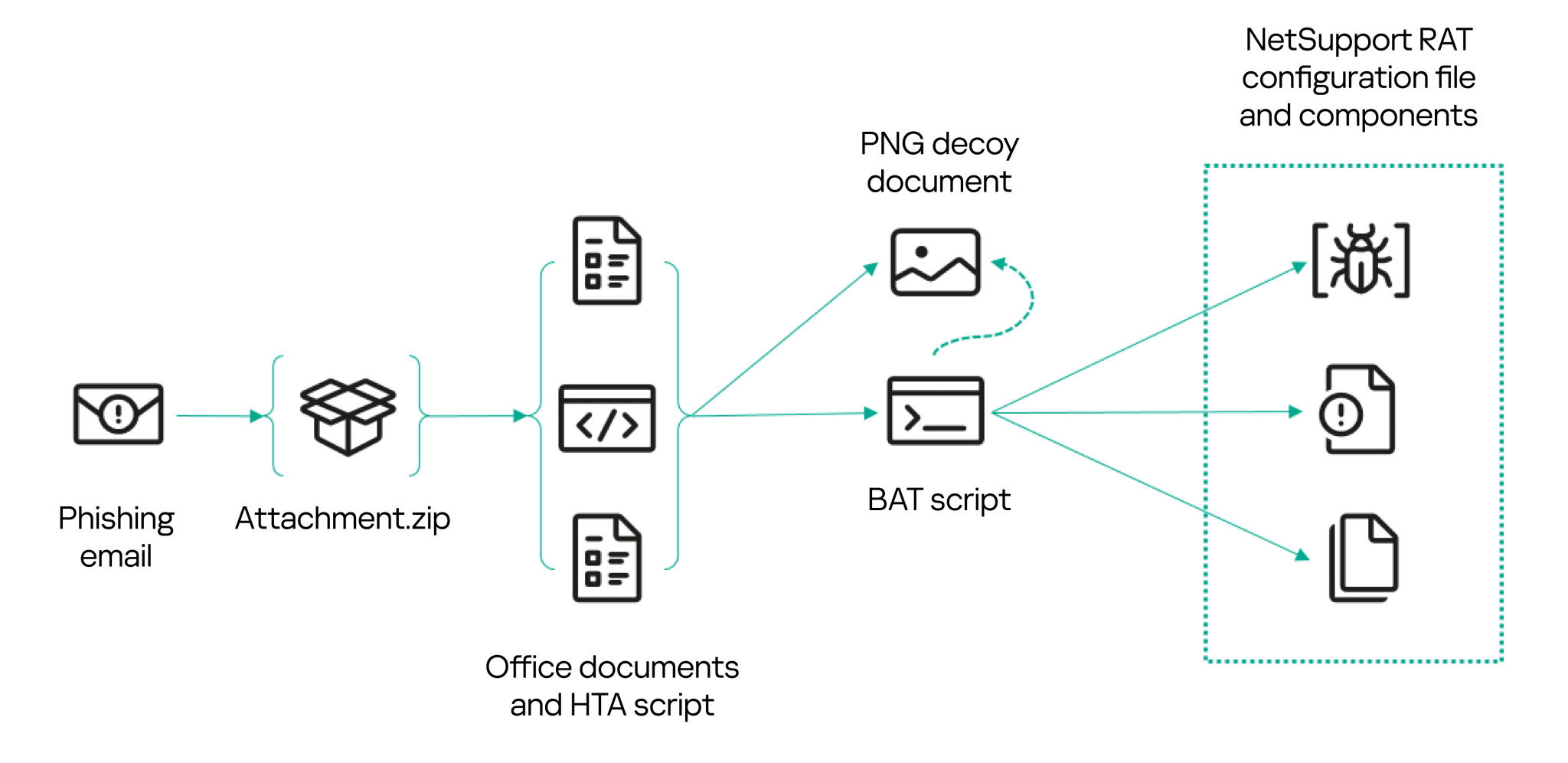
Version A infection chain | Image: Kaspersky Labs
In a detailed report by Kaspersky Labs, the Horns&Hooves campaign emerges as a notable example of cybercriminal ingenuity, leveraging dual RAT payloads—NetSupport RAT and BurnsRAT—to compromise systems across various sectors. The campaign, named after a fictional fraudulent organization in the Soviet satirical novel The Golden Calf, has primarily targeted individuals, retailers, and service businesses in Russia since its inception in March 2023.
