IoT-Home-Guard: A tool for malicious behavior detection in IoT devices
IoT-Home-Guard
IoT-Home-Guard is a project to help people discover malware in smart home devices.
For users, the project can help to detect compromised smart home devices. For security researchers, it is also useful in network analysis and malicious behaviors detection.
In July 2018 we had completed the first version. We will complete the second version by October 2018 with the improvement of user experience and increased number of identifiable devices.
The first generation is a hardware device based on Raspberry Pi with wireless network interface controllers. We will customize new hardware in the second generation. The system can be set up with software part in laptops after essential environment configuration. The software part is available in software_tools/.
Proof of principle
Our approach is based on the detection of malicious network traffic. A device implanted malware will communicate with the remote server, trigger a remote shell or send audios/videos to the server.
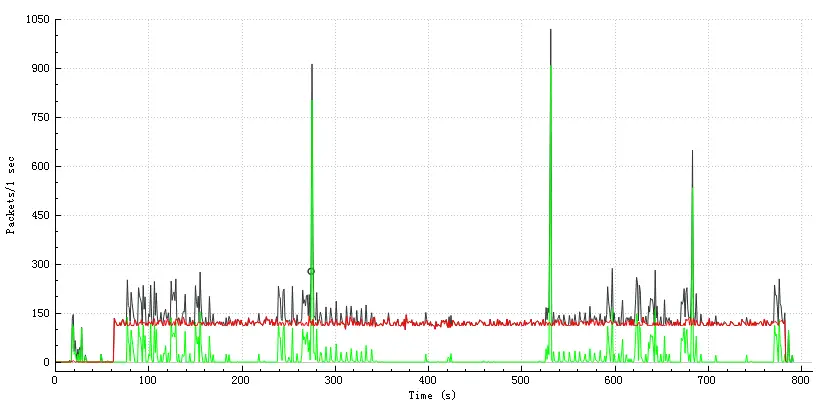
The chart below shows the network traffic of a device which implanted snooping malware.
Red line: traffic between devices and a remote spy server.
Green line: normal traffic of devices.
Black line: Sum of TCP traffic.
Supported Devices
| Device Name | Product Version |
|---|---|
| Xiaomi MINI smart speaker | LX01 |
| Amazon Echo v1 smart speaker | v1 |
| Amazon Echo v2 smart speaker | v2 |
| Xiaofang ip camera | iSC5 |
| Baidu WiFi Translator | TUGE830 |
| Xiaomi Mijia driving recorder | ZNHSJ01BY |
| Netease Youdao smart translator | GTA07 |
Modules
- AP module and Data flow catcher: Catch network traffic.
- The traffic analyzing engine: Extract characteristics from network traffic and compare them with the device fingerprint database.
- Device fingerprint database: Normal network behaviors of each device, based on the whitelist. Call APIs of 360 threat intelligence database (https://ti.360.net/).
- Web server: There may be a web server in the second generation.
Procedure
The tool works as an Access Point, connected manually by devices under test, sends network traffic to traffic analyzing engine for characteristic extraction. The traffic analyzing engine compares characteristics with entries in the device fingerprint database to recognize device type and suspicious network connection. Device fingerprint database is a collect of normal behaviors of each device based on the whitelist. Additionally, characteristics will be searched on threat intelligence database of Qihoo 360 to identify malicious behaviors. A web server is set up as user interfaces.
Copyright (c) 2018 MarvelTeamLab






