JSScanner
Scanning JS Files for Endpoints and Secrets
- Gather the javascript file links present in a domain.
- Discover the endpoints present in those javascript
- Then save those javascript files for further static analysis where we can look for hardcoded credentials and stuff
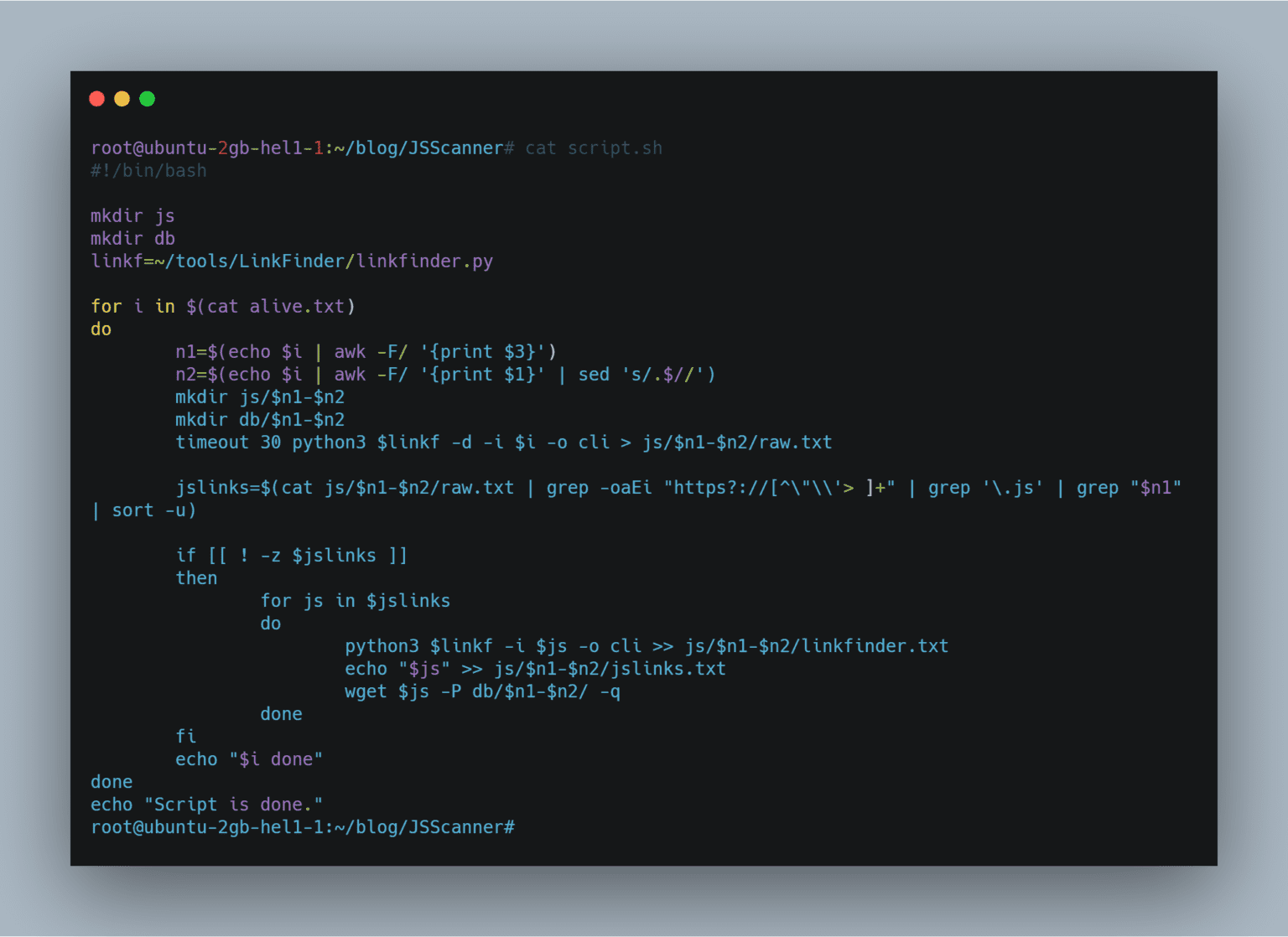
So this script will crawl the domain present in alive.txt.
