Infection Monkey v2.3 released: An automated pentest tool

Infection Monkey
The Infection Monkey is an open-source security tool for testing a data center’s resiliency to perimeter breaches and internal server infection. The Monkey uses various methods to self-propagate across a data center and reports success to a centralized Command and Control(C&C) server.
The Infection Monkey is comprised of two parts:
- Monkey – A tool which infects other machines and propagates to them
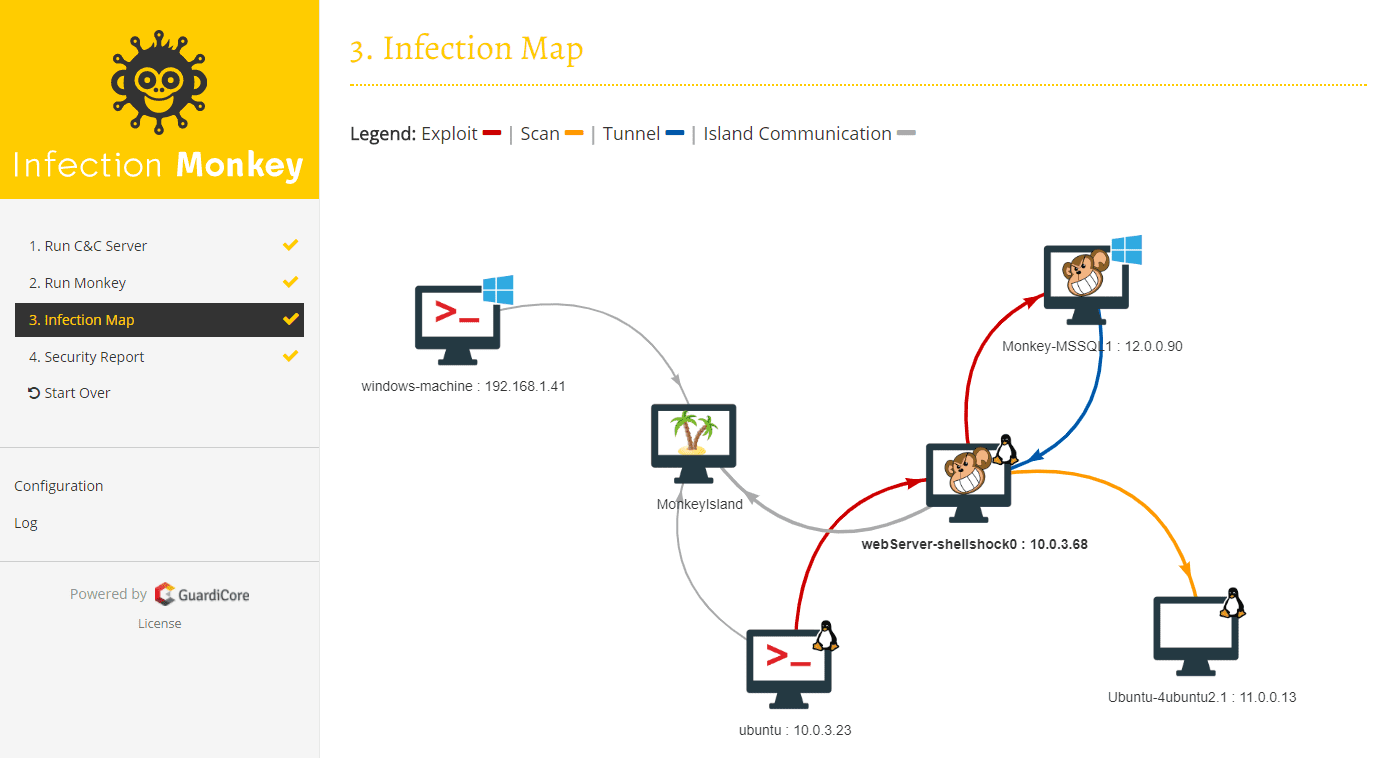
- Monkey Island – A C&C server with a dedicated UI to visualize the Chaos Monkey’s progress inside the data center
To read more about the Monkey, visit http://infectionmonkey.com
Main Features
The Infection Monkey uses the following techniques and exploits to propagate to other machines.
- Multiple propagation techniques:
- Predefined passwords
- Common logical exploits
- Password stealing using mimikatz
- Multiple exploit methods:
- SSH
- SMB
- RDP
- WMI
- Shellshock
- Conficker
- SambaCry
- Elastic Search (CVE-2015-1427)
Changelog v2.3
Objective
This release is focused on adding high-value features to Infection Monkey.
New Features
Propagation via RDP
Infection Monkey can now use RDP to propagate itself to Windows targets. According to The DFIR Report’s 2022 Year in Review, 41.2% of lateral movement occurs via RDP. Infection Monkey users can now simulate this behavior in their environments and ensure they are prepared to detect and handle it.
Cryptojacker simulation
A new cryptojacker payload has been added that performs cryptographic functions with the goal of consuming a configurable amount of CPU. It can also consume a configurable quantity of RAM, as well as simulate some bitcoin mining traffic.
Steal credentials from Chrome
Credentials can be stolen from chrome browsers and used for lateral movement. On Windows hosts, credentials can be stolen from Chrome and Edge. On Linux hosts, credentials can be stolen from Chrome and Chromium.
Plugin installation menu
Infection Monkey provides capabilities for exploitation/propagation, credentials stealing, and payloads via plugins. These plugins are now installable from a remote repository. This results in some highly-impactful advantages for users.
- Users can receive and use new features without completely reinstalling Infection Monkey.
- Users can receive bug fixes in certain modules without completely reinstalling Infection Monkey.
- Users can choose not to install certain plugins, which eliminates the risk associated with misconfiguration. This makes Infection Monkey safer in mission-critical environments.
Changelog
Added
- Ability to filter Agent events by timestamp. #3397
- Ability to filter Agent events by tag. #3396
- Provide a common server object to the plugins that can be used to serve agent
binaries to the exploited machine over HTTP. #3410 - CPUConsumptionEvent. #3411
- RAMConsumptionEvent. #3411
- HTTPRequestEvent. #3411
- DefacementEvent. #1247
- RDP exploiter plugin. #3425
- A cryptojacker payload to simulate cryptojacker attacks. #3411
PUT /api/install-agent-plugin. #3417GET /api/agent-plugins/installed/manifests. #3424GET /api/agent-plugins/available/index. #3420POST /api/uninstall-agent-plugin# 3422- Chrome credentials collector plugin. #3426
- A plugin interface for payloads. #3390
- The ability to install plugins from an online repository. #3413, #3418, #3616
- Support for SMBv2+ in SMB exploiter. #3577
- A UI for uploading agent plugin archives. #3417, #3611
Changed
- Plugin source is now gzipped. #3392
- Allowed characters in Agent event tags. #3399, #3676
- Hard-coded Log4Shell exploiter to a plugin. #3388
- Hard-coded SSH exploiter to a plugin. #3170
- Identities and secrets can be associated when configuring credentials in the
UI. #3393 - Hard-coded ransomware payload to a plugin. #3391
- Text on the registration screen to improve clarity. #1984
Fixed
- Agent hanging if plugins do not shut down. #3557
- WMI exploiter hanging. #3543
- Discovered network services are displayed in reports. #3000
Removed
Security
- Fixed a ReDoS issue when validating ransomware file extensions. #3391
Download & Setup
Copyright (c) 2017 Guardicore Ltd
Source: https://github.com/guardicore/