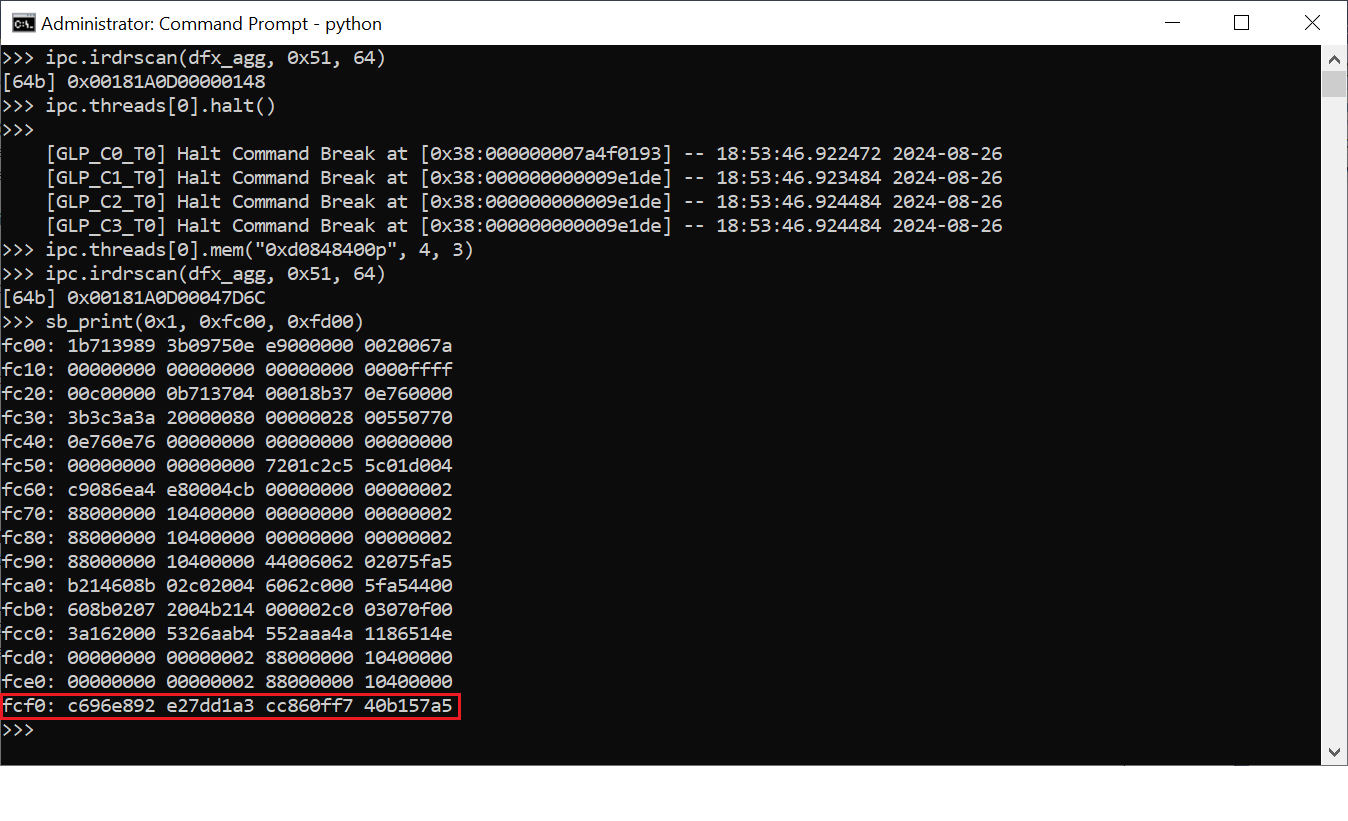
Recently, researcher Mark Ermolov has successfully extracted Intel’s SGX Fuse Key0, also known as the Root Provisioning Key. This key, introduced with Intel’s Skylake processors, is a cornerstone of Intel’s Software Guard eXtensions (SGX), a technology designed to create secure, isolated environments for sensitive data processing, known as enclaves or Trusted Execution Environments (TEEs).
