Hakuin
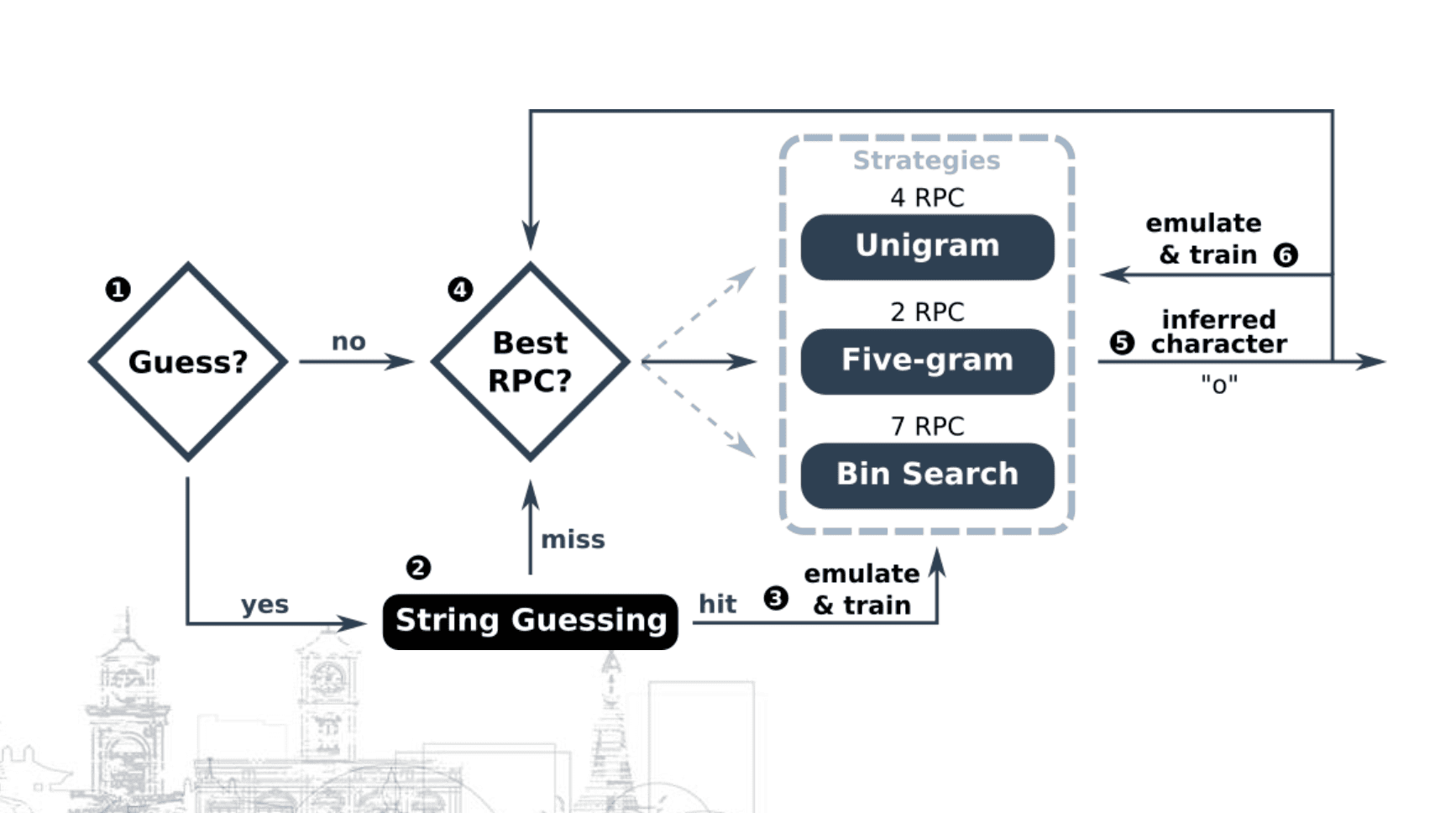
Hakuin is a Blind SQL Injection (BSQLI) inference optimization and automation framework written in Python 3. It abstracts away the inference logic and allows users to easily and efficiently extract textual data in databases (DB) from vulnerable web applications. To speed up the process, Hakuin uses pre-trained language models for DB schemas and adaptive language models in combination with opportunistic string guessing for DB content.

Hakuin has been presented at academic and industrial conferences:
Also, make sure to read our paper or see the slides.
Install
To install Hakuin, simply run:
Developers should install the package locally and set the -e flag for editable mode:
cd hakuin
pip3 install -e .
Examples
Once you identify a BSQLI vulnerability, you need to tell Hakuin how to inject its queries. To do this, derive a class from the Requester and override the request method. Also, the method must determine whether the query is resolved to True or False.
Example 1 – Query Parameter Injection with Status-based Inference
Example 2 – Header Injection with Content-based Inference
To start inferring data, use the Extractor class. It requires a DBMS object to construct queries and a Requester object to inject them. Currently, Hakuin supports SQLite and MySQL DBMSs but will soon include more options. If you wish to support another DBMS, implement the DBMS interface defined in hakuin/dbms/DBMS.py.
Example 1 – Inferring SQLite DBs
Example 2 – Inferring MySQL DBs
Now that everything is set, you can start inferring DB schemas.
Example 1 – Inferring DB Schemas
Example 2 – Inferring DB Schemas with Metadata
Example 3 – Inferring only Table/Column Names
Once you know the schema, you can extract the actual content.
Example 1 – Inferring Textual Columns
Copyright (c) 2023 Jakub Pruzinec
Source: https://github.com/pruzko/