Malicious email attachments have taken the form of ZIP archives containing JScript files camouflaged as business documents, such as “Request for proposals and prices from LLC <company>” or “Purchase request…”. These attachments often included decoy documents—sometimes as unconventional as PNG images, a tactic used to embed and deliver payloads without arousing suspicion.
Kaspersky Labs notes, “PNG images make convenient containers because they continue to display correctly even after the payload is added.”
The primary payloads of the campaign are the legitimate remote administration tool NetSupport Manager (NSM), rebranded as NetSupport RAT, and a custom variant dubbed BurnsRAT. These tools provide attackers with extensive control over compromised systems, leveraging their inherent legitimacy to evade detection.
NetSupport RAT, a known favorite of cybergangs due to its versatility, is deployed using clever infection chains. Scripts downloaded BAT files or PowerShell scripts that installed NetSupport components like client32.exe, configured registry entries for persistence, and connected to command-and-control servers. “When NetSupport RAT is run, it establishes a connection to one of the attackers’ servers,” the report states.
BurnsRAT, a lesser-known but equally dangerous tool, was distributed alongside or instead of NetSupport RAT in some instances. This variant exploited DLL side-loading techniques to hijack legitimate processes. Its payloads included utilities for remote desktop manipulation, data theft, and ransomware installation.
“The RMS build distributed by the attackers is also called BurnsRAT,” highlighting its dual-purpose capability to facilitate remote access and act as a launchpad for further attacks.
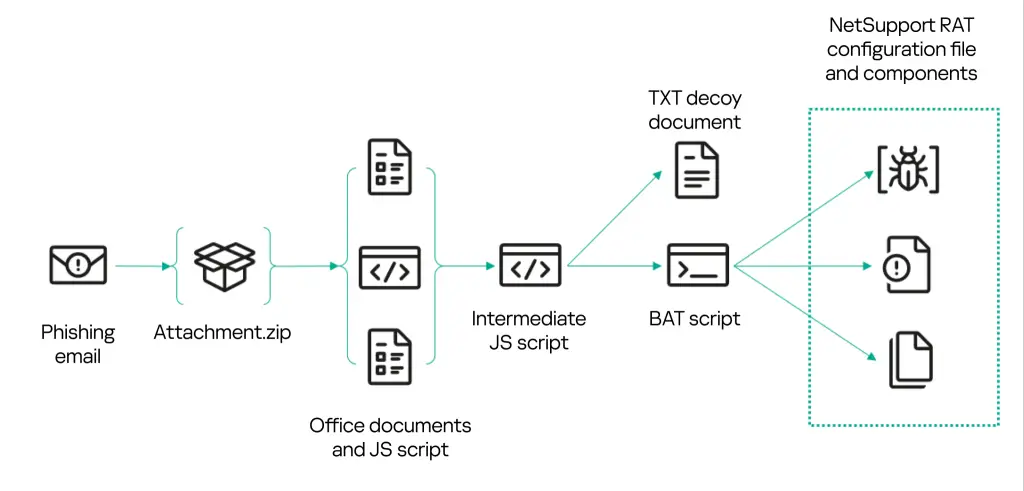
The Horns&Hooves campaign demonstrates adaptability in its infection chains, with multiple versions of the scripts observed over time. Earlier iterations relied on HTA files, while later versions adopted JScript with embedded payloads.
Intriguingly, the Horns&Hooves campaign bears a resemblance to operations linked to TA569, also known as Mustard Tempest. Kaspersky Labs found that the configuration files used in Horns&Hooves were nearly identical to those previously attributed to TA569, reinforcing suspicions of a shared origin.
The report adds, “The fact that the values match indicates that the attackers use the same security key to access the NetSupport client.”
Horns&Hooves exemplifies the growing trend of leveraging legitimate tools for malicious purposes. By disguising malware as credible software, attackers complicate detection and response efforts.
Cybersecurity teams must adopt multi-layered defenses, including robust email filtering, behavioral analysis of software, and regular patch management. Awareness of campaigns like Horns&Hooves is crucial in countering evolving threats.
Related Posts:
- Hackers are trying to install NetSupport Remote Access Tool on victim machine through Fake Software Update
- Cisco Talos Warns of Stealthy NetSupport RAT Campaigns
- NetSupport RAT Wielded in Escalating Cyber Attacks: Educational Institutions, Government Agencies, and Service Businesses at Risk
- Unveiling the NetSupport Threat: McAfee Researchers Delve into the Malware’s Tactics
- PhantomBlu Campaign Unleashes Stealthy Attack – Old RAT, Dangerous New Tricks