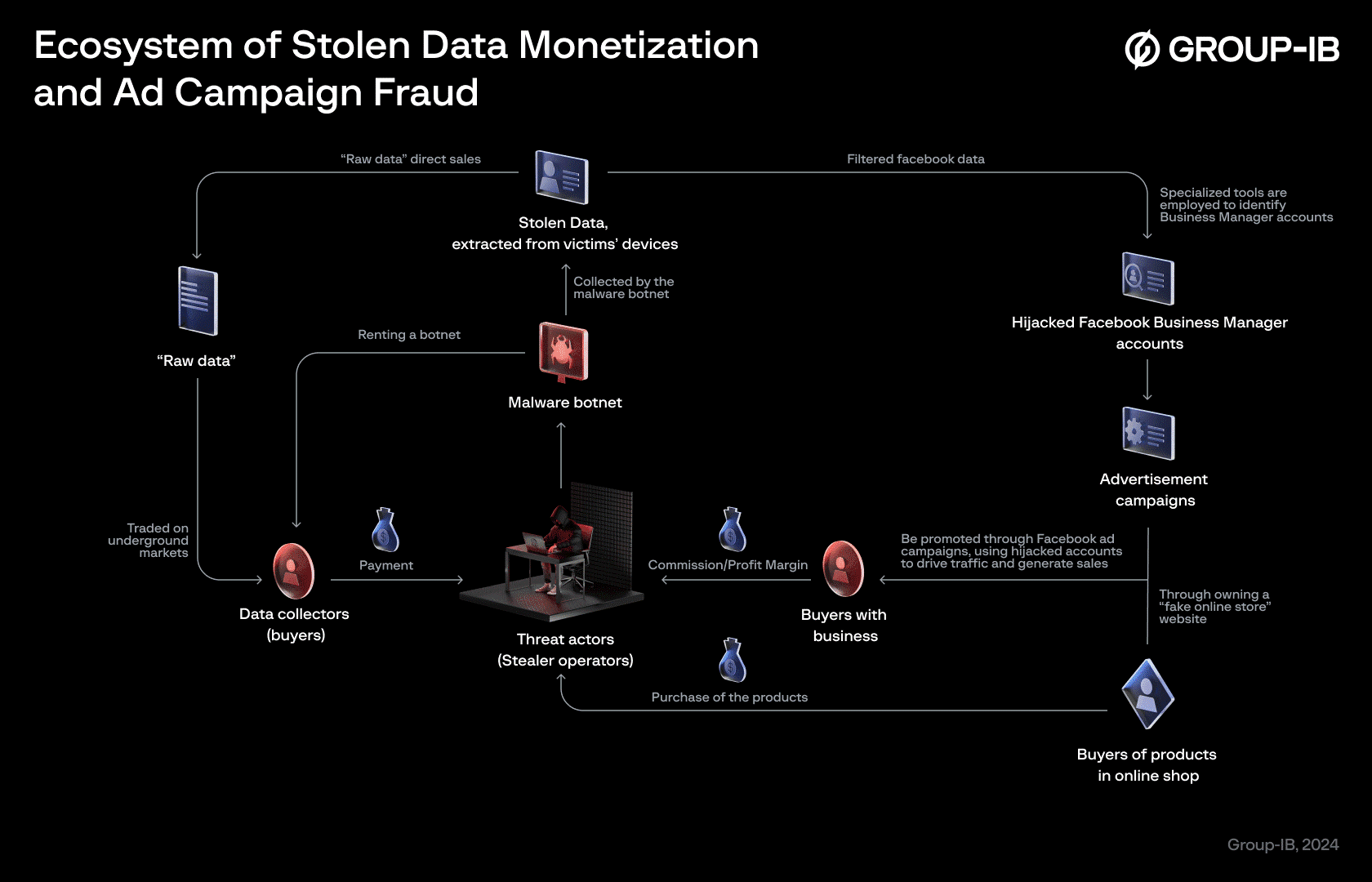
The Ecosystem of Facebook stolen data monetization | Image: Group-IB
Vietnam has become a hotspot for malicious operations targeting Facebook Business accounts, with threat actors leveraging infostealers like VietCredCare and DuckTail. According to a report from Group-IB, these malware families have fueled a thriving underground market for compromised data and unauthorized advertising campaigns.
