HvS-Consulting GmbH has released an insightful report shedding light on the often-overlooked vulnerabilities of the Network File System (NFS) protocol. Widely used across platforms for remote file access, NFS’s flexibility has inadvertently created security challenges due to misconfigurations and underutilized security features.
The report outlines the research team’s exploration of NFS vulnerabilities, focusing on its security properties, common configuration mistakes, and ways to exploit these weaknesses. The researchers emphasize that while the issues are rooted in the protocol’s intended functionality, improper configurations significantly amplify risks. As the report notes, NFS remains prevalent in both home and enterprise environments, yet it is often misconfigured, exposing critical data to unauthorized access.
“We’ve seen quite a lot, from unauthenticated access to latest R&D data to backups of all virtual machines in otherwise well hardened environments,” the researchers reveal.
The report highlights key security features and challenges of the protocol:
- Authentication Methods: NFS supports multiple authentication flavors, including AUTH_SYS (the default) and Kerberos. While AUTH_SYS offers ease of configuration, it lacks cryptographic verification, relying instead on unverified UIDs and GIDs. Kerberos authentication—although far more secure—remains underutilized, especially in Linux environments, due to its complexity.
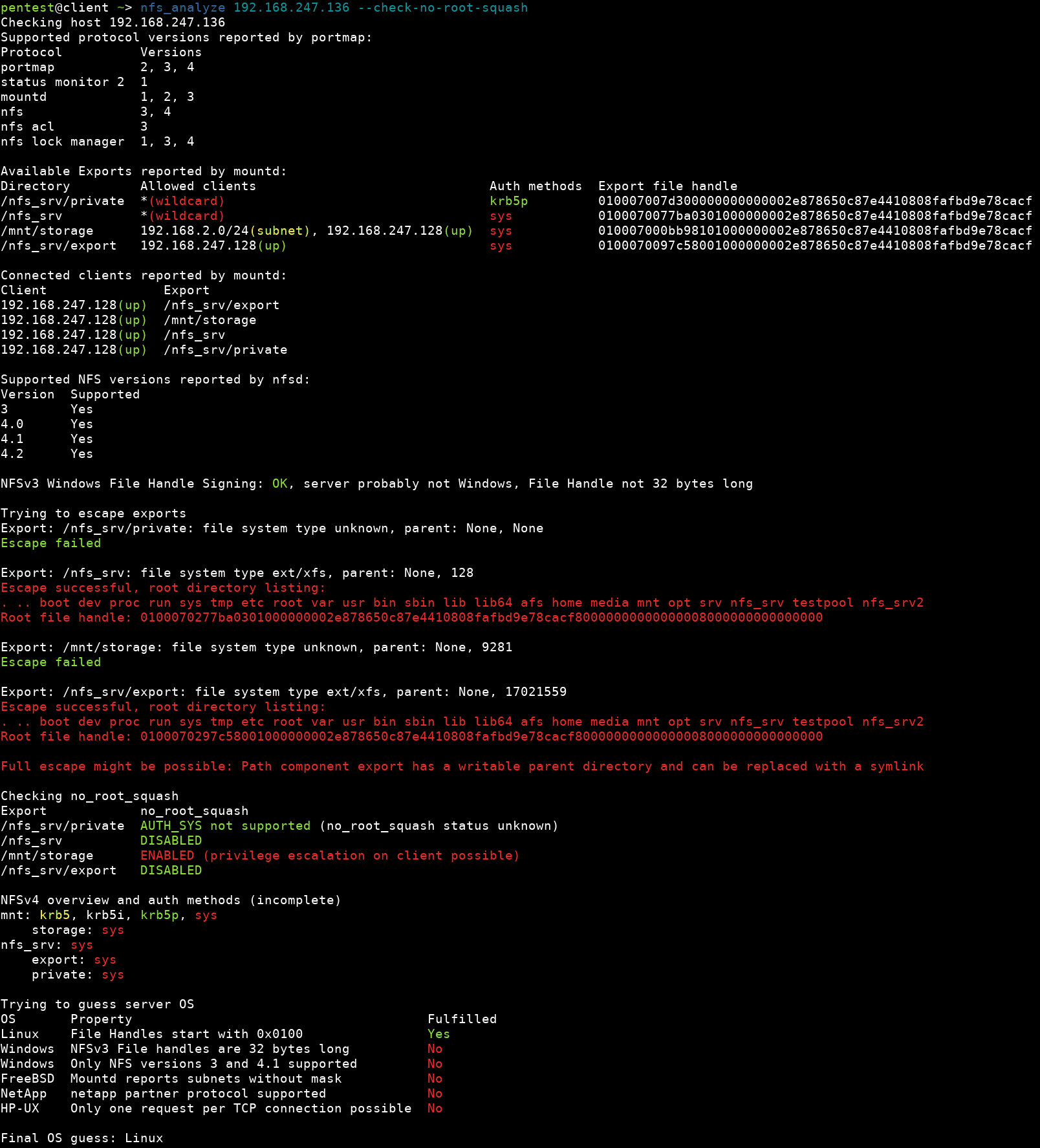
- Export Configurations: Improperly configured exports in the /etc/exports file can expose directories to unauthorized access. Misconfigurations such as enabling no_root_squash or failing to restrict client access exacerbate security risks.
- Subtree Check Misuse: Disabling subtree_check, often the default in Linux systems, can inadvertently allow access to files outside the intended export directory, especially in shared file systems like ext4, xfs, and btrfs.
The report outlines various methods attackers can use to exploit NFS vulnerabilities:
- UID/GID Spoofing: Without proper authentication mechanisms, attackers can impersonate users or groups to gain access to files.
- Privilege Escalation: By exploiting insecure configurations such as no_root_squash, attackers can upload and execute binaries with elevated privileges.
- Directory Escaping: Misconfigured exports and disabled subtree checks allow attackers to traverse and access files outside the exported directory, including sensitive files like /etc/shadow.
HvS-Consulting developed specialized tools to identify and exploit NFS misconfigurations, including:
- fuse_nfs: A FUSE driver for NFS that transparently maps UIDs and GIDs to bypass authentication mechanisms and access files.
- nfs_analyze: A tool for assessing server configurations, identifying misconfigurations like no_root_squash, and testing access to sensitive directories such as /etc/shadow.
To mitigate these vulnerabilities, the report recommends:
- Restrict Access: Limit NFS exports to specific clients and implement strict network segmentation.
- Enable Authentication: Use Kerberos or newer protocols like RPC-with-TLS for secure client-server communication.
- Optimize Export Configurations: Avoid enabling no_root_squash, use all_squash where possible, and ensure exports are isolated in their own file systems.
- Regular Auditing: Continuously review and update NFS configurations to ensure adherence to best practices.