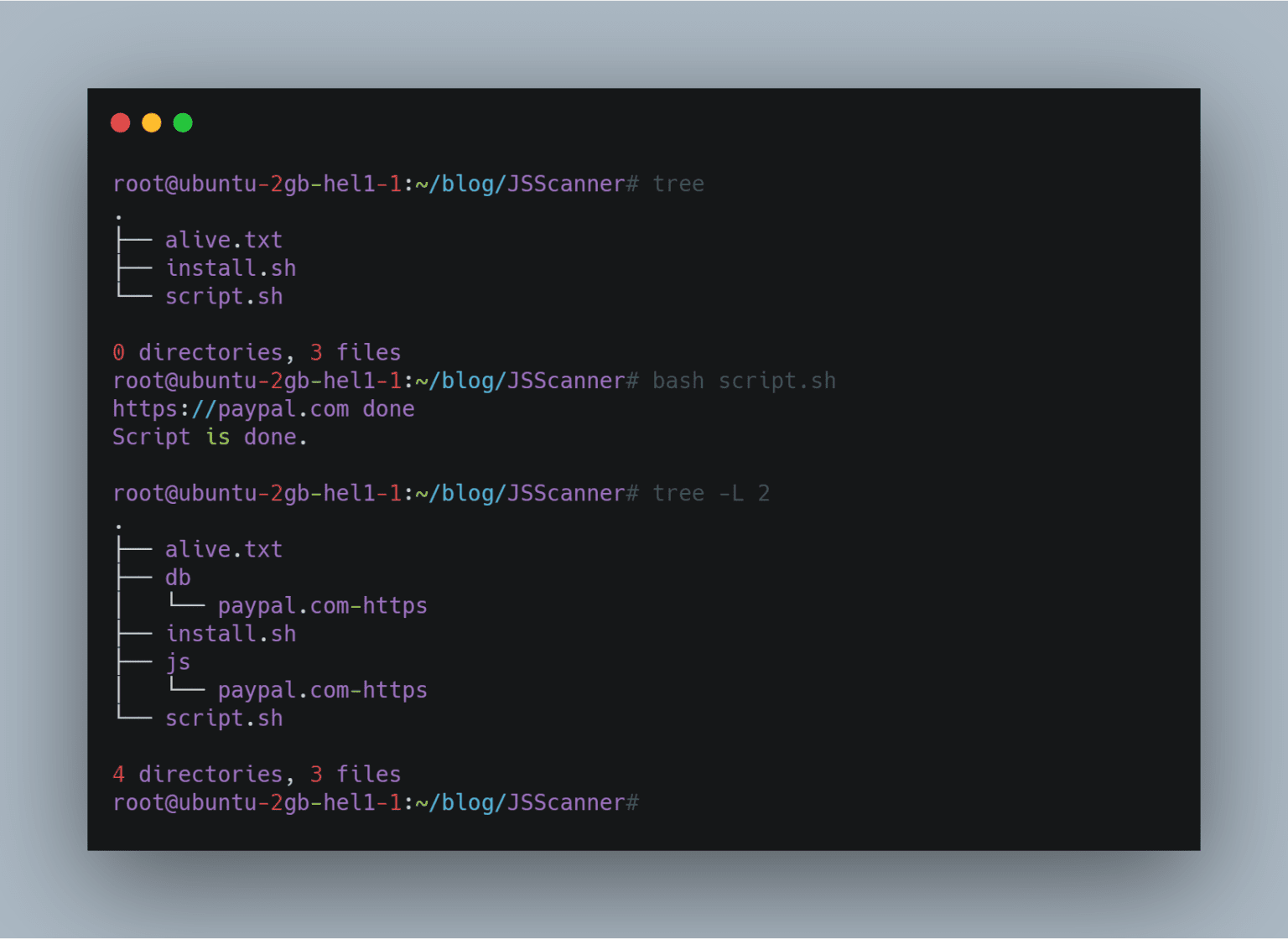
When you run the tool it will process the domain present in alive.txt and will create two folders js and db.
