IAM Vulnerable
Use Terraform to create your own vulnerable by design the AWS IAM privilege escalation playground.
IAM Vulnerable uses the Terraform binary and your AWS credentials to deploy over 250 IAM resources into your selected AWS account. Within minutes, you can start learning how to identify and exploit vulnerable IAM configurations that allow for privilege escalation.

What resources were just created?
The Terraform binary just used your default AWS account profile credentials to create:
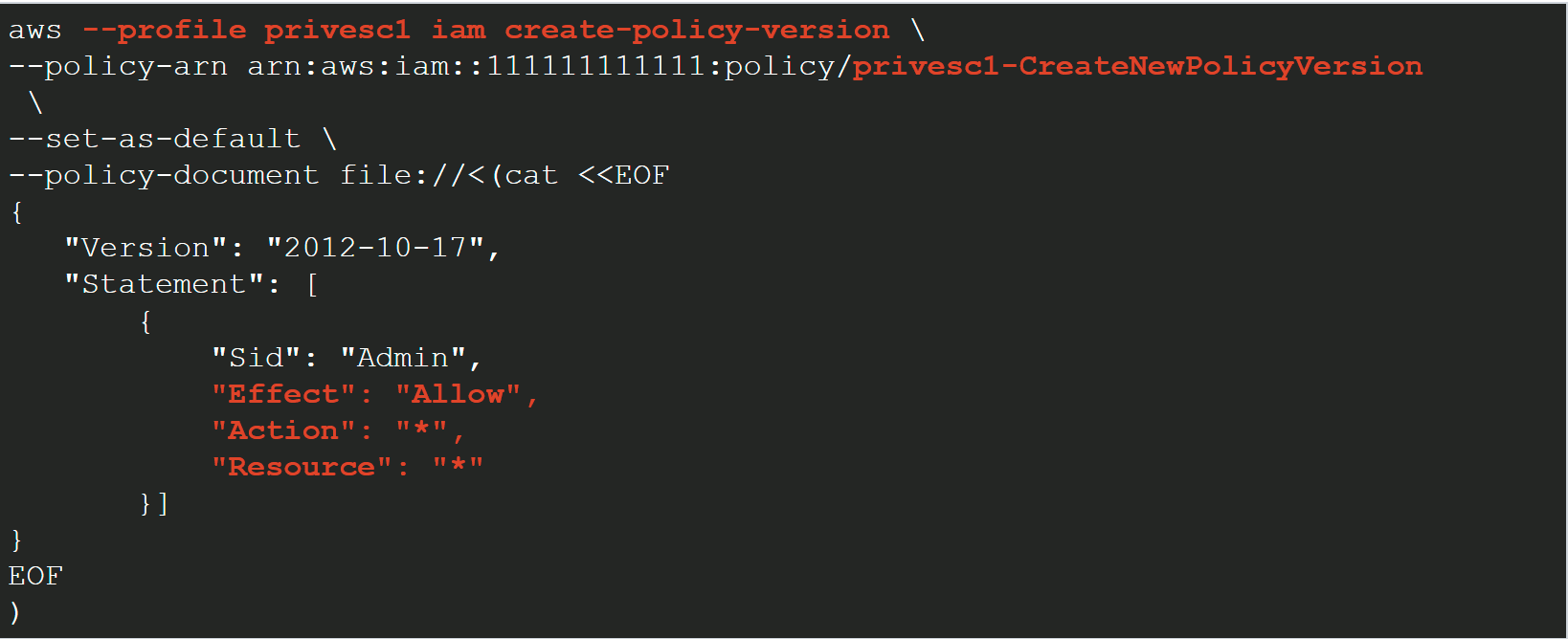
- 31 users, roles, and policies each with a unique exploit path to administrative access of the playground account
- Some additional users, groups, roles, and policies that are required to fully realize certain exploit paths
- Some additional users, roles, and policies that test the detection capabilities of other tools
By default, every role created by this Terraform module is assumable by the user or role you used to run Terraform.
- If you’d like Terraform to use a profile other than the default profile, or you’d like to hard-code the assume_role_policy ARN, see Other Use Cases.
FAQ
How does IAM Vulnerable compare to CloudGoat, Terragoat, and SadCloud?
All of these tools use Terraform to deploy intentionally vulnerable infrastructure to AWS. However, IAM Vulnerable’s focus is IAM privilege escalation, whereas the other tools either don’t cover IAM privesc or only cover some scenarios.
- CloudGoat deploys eight unique scenarios, some of which cover IAM privesc paths, while others focus on other areas like secrets in EC2 metadata.
- Terragoat and SadCloud both focus on the many ways you can misconfigure your cloud accounts but do not cover IAM privesc paths. In fact, you can almost think of IAM vulnerable as a missing puzzle piece when applied alongside Terragoat or SadCloud. The intentionally vulnerable configurations complement each other.
How does IAM Vulnerable compare to Cloudsplaining, AWSPX, Principal Mapper, Pacu, Cloudmapper, or ScouteSuite?
All of these tools help identify existing misconfigurations in your AWS environment. Some, like Pacu, also help you exploit misconfigurations. In contrast, it creates intentionally vulnerable infrastructure. If you really want to learn how to use tools like Principal Mapper (PMapper), AWSPX, Pacu, and Cloudsplaining, it is for you.
Install
Copyright (c) 2021 Bishop Fox