honssh v1.1.0 released: log all SSH communications between a client and server
honssh
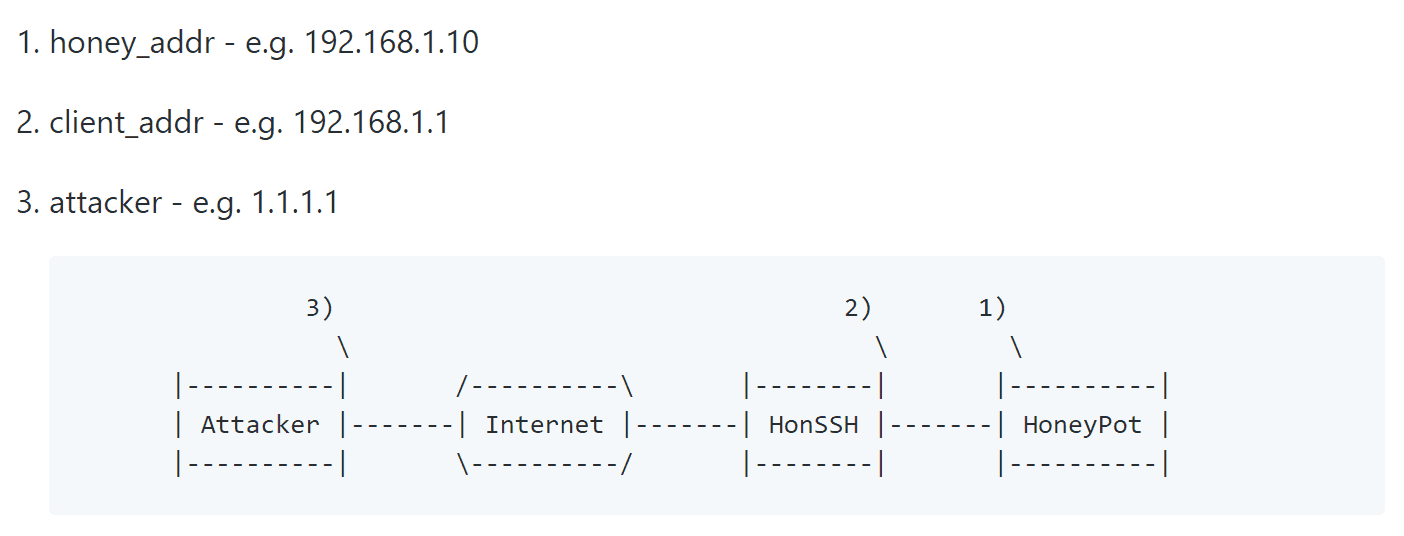
HonSSH is designed to be used in conjunction with a high interaction honeypot. HonSSH sits between the attacker and the honeypot and creates two separate SSH connections.
Features
- Captures all connection attempts to a text file, database or email alerts.
- When an attacker sends a password guess, HonSSH can automatically replace their attempt with the correct password (spoof_login option). This allows them to log in with any password but confuses them when they try to sudo with the same password.
- All interaction is captured into a TTY log (thanks to Kippo) that can be replayed using the playlog utility included from Kippo.
- A text based summary of an attackers session is captured in a text file.
- Sessions can be viewed or hijacked in real time (again thanks to Kippo) using the management telnet interface.
- Downloads a copy of all files transferred through wget or scp.
- Can use docker to spin up new honeypots and reuse them on ip basis.
- Saves all modifications made to the docker container by using filesystem watcher.
- Advanced networking feature to spoof attackers IP addresses between HonSSH and the honeypot.
- Application hooks to integrate your own output scripts.
Changelog v1.1.0
- Merge pull request #117 from tnich/exec_bug_fix
- Fixing config parsing of disable_exec
Install
- Using a single machine: static honeypot
- Using Docker: docker honeypot
Usage
Copyright (c) 2016 Thomas Nicholson <tnnich@googlemail.com>
All rights reserved.
Source: https://github.com/tnich/





