JSON Interoperability Vulnerability Labs
Companion labs to “An Exploration of JSON Interoperability Vulnerabilities”
Description
These are the companion labs to my research article “An Exploration of JSON Interoperability Vulnerabilities”.
Lab 1: Free purchases in an E-commerce Application
- Key Collision Attacks: Inconsistent Duplicate Key Precedence
- Inconsistent Large Number Representations
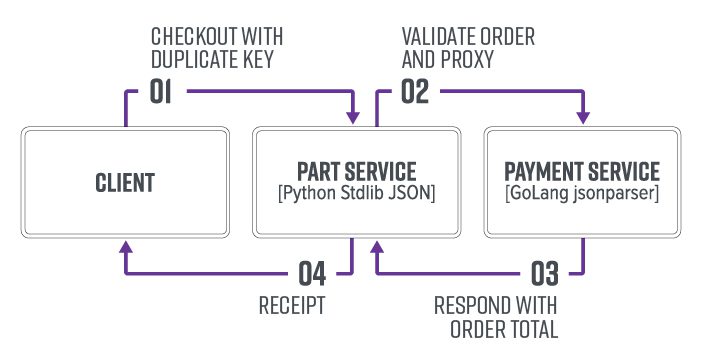
 This lab demonstrates a vulnerability pattern when two services use JSON parsers with inconsistent duplicate key precedence. The Cart service will decode a positive quantity, while the Payment service will decode a negative quantity. In this example, this will lead to an attacker receiving items without paying for them.
This lab demonstrates a vulnerability pattern when two services use JSON parsers with inconsistent duplicate key precedence. The Cart service will decode a positive quantity, while the Payment service will decode a negative quantity. In this example, this will lead to an attacker receiving items without paying for them.
There are two services:
- Cart API (port 5000): Python, stdlib JSON
- Payments API (port 5001): Go, buger/jsonparser library
Lab 2: Privilege Escalation in a Multi-tenant Application
- Key Collision Attacks: Character Truncation
 These labs bind to host ports 5000-5004, by default.
These labs bind to host ports 5000-5004, by default.
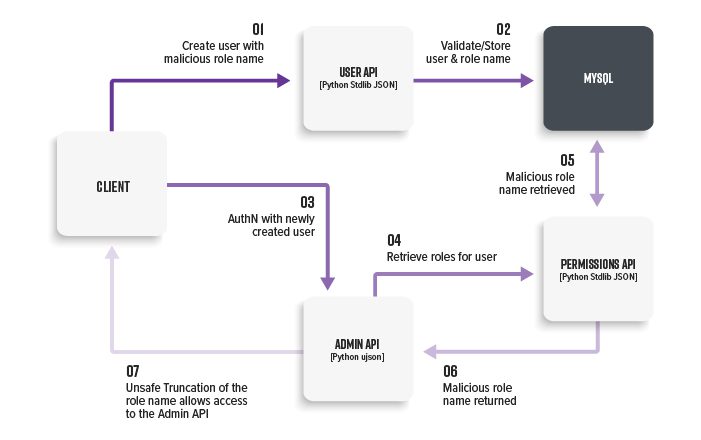
Let’s consider a multi-tenant application where an organization admin is able to create custom user roles. We also know that users that have cross-organizational access are assigned the internal rolesuperadmin . Let’s try to escalate privileges.
There are two APIs:
- User API (port 5002): Python, stdlib JSON
- Permissions API (port 5003): Python, stdlib JSON
- Admin API (port 5004): Python, ujson
Attack Techniques
1. Key Collisions
Inconsistent Duplicate Key Precedence
{"qty": 1, "qty": -1}
Character Truncation
Truncation in last-key precedence parsers (flip order for the first-key precedence)
Comment Truncation
These documents take advantage of inconsistent support of comments and quote-less string support:
2. Number Decoding
Inconsistent Large Number Decoding
These large numeric values may be converted to Strings (e.g., “+Infinity”), which may lead to type-juggling vulnerabilities. Or, they may be converted to MAX_INT/MIN_INT, rounded values, or 0, which may allow a bypass of business logic.
Download
Author
Twitter: @theBumbleSec
GitHub: the-bumble