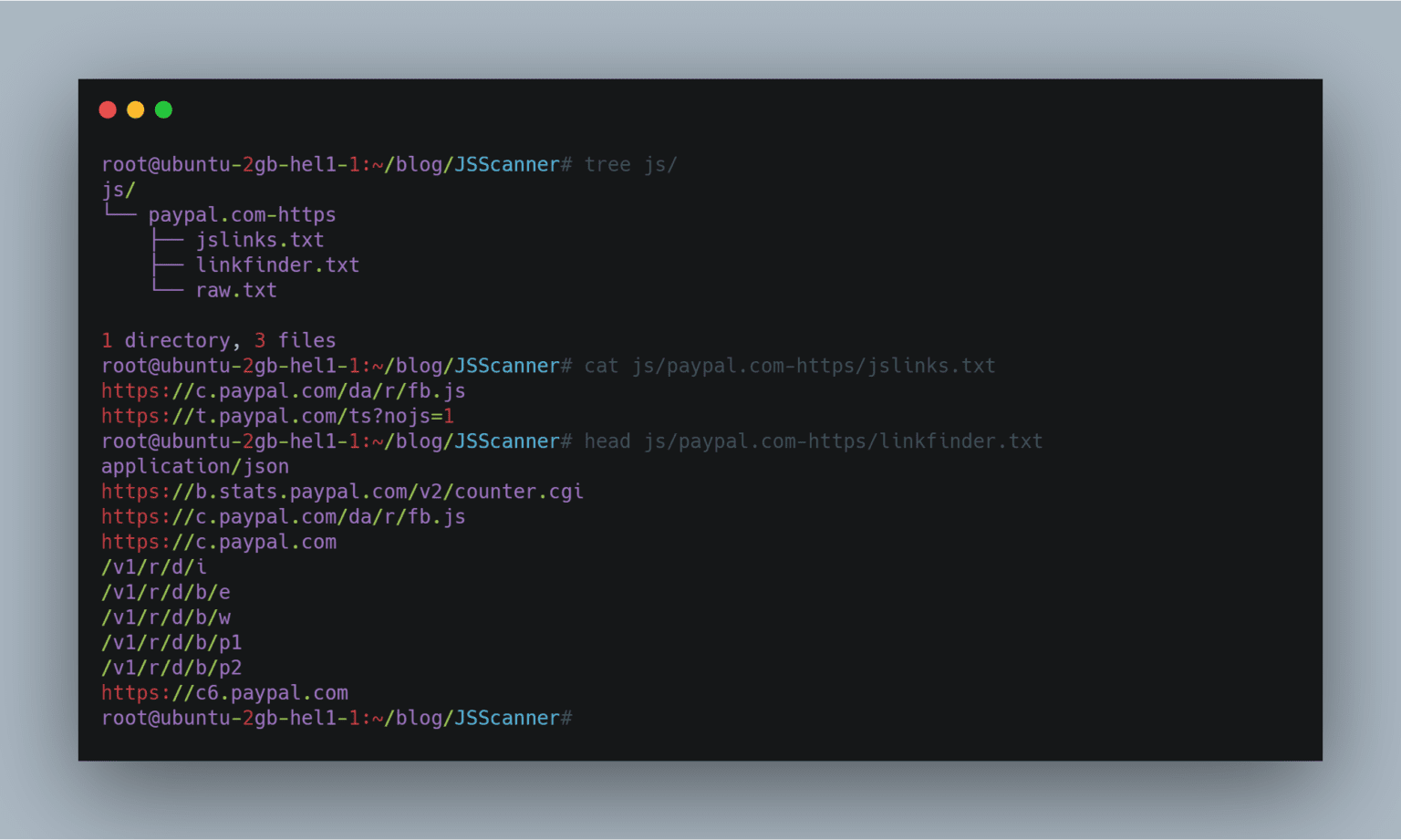
It will then crawl the javascript files from those domains and save the javascript links and LinkFinder result to js folder.
