RECON: Information Gathering Automation framework
AUTO-RECON
Information Gathering Automation framework. This program is intended to be used in Kali Linux.
Features!
- This tool is intended for CTF’s and can be fairly noisy. (Not the most stealth conscious tool…)
- All tools in this project are compliant with the OSCP exam rules.
- If Virtual Host Routing is detected, Auto-Recon will add the hostnames to your /etc/hosts file and continue to enumerate the newly discovered hostnames.
- DNS enumeration is nerfed to ignore .com .co .eu .uk .git domains etc… since this tool was designed for CTF’s like hack the box. It will try to find most .htb and .local domains.
- This project use’s various tools and chains them together as needed to enumerate a target based off nmap results.
- Using python multiprocessing, services can be scanned quickly.
INSTALLATION
cd /opt
git clone https://github.com/gotr00t0day/RECON.git
cd RECON
chmod +x setup.sh
./setup.sh
python3 -m pip install -r requirements.txt
Usage
To scan a single target and enumerate based off of nmap results:
python3 recon.py -t 10.10.10.10
To Enumerate Web with larger wordlists
python3 recon.py -w 10.10.10.10
To Scan + Enumerate all IPv4 addr’s in ips.txt file
python3 recon.py -f ips.txt
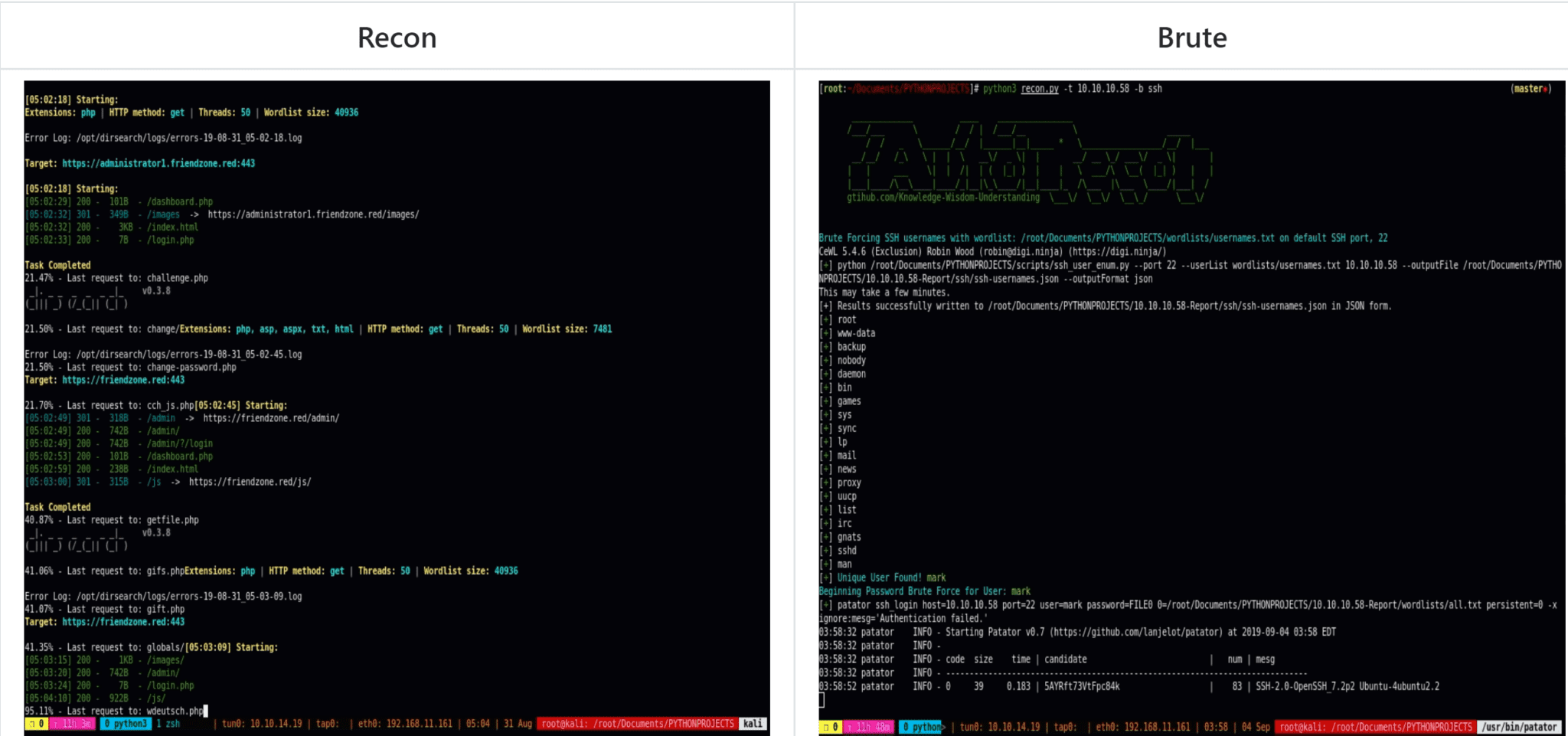
Brute force ssh users on default port 22 If unique valid users found, brute force passwords
python3 recon.py -t 10.10.10.10 -b ssh
Same as above but for ssh on port 2222 etc…
python3 recon.py -t 10.10.10.10 -b ssh -p 2222
Demo
Copyright (c) 2019 Knowledge-Wisdom-Understanding
Source: https://github.com/gotr00t0day/






