azure Automation service. In response to the disclosure, Microsoft has indicated that this method is an integral part of the service’s operation and can be utilized without fees.
While the study is limited to the use of Azure Automation for cryptocurrency mining, SafeBreach cautions that the same techniques might be employed for other purposes. Organizations should vigilantly monitor every resource and action within their environment to thwart such threats. SafeBreach advises organizations to educate themselves and monitor execution metrics that may signify the unethical use of resources.