Overlaps in TTPs, tools, and infrastructure between Head Mare and Twelve | Image: Kaspersky Labs
In a series of attacks targeting Russian companies in September 2024, cybersecurity researchers uncovered evidence of collaboration between two hacktivist groups: Head Mare and Twelve. A report by Kaspersky Labs reveals that Head Mare has been relying on tools previously associated with Twelve, and has also utilized command-and-control (C2) servers exclusively linked to Twelve. This suggests a potential alliance and coordinated campaigns between the two groups.
The attackers are continuously refining their methods, incorporating both familiar tools from past Head Mare incidents and new PowerShell-based tools. The report analyzes the software and techniques observed in recent Head Mare attacks and their overlap with Twelve’s activities, focusing on Head Mare’s TTPs and their evolution, with notes on commonalities with Twelve’s TTPs.
Head Mare’s toolkit includes a mix of publicly available tools, open-source software, and leaked proprietary tools. Some of the tools, like mimikatz, ADRecon, secretsdump, ProcDump, Localtonet, revsocks, ngrok, cloudflared, Gost, fscan, SoftPerfect Network Scanner, mRemoteNG, PSExec, smbexec, wmiexec, LockBit 3.0, and Babuk, were mentioned in a previous report on Head Mare.
However, the attackers have also introduced new tools into their arsenal. Notably, they used the Cobint backdoor for remote access to domain controllers, a tool previously observed only in Twelve’s attacks on Russian companies. “This is an interesting fact, suggesting that Twelve and Head Mare may be sharing tools,” the report states. In addition to Cobint, the attackers used their own PhantomJitter backdoor, installed on servers for remote command execution. This tool appeared in the group’s arsenal in August 2024. The attackers also employed a tool for remote command execution on a business automation platform server, showcasing their flexibility and adaptability.
While previous Head Mare attacks relied solely on phishing emails with malicious attachments, the attackers now also infiltrate victims’ infrastructure through compromised contractors with access to business automation platforms and RDP connections. This confirms the trend of hacktivists exploiting trusted relationships. The attackers also exploited software vulnerabilities, including CVE-2023-38831 in WinRAR and CVE-2021-26855 (ProxyLogon) in Microsoft Exchange servers. Despite being patched in 2021, the ProxyLogon vulnerability is still exploitable due to organizations using outdated operating systems and software.
The attackers have also changed their persistence methods. Instead of creating scheduled tasks, they now create new privileged local users on a business automation platform server. They use these accounts to connect to the server via RDP to transfer and execute tools interactively. Additionally, they install traffic tunneling tools like Localtonet for persistent access to the target host. Localtonet is made persistent with the help of Non-Sucking Service Manager (NSSM), which allows running any application as a Windows service and monitoring/restarting it if it fails. These tools help the malicious actors maintain continuous access to the infected host.
Head Mare continues to employ masquerading techniques, naming utility executables like standard operating system files. Examples include renaming the cloud storage sync tool rclone to “C:\ProgramData\wusa.exe,” PhantomJitter to “C:\Windows\System32\inetsrv\calc.exe,” cloudflared to “C:\Windows\System32\winuac.exe,” and Gost to “C:\Windows\System32\winsw.exe”. In one incident, cmd.exe was renamed to log.exe and launched from C:\Users[username]\log.exe. The attackers also remove services and files they created and clear event logs to evade detection.
After exploiting the business automation platform server, attackers download and install the PhantomJitter backdoor. The backdoor was downloaded from URLs like http[:]//45.87.246[.]34:443/calc.exe and http[:]//185.158.248[.]107:443/calc.exe, and saved as c.exe in the local directory. Upon launch, it connects to the C2 server, allowing the operator to execute commands on the compromised host. In addition to PhantomJitter, the attackers used Cobint, with its payload connecting to the C2 server at 360nvidia[.]com, which resolves to the IP address 45.156.27[.]115.
To gain remote access to the compromised infrastructure, the attackers use a custom PowerShell script named proxy.ps1 to install and configure cloudflared and Gost. Gost is a lightweight proxy utility offering various network routing and traffic hiding capabilities, supporting multiple protocols and creating secure communication channels.
