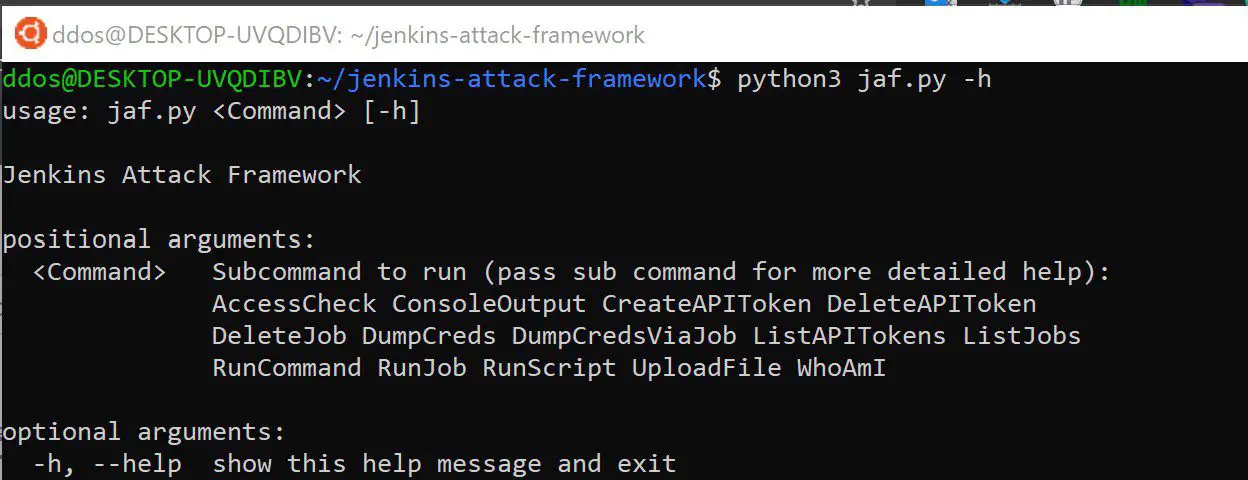
Jenkins Attack Framework
This project can currently perform the following tasks:
- AccessCheck: Test credentials and provide a rough overview of their access levels
- ConsoleOutput: Dump the console output of the last build of every job on the server (Can be Gigabytes of data, but good for finding credentials)
- CreateAPIToken: Creates an API Token for the current user (Or another user if you have administrative credentials)
- DeleteAPIToken: Deletes an API Token for the current user (Or another user if you have administrative credentials. Lists existing ones if no token supplied)
- DeleteJob: Delete a Job, or failing that, attempt a number of follow-up mitigations from most-to-least effective.
- DumpCreds: Dump credentials (Uses administrative credentials to dump credentials via Jenkins Console)
- DumpCredsViaJob: Dump credentials via job creation and explicit enumeration (User needs at least Add Job permissions)
- ListAPITokens: List existing API tokens for the current user (Or another user if you have administrative credentials)
- ListJobs: List existing Jenkins Jobs (Good For finding specific jobs)
- RunCommand: Run system command and get output/errors back (Uses administrative credentials and Jenkins Console)
- RunJob: Upload a script and run it as a job. Also, run “Ghost Jobs” that don’t terminate or show up in Jenkins (after launch)
- RunScript: Run Groovy scripts (Uses administrative credentials to run a Groovy Script via Jenkins Console)
- UploadFile: Upload a file (Uses administrative credentials and chunked uploading via Jenkins Console)
- WhoAmI: Get the credentialed user’s Jenkins groups (Usually contains their domain groups)
- More things are in the works…
Install
git clone git@github.com:Accenture/jenkins-attack-framework.git
cd jaf
chmod +x jaf
sudo ./jaf –install
./jaf –install
Use
Tutorial
Copyright (c) 2021 Accenture