HBSQLI: Automated Tester For Header-Based Blind SQL Injection
HBSQLI is an automated command-line tool for performing Header Based Blind SQL injection attacks on web applications. It automates the process of detecting Header Based Blind SQL injection vulnerabilities, making it easier for security researchers, penetration testers & bug bounty hunters to test the security of web applications.
Installation
Install HBSQLI with the following steps:
$ git clone https://github.com/SAPT01/HBSQLI.git
$ cd HBSQLI
$ pip3 install -r requirements.txt
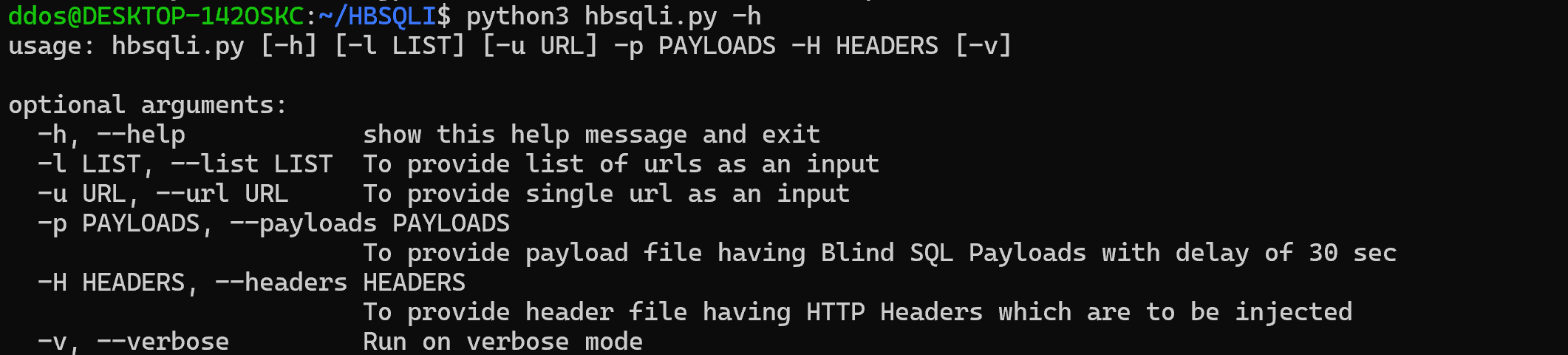
Use

Modes
There are basically two modes in this, verbose which will show you all the process which is happening and show your the status of each test done and non-verbose, which will just print the vulnerable ones on the screen. To initiate the verbose mode just add -v in your command
Notes
-
You can use the provided payload file or use a custom payload file, just remember that delay in each payload in the payload file should be set to 30 seconds.
-
You can use the provided headers file or even some more custom header in that file itself according to your need.
Source: https://github.com/SAPT01/