iOS Malicious Bit Hunter: malicious plug-in detection engine for iOS applications
iOS Malicious Bit Hunter
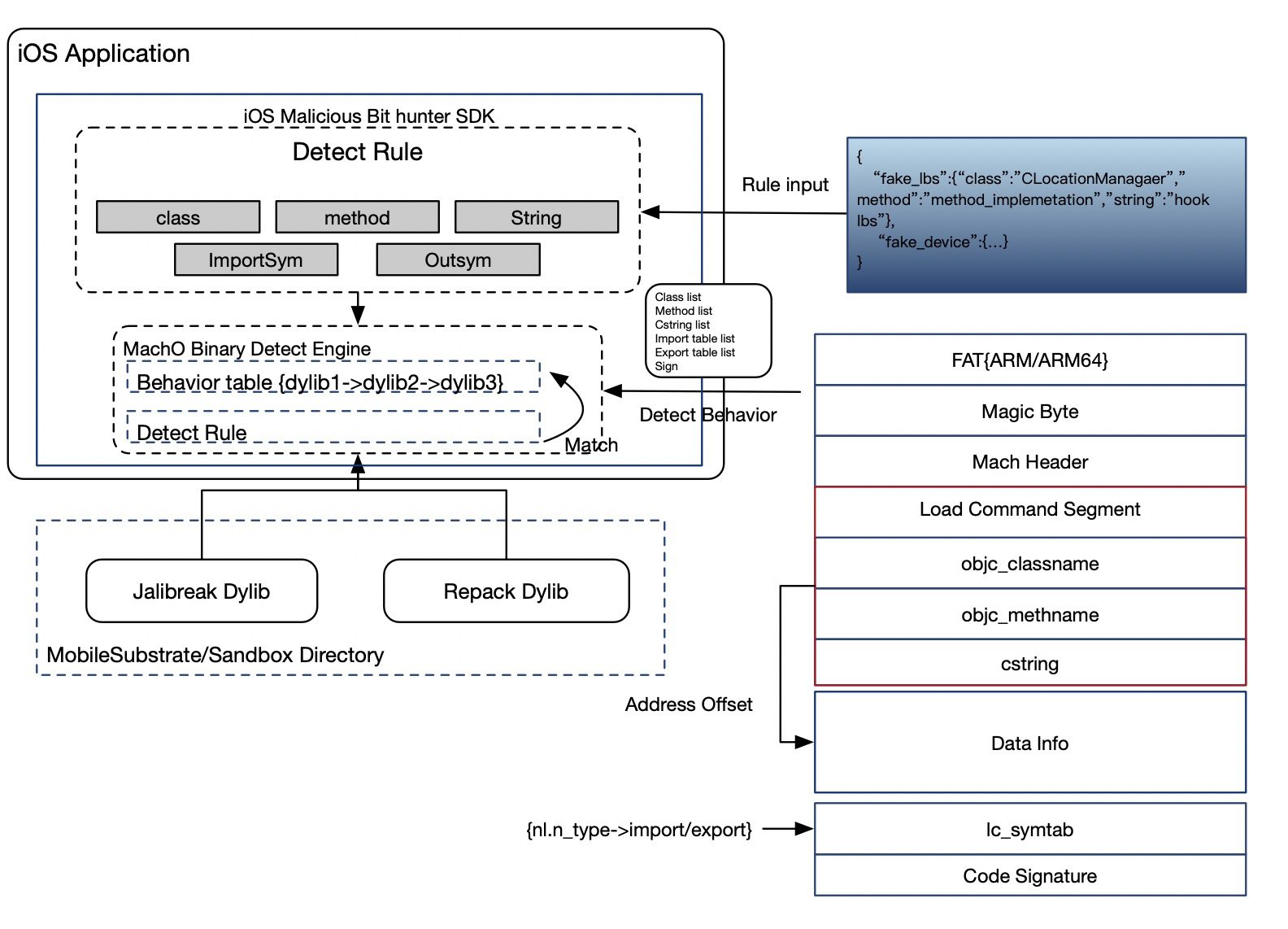
iOS Malicious Bit Hunter is a malicious plug-in detection engine for iOS applications. It can analyze the head of the macho file of the injected dylib dynamic library based on runtime and can perform behavior analysis through interface input characteristics to determine the behavior of the dynamic library feature. The program does not rely on the jailbreak environment and can be used on the AppStore.
What’s the new feature
This is a new way to accurately identify the behavior of iOS malicious code. Based on the method of analyzing malicious code running in the memory based on the Mach-O format in the App, it can perform flexible behavior recognition for analysis and continuous tracking. This is a very accurate anti-plug-in defense method, including behaviors, variables, and highly obfuscated code (including ollvm), which has achieved very good results in our defense process.
Logic Principle
The tool provides an API interface for obtaining external match rules. It will analyze the behavior of jailbroken and repackaged dynamic libraries at runtime, mainly through static analysis of the MachO file format, through the Load Command and different segments Obtain the import table, export table, class name, function name, string, and other information, and judge whether the dynamic library has been loaded into the memory through the memory map at runtime.
Download & Use
Copyright (C) 2021 SecurityLife





