JWT Key ID Injector
Simple python script to check against hypothetical JWT vulnerability.
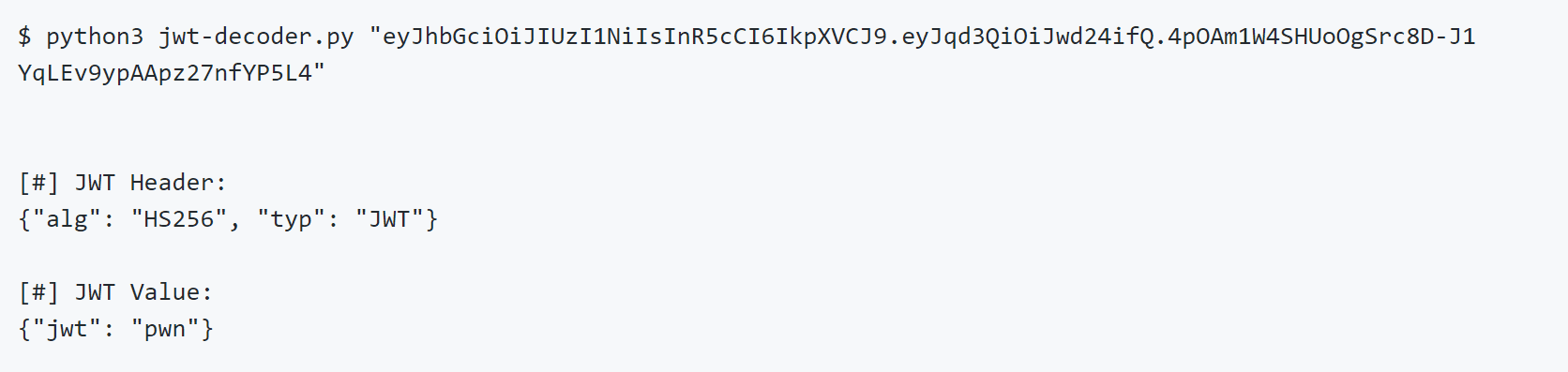
Let’s say there is an application that uses a JWT tokens signed HS256 algorithm. An example token looks like the following:
The above token can be decoded to the following data:
To calculate signature the following secret is used:
supersecret
The following pseudo-code is used to calculate the signature:
But what if a kid field is a standard way to choose a key. My assumption is that, if a kid field is not expected, there may be a vulnerable implementation that will treat the string $key value as an array:unexpected “kid”:0 field will be injected into the header?
hmac($alg, $data, $key[kid]);
As a result “s” ($key[0]) value will be used as an HMAC secret.
Download
git clone https://github.com/dariusztytko/jwt-key-id-injector.git
Use
injector.py script takes original JWT token, injects “kid”:0 field into the header and generates tokens signed with the one-letter secrets (ASCII codes: 32 – 126 [{space}, !, “, #, …, x, y, z, {, |, }, ~]):
As result, two files are created – tokens.txt and tokens_meta.txt. tokens.txt contains generated tokens and can be used as a list of payloads for the Burp Intruder. If any token is valid (which means that the application is vulnerable), the tokens_meta.txt file can be used to check what algorithm and secret were used to generate the given token. tokens_meta.txt file contains the following data:
Copyright (C) 2020 dariusztytko
Source: https://github.com/dariusztytko/