Image: Google
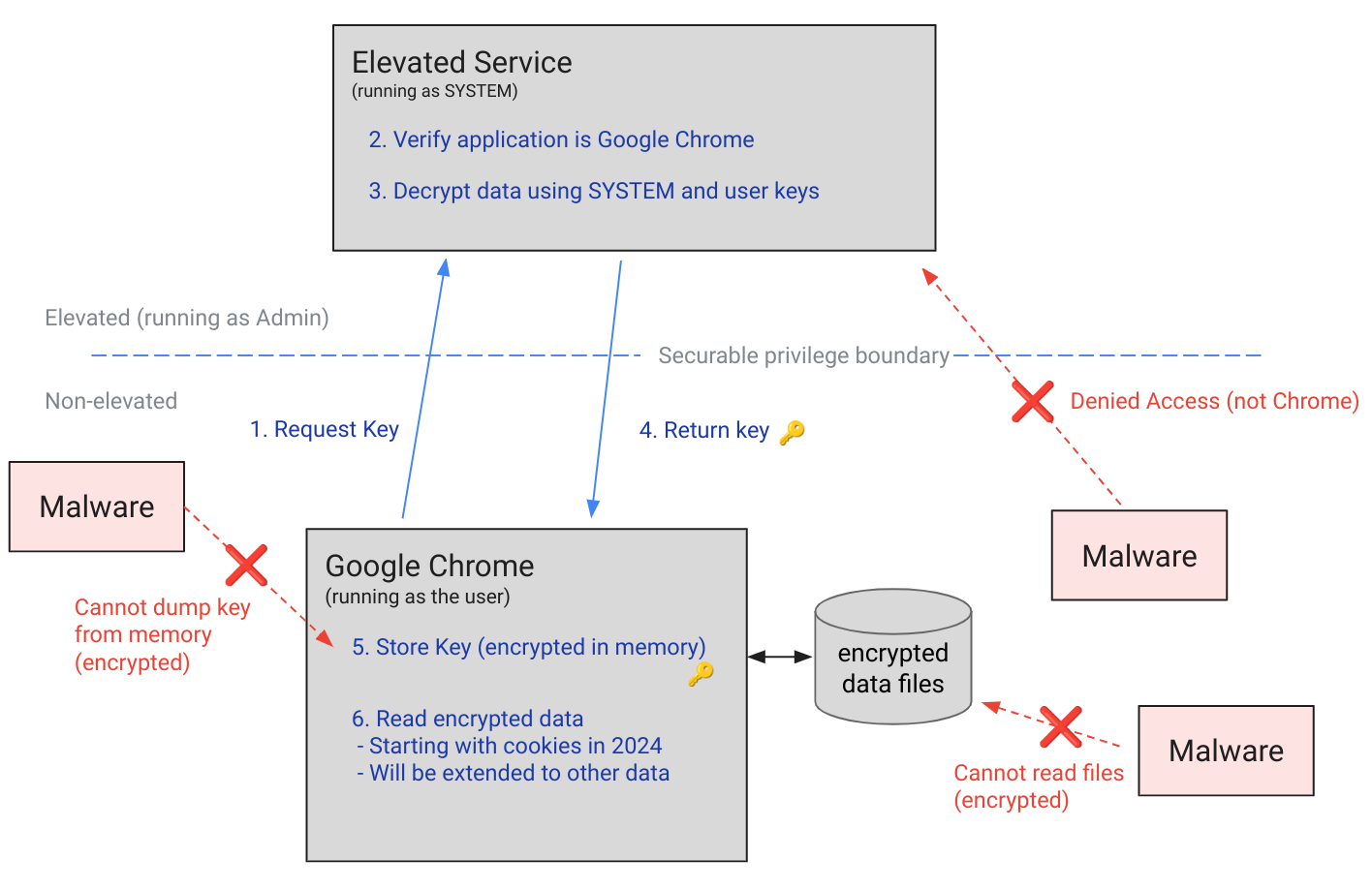
In a concerning development for cybersecurity, developers of several notorious infostealers have announced that they have successfully bypassed Chrome’s App-Bound Encryption feature introduced in version 127. This advancement enables these malicious tools to harvest authentication cookies that were previously secured through encryption, posing a renewed threat to user data privacy.
The infamous #Vidar Stealer also announced today an update to featuring his own bypass to the newest Google Chrome app-bound cookie encryption (without admin privileges)
This announcement is followed after infostealers Meduza, Lumma and Lumar
Full statement 👇👇 https://t.co/ZbppJDA99u pic.twitter.com/YNu0bvAVjU
— Who said what? (@g0njxa) September 20, 2024
Google rolled out the App-Bound Encryption feature in July with Chrome 127, aiming to enhance data security by encrypting browser-associated data. This encryption was designed to be accessible only with administrator credentials, adding an extra layer of protection against unauthorized access. However, within just two months, malware developers have found ways to sidestep this security measure.
Infostealers such as Lumar, Lumma, Meduza, Vidar, and WhiteSnake have updated their capabilities to circumvent the App-Bound Encryption. Initially, these malware strains attempted various methods to overcome the barrier, including injecting malicious code directly into the Chrome process and exploiting privilege escalation vulnerabilities to gain administrative rights. Their success in bypassing the encryption now allows them to collect sensitive data that users believed to be secure.
To bolster defenses further, Google is developing a new security feature called Device Bound Session Credentials (DBSC). Scheduled for testing by the end of the year, DBSC will utilize cryptographic keys tied to the user’s device, providing an additional layer of encryption for passwords and cookie data. This feature aims to ensure that even if data is accessed by unauthorized parties, it remains encrypted and unusable on other devices.
DBSC is expected to be supported on approximately half of all Chrome desktop devices upon initial rollout. It aligns with Google’s broader initiative to phase out third-party cookies, enhancing user privacy and security simultaneously. Once fully implemented, both individual consumers and enterprise users will benefit from improved protection for their Google accounts without requiring additional actions on their part.
Related Posts:
- Google Chrome Strengthens Cookie Security on Windows with App-Bound Encryption
- Suspected CoralRaider Expands Attacks, Targets Diverse Victims with Triple-Threat Infostealer Campaign
- The Silent Threat: Unmasking Undetected macOS InfoStealers