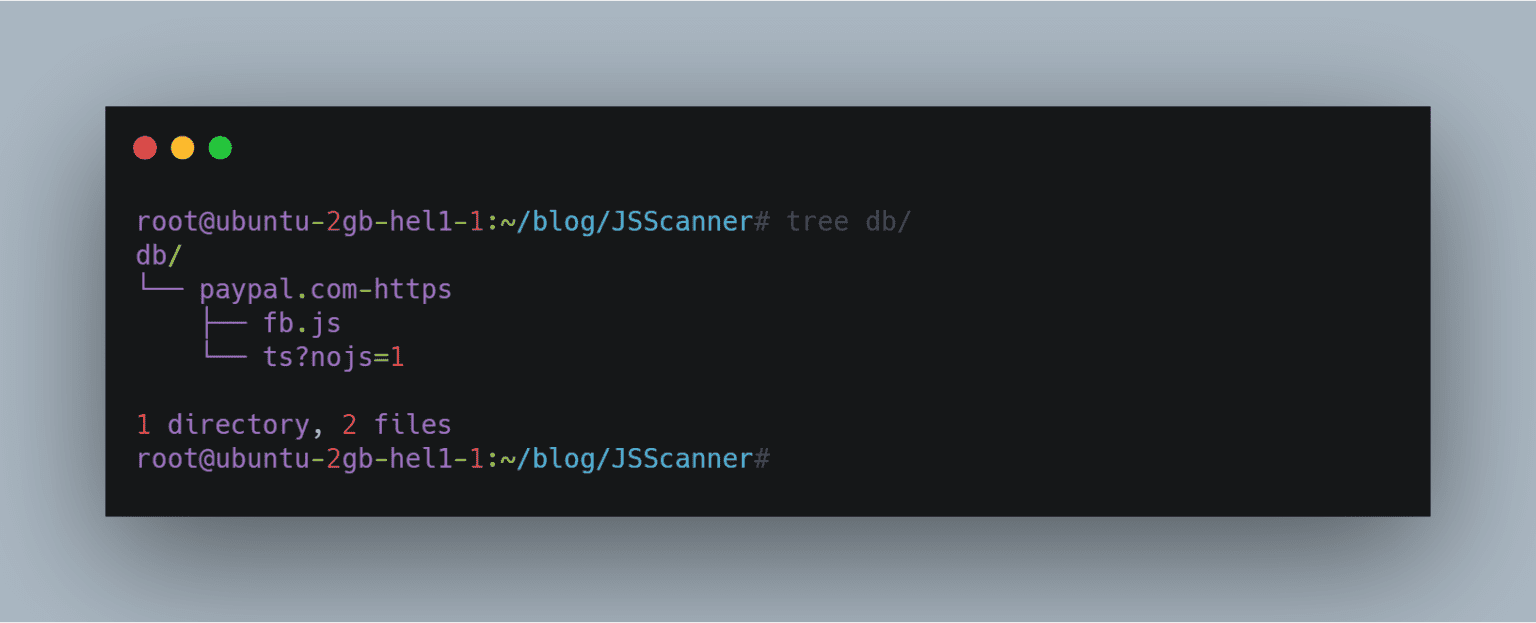
It will save the javascript in the db folder for further manual analysis.
