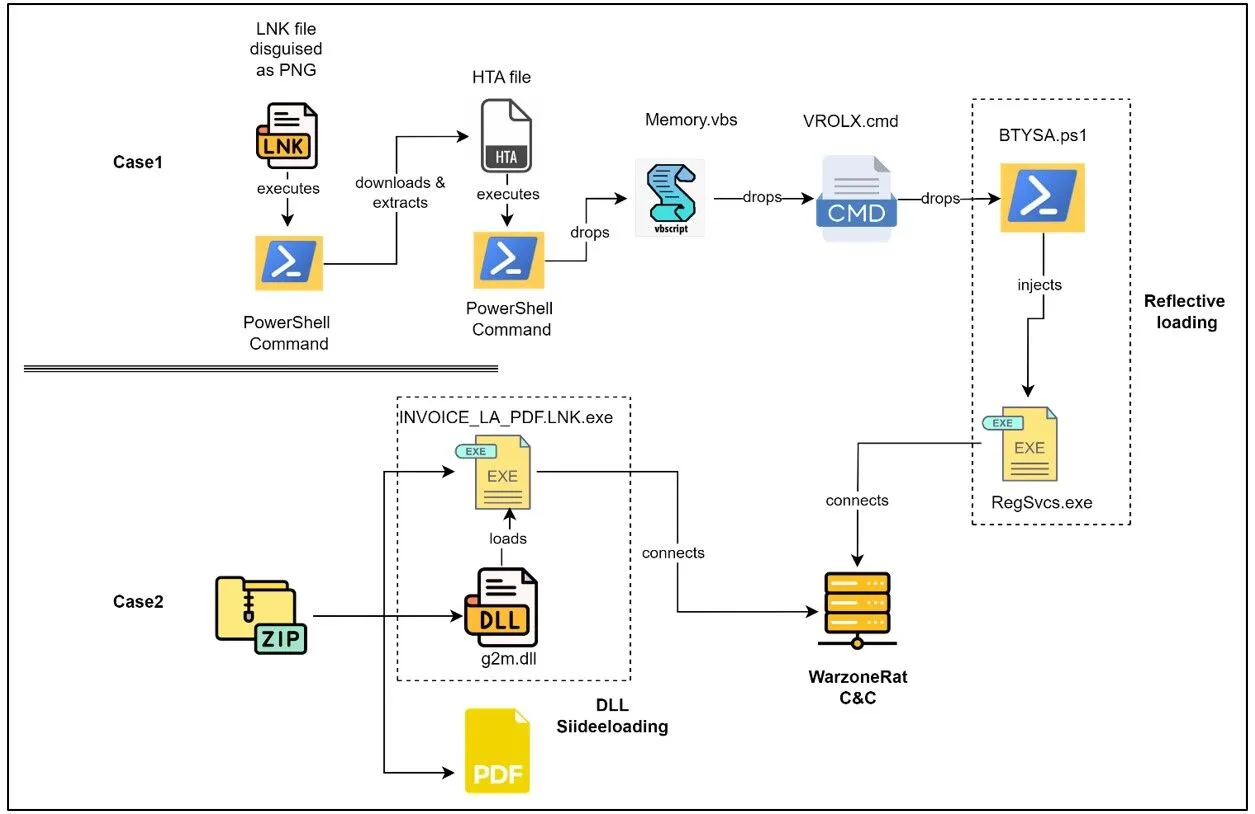
Overall infection chain
In a troubling development, the notorious WarzoneRAT (also known as Avemaria), has made a comeback following a brief hiatus caused by the FBI’s seizure of its infrastructure in February. According to a new report from Cyble Research & Intelligence Labs (CRIL), threat actors are now actively deploying this enhanced RAT in stealthy, multi-stage attacks.
The Evolving Threat
The latest WarzoneRAT campaigns primarily target victims via tax-themed spam emails, cleverly exploiting a timely and often anxiety-inducing subject to increase the likelihood of users opening malicious attachments. The CRIL report details two primary infection methods:
- Trojanized Shortcut: Victims are tricked into opening a seemingly harmless PNG image file, which is a cleverly disguised shortcut. This shortcut unleashes a complex chain of downloads, scripts, and evasive maneuvers, ultimately installing WarzoneRAT.
- DLL Sideloading: In this method, a legitimate-looking executable file is bundled with a malicious DLL. When the victim runs the executable, the DLL sideloading technique launches, loading WarzoneRAT directly into memory for a stealthier infection.
Inside the Attack

Once WarzoneRAT has infiltrated a system, it employs a sophisticated arsenal of tools to gain a foothold and evade detection. This includes:
- Defense Evasion: The malware disables security features like Windows Defender, patches critical Windows functions like AMSI (Anti-Malware Scan Interface), and alters various settings to weaken the system’s defenses.
- Command and Control: WarzoneRAT connects with remote servers controlled by the attackers, allowing them to send commands and steal sensitive data.
- Privilege Escalation: The malware may attempt to gain elevated privileges on the infected system, giving the attackers extensive control.
WarzoneRAT’s Capabilities
If successful, attackers armed with WarzoneRAT gain the ability to:
- Steal personal data, login credentials, and financial information
- Monitor keystrokes and online activity
- Remotely control the victim’s computer
- Install additional malware for further attacks
What Makes This Resurgence Concerning
The FBI seizure in February was a significant blow to the actors behind WarzoneRAT. However, this latest report suggests that they have regrouped and quickly enhanced the malware’s capabilities. This highlights the persistent and adaptable nature of cybercriminal operations.
The Takeaway
The WarzoneRAT resurgence is a reminder that even disrupted malware operations can quickly return, often in a more sophisticated form. Proactive vigilance and a layered defense strategy are critical for individuals and organizations to protect themselves against this ever-evolving threat.