hcltm v0.1.6 releases: Threat Modeling with HCL
hcltm
Threat Modeling with HCL

Overview
There are many different ways in which a threat model can be documented. From a simple text file to more in-depth word documents, to fully instrumented threat models in a centralised solution. Two of the most valuable attributes of a threat model are being able to clearly document the threats and to be able to drive valuable change.
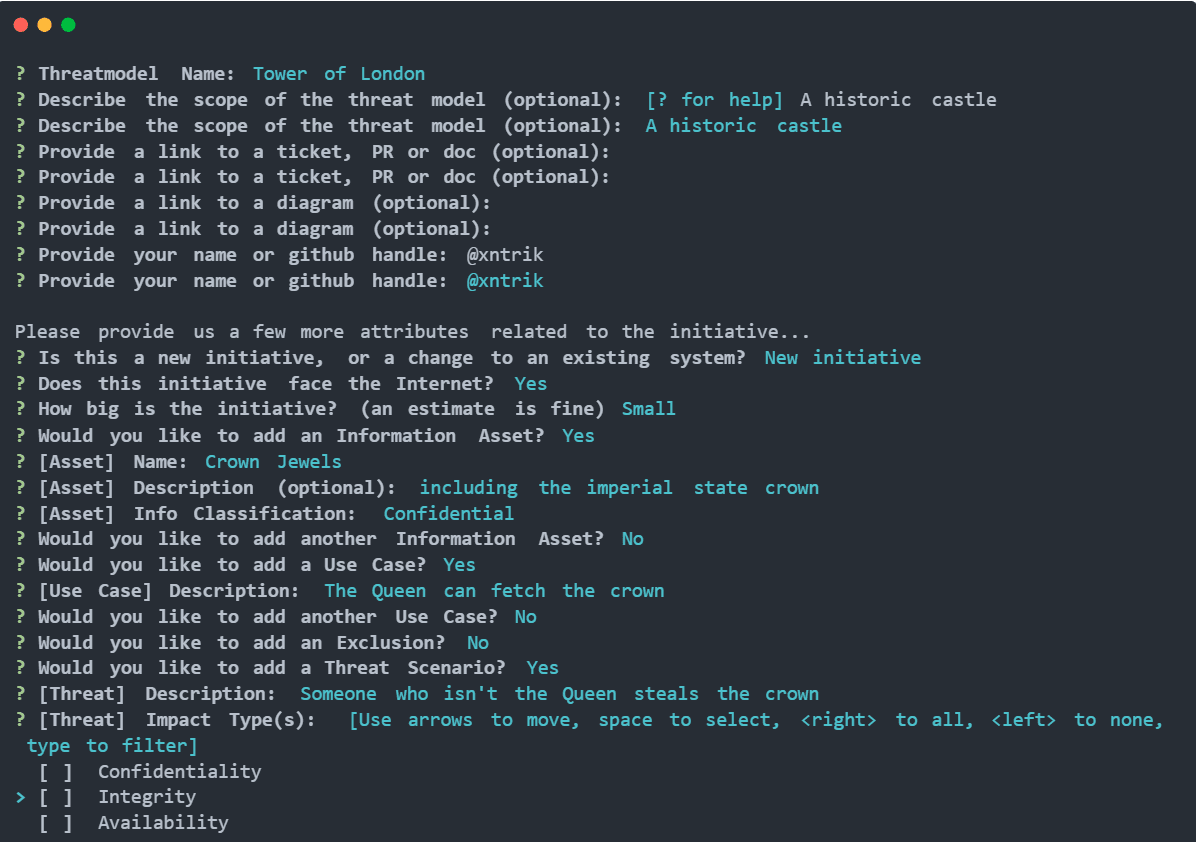
hcltm aims to provide a DevOps-first approach to documenting a system threat model by focusing on the following goals:
- Simple text-file format
- Simple cli-driven user experience
- Integration into version control systems (VCS)
This repository is the home of the hcltm cli software. The hcltm spec is based on HCL2, HashiCorp’s Configuration Language, which aims to be “pleasant to read and write for humans, and a JSON-based variant that is easier for machines to generate and parse“. Combining the hcltm cli software and the hcltm spec allows practitioners to define a system threat model in HCL, for example:
Why HCL?
HCL is the primary configuration language used in the products by HashiCorp, in-particularly, Terraform – their open-source Infrastructure-as-Code software. I worked at HashiCorp for a while and the language really grew on me, plus, if DevOps and Software engineers are using the language, then simplifying how they document threat models aligns with hcltm‘s goals.
You can use hcltm with JSON, but you lose some of the features. For more, see the examples/ folder.
Changelog v0.1.6
Features
- Parse for legacy DFDs and shift into the new format #78 (xntrik)
- Adding contraint checks for old dfd blocks #29 #78 (xntrik)
- list command now handles number of DFD in output #29 #78 (xntrik)
- Multiple DFDs per TM are now supported #29 #78 (xntrik)
- TMs now support additiona_attribute blocks #71 #78 (xntrik)
Documentation
Tests
- updated tests for DOT output #78 (xntrik)
- for the multi dfd contstraint check #29 #78 (xntrik)
- for the multi dfd contstraint check – forgot to add the test file #29 #78 (xntrik)
- Forgot to add the test file for #29 #78 (xntrik)
Continuous Integration
- working on getting docker built on gh actions #78 (xntrik)
- adding qemu #78 (xntrik)
- Updating release to include docker building for GHCR #78 (xntrik)
- updating golang #78 (xntrik)
- Updated pre-release to test-build docker build #78 (xntrik)
- Tweaking pre-release action #79 (xntrik)
- Adding env flags to pre-release action #80 (xntrik)
Chores
- After a go mod tidy #78 (xntrik)
- updating vulnerable aws-sdk-go https://github.com/xntrik/hcltm/security/dependabot/2 #78 (xntrik)
- bumping version in prep for 0.1.6 – still need to tidy other ver #78 (xntrik)
- go mod tidy #78 (xntrik)
- go mod tidy #78 (xntrik)
- Updated 0.1.5 refs to 0.1.6 #81 (xntrik)
Install & Use
Copyright (c) 2021 Christian Frichot





