Invoke-Apex
Invoke-Apex is a PowerShell-based toolkit consisting of a collection of techniques and tradecraft for use in red team, post-exploitation, adversary simulation, or other offensive security tasks. It can also be useful in identifying lapses in “malicious” activity detection processes for defenders as well.
I wrote this toolkit with the intention of obtaining a deeper understanding of the techniques in use by real-world adversaries (APTs) while applying similar techniques in my work (Pentesting). I also wanted to create a tool that could act a starting “point” (hence “Apex”) with regard to post-exploitation of a target system. I’m sure there are some bugs, and some of the code could probably (very likely) be more efficient (I’m not a “developer” by any stretch of the imagination) … but hey, it appears to serve its purpose for the time being. 😉
Any techniques, where applicable, are credited within the source code of the included .ps1 scripts, so thanks to everyone who contributes to offensive/defensive security research! If I forgot to mention or credit a technique to a particular researcher, don’t hesitate to ping me and I’ll add it to the source. For the most part, many of the techniques were derived from Mitre ATT&CK and the LOLBAS projects.
The Mitre ATT&CK Reference component
Each technique or method in the toolkit is mapped back to a Mitre ATT&CK Technique ID where applicable, and the techniques and modules which they can be found in can be viewed with the Invoke-MitreReference -Help command.
PS> Invoke-MitreReference -Help
PS> Invoke-MitreReference -Help
|------------------------------------------------------------------|
| ### MITRE ATT&CK TECHNIQUE REFERENCE ### |
|------------------------------------------------------------------|
<...snip...>
Module: Invoke-Creds
--------------------
Mitre ATT&CK Ref: T1056 (Input Capture)
Mitre ATT&CK Ref: T1081 (Credentials in Files)
Mitre ATT&CK Ref: T1003 (Credential Dumping)
Module: Invoke-DefenderTools
----------------------------
Mitre ATT&CK Ref: T1211 (Exploitation for Defense Evasion)
Mitre ATT&CK Ref: T1089 (Disabling Security Tools)
Module: Invoke-Download
-----------------------
Mitre ATT&CK Ref: T1105 (Remote File Copy)
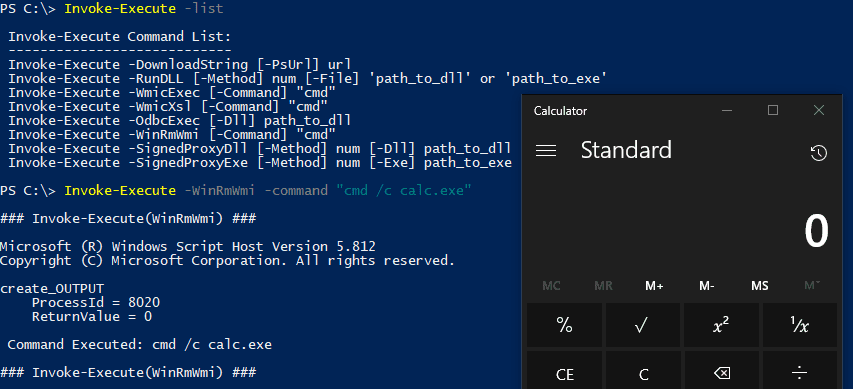
Module: Invoke-Execute
----------------------
Mitre ATT&CK Ref: T1086 (PowerShell)
Mitre ATT&CK Ref: T1085 (Rundll32)
Mitre ATT&CK Ref: T1047 (Windows Management Instrumentation)
Mitre ATT&CK Ref: T1220 (XSL Script Processing)
Mitre ATT&CK Ref: T1028 (Windows Remote Management)
Mitre ATT&CK Ref: T1218 (Signed Binary Proxy Execution)
<...snip...>
You can also lookup which Mitre ATT&CK techniques are in use, and in which modules with the -Tid parameter and specifying a Mitre ATT&CK Technique ID as a value:
PS> Invoke-MitreReference -Tid 1352
Modules using Mitre ATT&CK Ref: T1352 (C2 Protocol Development):
[+] Module: Invoke-Connect
Listing all available functions
PS> Invoke-Apex
8888888b. Y88b d88P
888 Y88b Y88b d88P
888 888 Y88o88P
8888b. 888 d88P .d88b. Y888P
"88b 8888888P" d8P Y8b d888b
.d888888 888 88888888 d88888b
888 888 888 Y8b. d88P Y88b
"Y888888 888 "Y8888 d88P Y88b
Y88b
Post-Exploitation Toolkit Y88b
By: Fabrizio Siciliano (@0rbz_) V1.0
[*] Usage: [Function-Name] -Help (Shows Help for each command within a function)
[*] Usage: [Function-Name] -List (Summary list of available commands within a function)
[*] Example: Invoke-DefenderTools -Help
[*] Example: Invoke-DefenderTools -List
CommandType Name Version Source
----------- ---- ------- ------
Function Invoke-Apex 1.0 Invoke-Apex
Function Invoke-Connect 1.0 Invoke-Apex
Function Invoke-Creds 1.0 Invoke-Apex
Function Invoke-DefenderTools 1.0 Invoke-Apex
Function Invoke-Download 1.0 Invoke-Apex
Function Invoke-Execute 1.0 Invoke-Apex
Function Invoke-Exfil 1.0 Invoke-Apex
Function Invoke-GlasswireExceptions 1.0 Invoke-Apex
Function Invoke-MitreReference 1.0 Invoke-Apex
Function Invoke-Persistence 1.0 Invoke-Apex
Function Invoke-Privesc 1.0 Invoke-Apex
Function Invoke-Sysinfo 1.0 Invoke-Apex
Function Invoke-TCPScan 1.0 Invoke-Apex
Function Invoke-TimeStomp 1.0 Invoke-Apex
Function Invoke-XuLiE 1.0 Invoke-Apex
Function New-Lnk 1.0 Invoke-Apex
Function New-PsDat 1.0 Invoke-Apex
Function New-PsTask 1.0 Invoke-Apex
Function New-Reverse 1.0 Invoke-Apex
Copyright (c) 2019, SecureMode
All rights reserved.