Introduced with Intel’s Skylake processors, SGX was designed to protect sensitive data by creating secure enclaves—isolated compartments of memory that remain inaccessible even to the operating system itself. These enclaves, or Trusted Execution Environments (TEEs), serve as a fortress for critical data, ensuring its safety even if the broader system is compromised.
At the heart of SGX’s security is a suite of keys, including the Root Provisioning Key (FK0) and the Root Sealing Key (FK1), both of which derive from a master key embedded within the processor’s fuses. These keys are meant to be unique, unknown, and irremovable, providing the essential “Root of Trust” for the entire platform. However, this foundational security has now been called into question.
Ermolov’s successful extraction of the SGX Fuse Key0 was made possible by a flaw in Intel’s microcode—a critical component of the processor’s firmware. The microcode failed to clear an internal buffer that temporarily held all the fuse values, including FK0, during the manufacturing process. This oversight allowed Ermolov to access the key, which should have been securely protected and inaccessible under normal circumstances.
“The complexity of Intel’s hardware leaves room for errors, and after years of diligent research, we were able to extract the Intel SGX Fuse Key0, a key that represents the Root of Trust for SGX,” Ermolov explained. “While Intel’s microcode worked as intended, the failure to clear the internal buffer exposed these critical keys, compromising the platform’s security.”
The ramifications of this breach are profound. The extracted Fuse Key0, combined with the compromised Root Sealing Key (FK1), means that attackers could potentially decrypt sealed data, forge attestation reports, and completely bypass the security guarantees that SGX is supposed to offer.
What exacerbates the situation is the Global Wrapping Key (GWK), also known as the Fuse Encryption Key (FEK), which is supposed to protect FK0. The GWK is shared across all processors within the same microarchitecture, meaning that if this key is compromised, it could potentially expose the Fuse Key0 of all processors sharing that design. This turns a unique, chip-specific security measure into a widespread vulnerability that could affect countless devices.
The breach primarily affects processors from the Apollo Lake, Gemini Lake, and Gemini Lake Refresh families—processors that, although now end-of-life (EOL), are still widely deployed in embedded systems and low-power devices. Despite their discontinuation, the legacy of these processors continues, and so too does the threat posed by this vulnerability.
This breach is the latest in a series of vulnerabilities that have targeted Intel SGX over the years:
- SGAxe: This attack breached the security guarantees of SGX enclaves by extracting attestation keys from Intel’s quoting enclave. This allowed network attackers to impersonate legitimate SGX systems, undermining trust in SGX-based applications.
- SmashEx: Discovered by a team of academics in 2021, SmashEx enabled a confidential data disclosure attack that corrupted private data within the enclave, breaking its integrity and compromising its confidentiality.
Update on August 30th:
“What Positive Technologies seems to have found is expected based on previous mitigated vulnerabilities in DFX Aggregator logic, requiring physical access to Gemini Lake systems without Intel Firmware Version Control capability. An attacker must have physical access to an unmitigated system impacted by prior vulnerabilities (CVE-2017-5705, CVE-2017-5706, CVE-2017-5707, CVE-2019-0090) that allow Intel Unlock state to be achieved. Intel has provided mitigations for these prior vulnerabilities,” an Intel spokesperson talk with us.
Intel recommends:
- Setting up systems at the end of manufacturing to enable Intel® Firmware Version Control to help prevent this and other vulnerabilities.
- Completing End of Manufacturing process, set Manufacturing Mode to Disabled, and enable Intel® Firmware Version Control.
- Ensuring all security mitigations provided by Intel are applied.
For more details, please read the Intel security advisory.
Related Posts:
- SGXPECTRE, new Spectre attack variant compromises Intel SGX
- CVE-2024-6633 (CVSS 9.8): Critical Flaw in Fortra FileCatalyst Workflow
