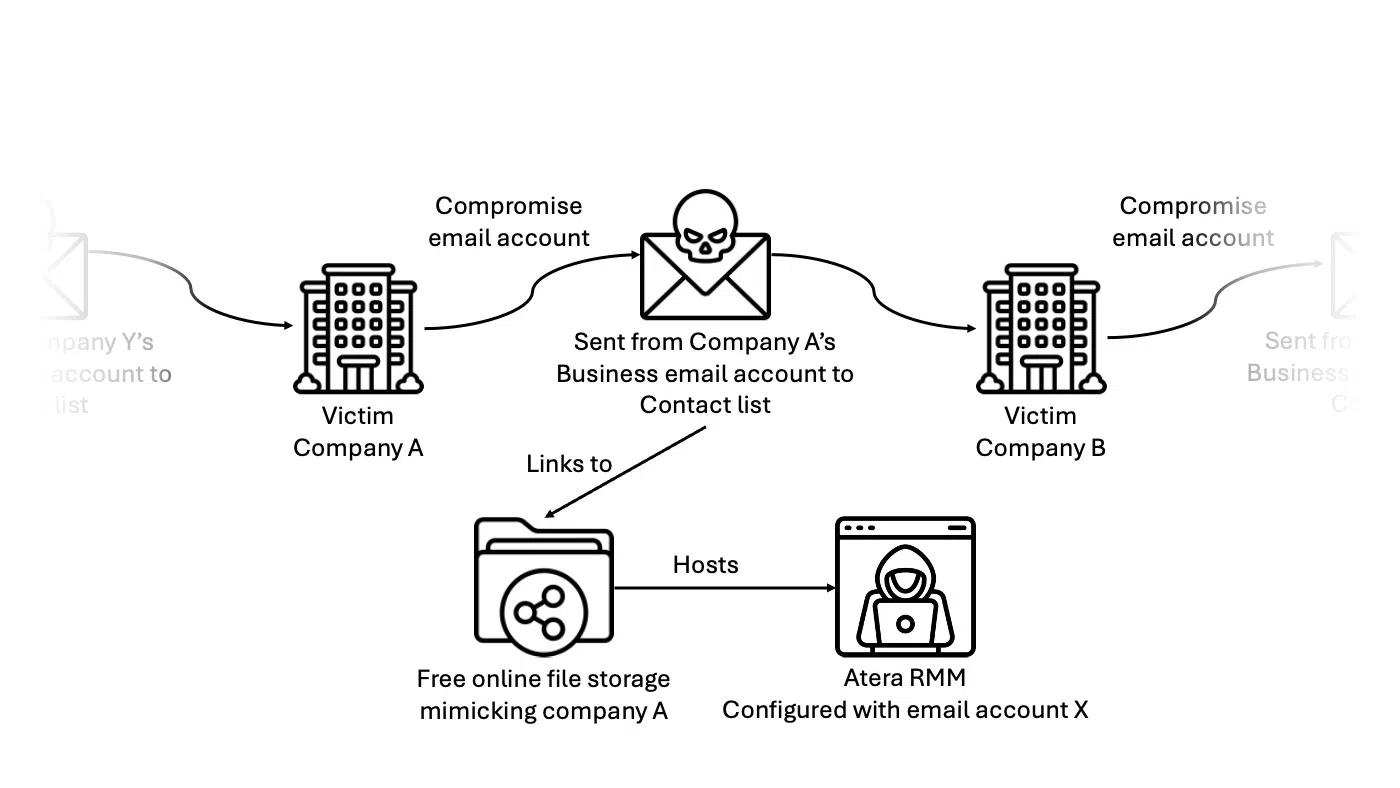
Observed spreading methodology
Security researchers at Harfang Lab have uncovered an ongoing MuddyWater campaign that has been escalating since late 2023. MuddyWater, an Iranian state-backed hacking group, is exploiting the legitimate remote monitoring and management (RMM) solution Atera Agent to gain initial access to victim systems. This shift in tactics provides the attackers with greater operational security and flexibility.

MuddyWater has been active in cyber espionage since at least 2015, focusing on entities across the Middle East and beyond. Their modus operandi typically involves leveraging legitimate software tools to bypass traditional security measures effectively. The recent campaigns have seen a pivot to utilizing Atera Agents, which do not require attackers to establish their infrastructure, thus enhancing their operational security and making attribution more difficult.
The current wave of attacks began in late October 2023 and has continued to escalate. MuddyWater has exploited Atera’s free trial offers to register agents using a mix of compromised business and private email accounts obtained through various methods such as password spraying, exploiting reused passwords, and other deceptive means.
MuddyWater uses free file hosting platforms to distribute their RMM installers. The group employs spearphishing emails to lure recipients to these malicious files. Notably, the quality of these phishing attempts has improved, with emails now featuring more convincing content and professional formatting to enhance their deceit.
Once the Atera Agent is installed, the attackers gain extensive control capabilities directly from Atera’s web UI, which includes uploading and downloading files and running an interactive shell. This agent setup allows the attackers to operate undetected as they do not need to manage their command and control infrastructure.
The use of Atera Agent installation packages linked to MuddyWater has been significant, with packages being registered under various pretexts and delivered through tailored spearphishing emails. This method suggests a high degree of customization in targeting, which spans several sectors including telecommunications, pharmaceuticals, and government entities among others.
The implications of MuddyWater’s recent campaign are profound, highlighting the vulnerability of even legitimate software tools when used by skilled threat actors. Organizations are advised to enhance their email security protocols, enforce strict access controls, and continuously monitor and audit their IT environments for any signs of suspicious activities.