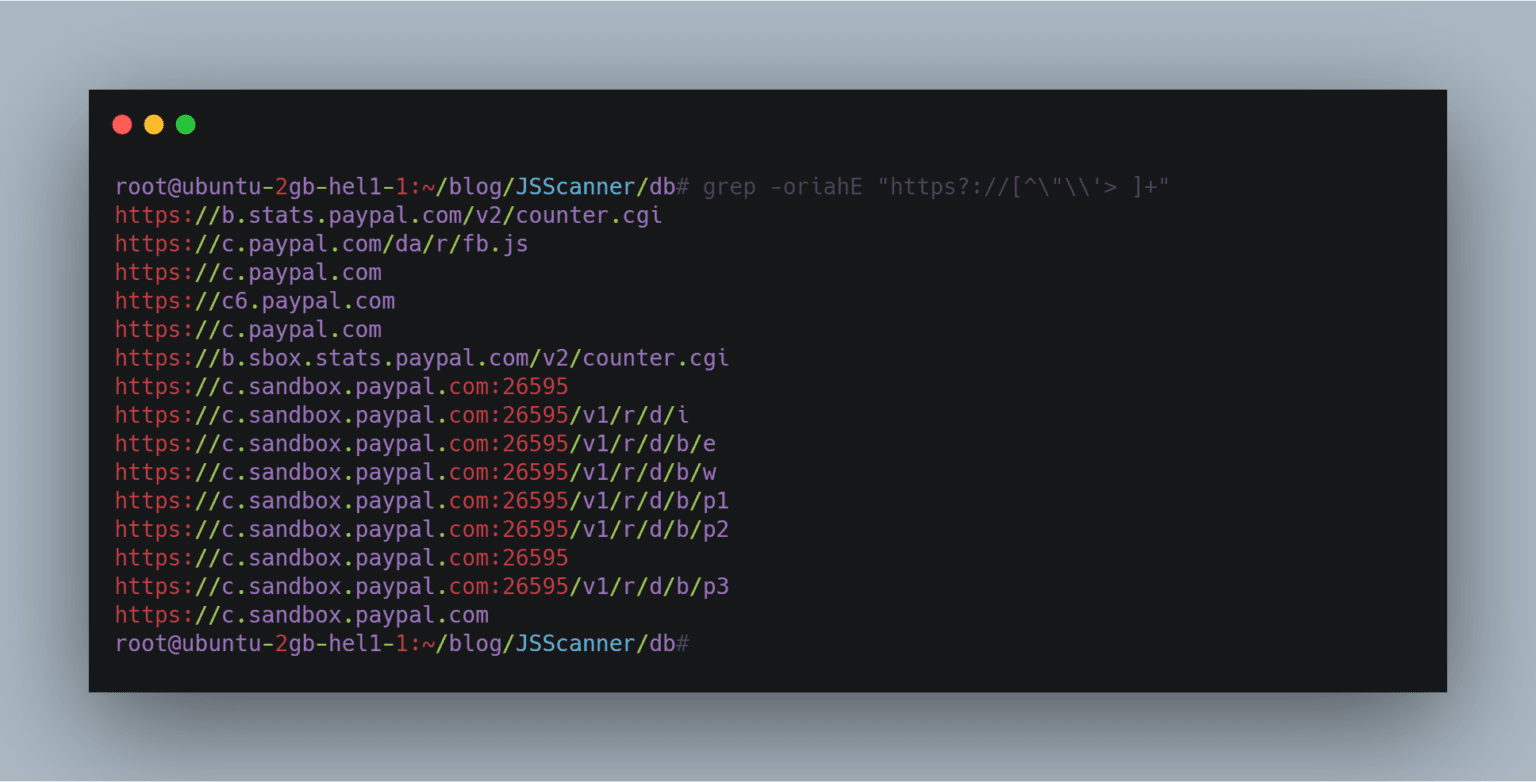
Now comes the part to look for secrets or hardcoded strings in those js files. So we can get into the db folder and grep for anything we like.
At this stage, you can use your own creativity and look for certain keywords like amazonaws.com. api_key, api_secret, token. or also for var to identify potential GET or POST parameters.
Download
git clone https://github.com/dark-warlord14/JSScanner.git
bash install.sh
Use
Change the alive.txt with the domains you need to test. These are should be in below format
http://example.com
https://example2.com
To run the tool use
bash script.sh
Source: https://github.com/dark-warlord14/