Group-IB reports that VietCredCare and DuckTail emerged as dominant threats between 2022 and 2023. While VietCredCare activity declined following a series of arrests by Vietnamese law enforcement in 2024, DuckTail continues to operate and evolve. The report highlighted: “Both malware families are believed to have been crafted and operated by threat actors within Vietnam, and they target Vietnamese and overseas businesses, particularly Facebook Business accounts, for unauthorized advertising campaigns.“
Both VietCredCare and DuckTail share core functionalities designed to compromise Facebook Business accounts. They utilize spear-phishing tactics, Telegram API for exfiltration, and target sensitive data like session cookies and credentials. As Group-IB notes: “Their primary goal is financial gain through unauthorized access and control of Facebook business accounts.”
Despite these shared objectives, their operational strategies and capabilities differ significantly.
- Malware Delivery
- VietCredCare: Disguised malware as trusted software, such as Microsoft Excel or Acrobat Reader, and distributed it via Facebook Messenger, WhatsApp, or email.
- DuckTail: Targeted professionals on LinkedIn and WhatsApp with job offers or marketing projects, sharing malware-laden links hosted on cloud services like Dropbox or iCloud.
- Technical Sophistication
- VietCredCare was designed primarily for stealing Facebook account data, while DuckTail featured advanced functionalities, such as: checking whether two-factor authentication (2FA) is enabled and attempting to retrieve recovery codes.
- Monetization Models
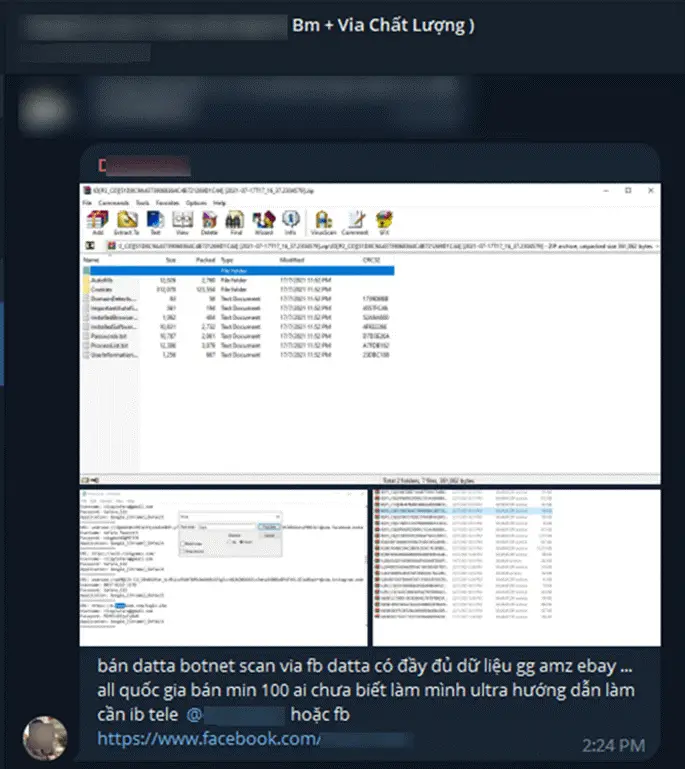
- VietCredCare’s operators sold raw data, such as session cookies and credentials, in bulk on Telegram groups.
- DuckTail utilized hijacked accounts for unauthorized advertising campaigns, often promoting fake online stores to maximize illicit profits.
The stolen data from both malware families feeds into a bustling underground market. Compromised Facebook Business Manager (BM) accounts are either sold or exploited for fraudulent advertising. According to Group-IB: “it is possible to get several thousand US dollars per day for using compromised ad accounts and advertising online shops controlled by threat actors.”
Telegram groups facilitate this trade, advertising account quality based on metrics like follower count, account balance, and prior campaign success.
While arrests have disrupted some activities, the continued operation of DuckTail suggests this market is far from dormant. Group-IB warns: “The Facebook dark market will keep growing, and more malware families will emerge to support its illegal operations.”
Related Posts:
- New Ducktail Malware Campaign Uses Delphi to Steal Facebook Business Accounts
- Beware of LinkedIn: Ducktail Malware’s Sneaky ZIP Attack Revealed
- Ducktail & Quasar RAT: Vietnamese Threat Actors Target Meta Ads Professionals
- The Cobalt hacker group is still active, although the leader was arrested
- Group-IB and other security firms assisted Ukrainian police in taking down on DDoS criminal gangs