Invoke-DNSteal
Invoke-DNSteal is a Simple & Customizable DNS Data Exfiltration.
This tool helps you to exfiltrate data through DNS protocol over UDP and TCP and lets you control the size of queries using random delay. Also, allows you to avoid detections by using random domains in each of your queries and you can use it to transfer information both locally and remotely.
Install
Requirements
- Powershell 4.0 or higher
- Python 2
Download
git clone https://github.com/JoelGMSec/Invoke-DNSteal.git
Use
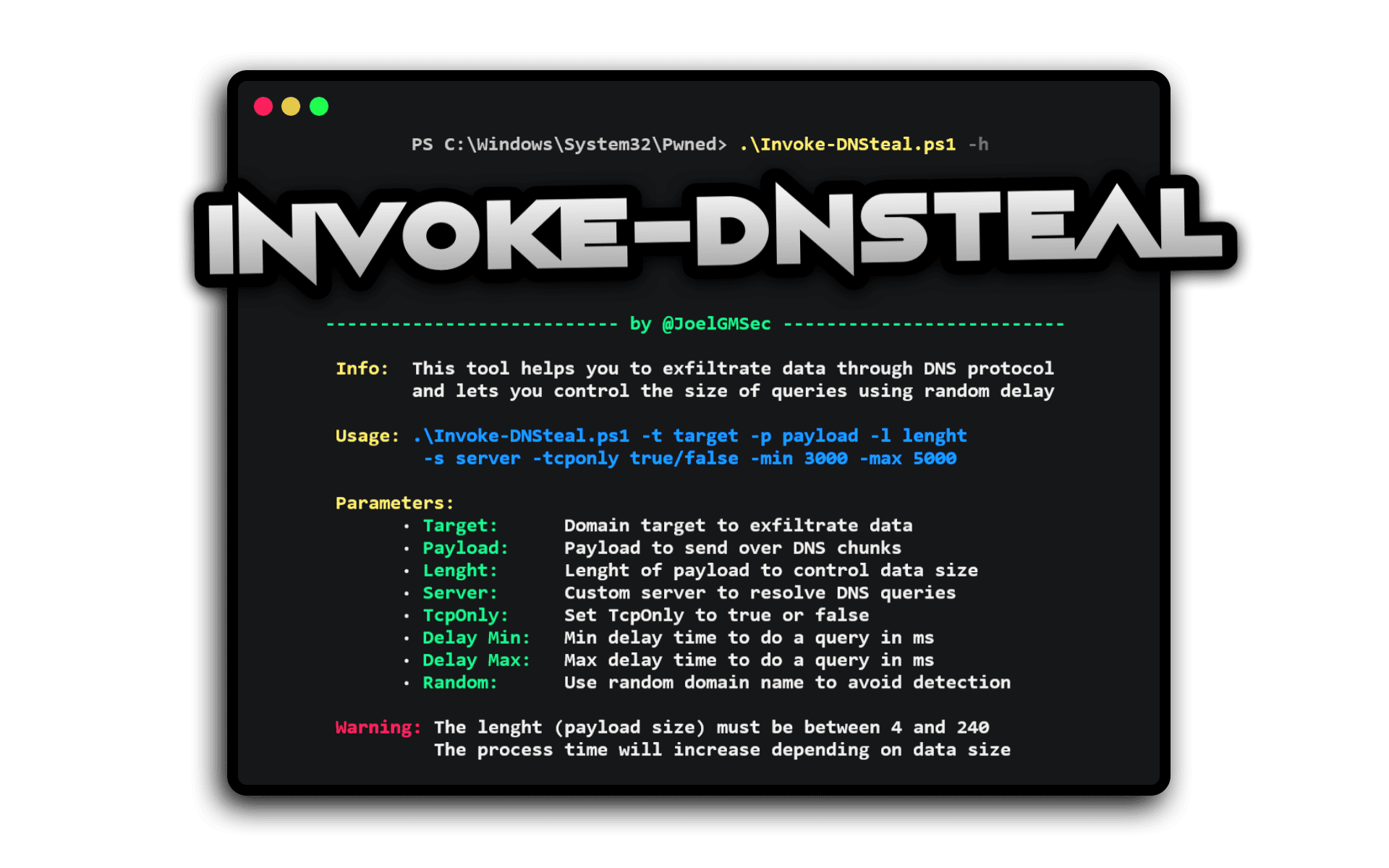
.\Invoke-DNSteal.ps1 -h
___ _ ____ _ _ ____ _ _
|_ _|_ __ _ __ __ | | __ __ | _ \| \ | / ___|| |__ __ __ _| |
| || ‘_ \ \ / / _ \| |/ / _ \_____| | | | \| \___ \| __/ _ \/ _’ | |
| || | | \ V / (_) | < __/_____| |_| | |\ |___) | || __/ (_| | |
|___|_| |_|\_/ \___/|_|\_\___| |____/|_| \_|____/ \__\___|\__,_|_|————————— by @JoelGMSec ————————–
Info: This tool helps you to exfiltrate data through DNS protocol
and lets you control the size of queries using random delayUsage: .\Invoke-DNSteal.ps1 -t target -p payload -l lenght
-s server -tcponly true/false -min 3000 -max 5000Parameters:
· Target: Domain target to exfiltrate data
· Payload: Payload to send over DNS chunks
· Lenght: Lenght of payload to control data size
· Server: Custom server to resolve DNS queries
· TcpOnly: Set TcpOnly to true or false
· Delay Min: Min delay time to do a query in ms
· Delay Max: Max delay time to do a query in ms
· Random: Use random domain name to avoid detectionWarning: The lenght (payload size) must be between 4 and 240
The process time will increase depending on data size
Copyright (C) 2021 Joel Gámez Molina // @JoelGMSec
Source: https://github.com/JoelGMSec/