Cloudflared tunnels traffic through the Cloudflare network, establishing a secure connection to an attacker-controlled Cloudflare server and bypassing network restrictions. The proxy.ps1 script can also download archives from URLs and extract them to a temporary folder. The script defines constants for filenames, installing cloudflared and Gost with names mimicking standard Windows services. It uses the GetTempFileName function to obtain temporary file paths. The script installs the Gost executable file as a service and passes necessary settings to it. If the -t key is passed to the script, it installs and configures cloudflared. The script can also remove the artifacts they leave behind, and stop and uninstall the cloudflared and Gost services.
In one incident, the attackers downloaded cloudflared and Gost from the server 45[.]156[.]21[.]148, previously seen in Head Mare attacks. Besides cloudflared and Gost, the attackers used cloud tunnels like ngrok and Localtonet. Localtonet is a reverse proxy server providing internet access to local services. The attackers launched it as a service using NSSM, downloading both tools from the official Localtonet website.
The attackers used common system reconnaissance tools like quuser.exe, tasklist.exe, and netstat.exe on local hosts. They primarily used fscan and SoftPerfect Network Scanner for local network reconnaissance, along with ADRecon, a tool for gathering information from Active Directory. ADRecon is a PowerShell script not previously observed in the group’s arsenal. The attackers also used ADRecon to study the Active Directory domain, including computers, accounts, groups, and trust relationships between domains.
The attackers exploited previously compromised accounts and created privileged local accounts, particularly when exploiting the business automation software server. The business automation software allows running a child command prompt process with privileges corresponding to the program’s privileges. Since this software typically has administrator privileges, the child process also becomes privileged, which the attackers exploited to create a privileged local account.
The attackers launched the Windows command interpreter on the business automation platform server using a command that downloads and executes the vivo.txt file. Although the vivo.txt file was not obtained, it is suspected to have opened a reverse shell, used to create two files: c:\programdata\microsoftdrive\mcdrive.vbs and c:\programdata\microsoftdrive\mcdrive.ps1. The attackers then added an autorun entry to execute mcdrive.vbs with the interpreter wscript.exe. The VBS file is an obfuscated Visual Basic script that executes an obfuscated command line to read and execute the C:\ProgramData\MicrosoftDrive\mcdrive.ps1 file through the PowerShell interpreter. This file is a CobInt loader, previously seen only in Twelve’s arsenal.
The investigation also identified tools for obtaining credentials, including the publicly available mimikatz utility, secretsdump, and ProcDump. A new Go-based sample named update.exe was discovered, enabling the dumping of the ntds.dit file and the SYSTEM/SECURITY registry hive using ntdsutil.exe.
The attackers used RDP to connect to systems, including with privileged accounts, and connected to NAS servers via SSH. They also used tools like mRemoteNG, smbexec, wmiexec, PAExec, and PsExec for remote host communication.
Another new tool in Head Mare’s arsenal was a script running wusa.exe, which was actually the rclone.exe utility. Rclone is an open-source project for copying and synchronizing files between storages of different types, making it convenient for data transfer. The script takes a file as input, containing a list of hosts, and runs rclone.exe to transfer files from the device to an SFTP server through a SOCKS proxy. The attackers exfiltrated files from specific directories or files matching specified extension templates.
As in previous attacks, the attackers encrypted data using variants of LockBit 3.0 (for Windows systems) and Babuk (for NAS devices). The LockBit file was found at paths like C:\Users\{username}\Desktop\locker.exe and C:\Windows\SYSVOL\Intel\locker.exe.
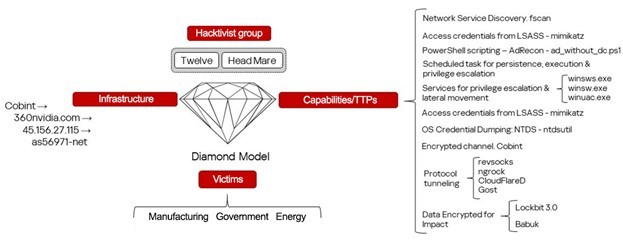
These attacks are attributed to Head Mare based on previously seen IP addresses and malware like PhantomJitter. However, the presence of Twelve’s tools like CobInt suggests collaboration. Analysis using the Diamond Model framework revealed overlaps in infrastructure (C2s), TTPs, Cobint malware, and victim choices, indicating that these groups are likely working together, exchanging access to command-and-control servers and various tools.