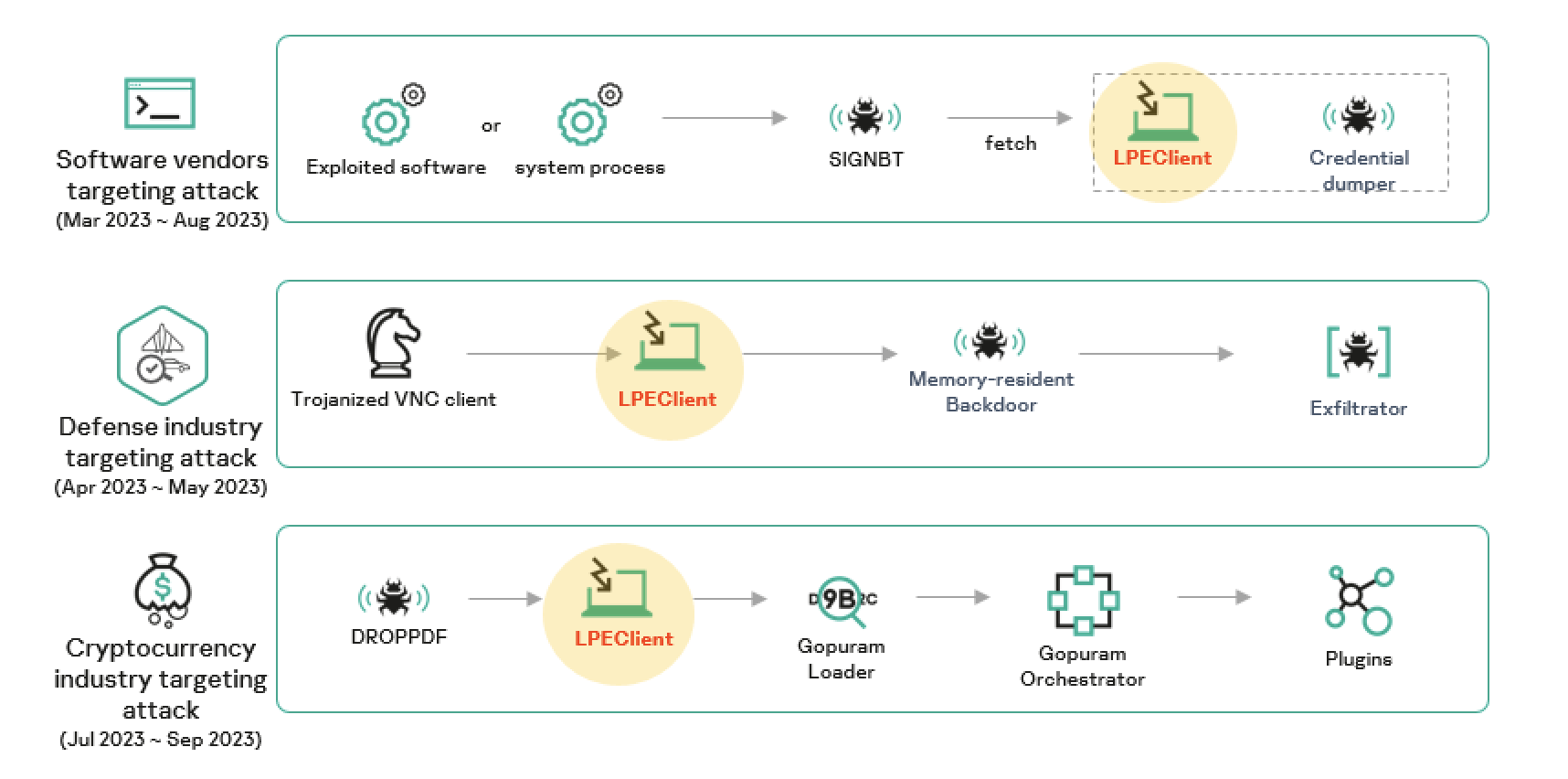
The infection chains of the three campaigns attributed to Lazarus in 2023 | Image: Kaspersky
In recent months, the Lazarus group, a notorious cyber threat actor, has shown increased activity, exploiting software vulnerabilities to compromise systems. While the vulnerabilities themselves were not new, what is particularly concerning is that several systems, despite having available patches, remained vulnerable.
Earlier this year, a software vendor was compromised using Lazarus malware. Astonishingly, this wasn’t the first time. Kaspersky’s security researchers discovered that this software vendor had previously been a victim of Lazarus on several occasions. The continuous breaches highlight a persistent threat actor with probable intentions of pilfering valuable source code or interfering with the software supply chain.

One alarming discovery was the introduction of the SIGNBT malware, aiming to control victims. A peculiar feature is its complex loader process. Originating from a file named `ualapi.dll`, it relies on a sequence in the Windows registry to validate its victim. If validated, the malware uses an AES decryption key to decrypt its payload and begins its malicious activities. The uniqueness of the SIGNBT malware lies in its communication. It uses specific strings starting with SIGNBT, which stands as its designation.
The malware’s communication with its Command & Control (C2) server is intricate. The C2 communication comprises a 24-byte value, combining a hard-coded value, an MD5 hash of the victim’s computer name, and a randomly generated identifier. This structure, designed to validate and secure communications, involves a repetitive procedure applied to every HTTP communication sequence.
The functionality of SIGNBT’s backdoor is vast. Its commands reflect commonly used Windows functions, with the added ability to implant additional payloads for automatic execution.
Apart from SIGNBT, another critical component of Lazarus’s arsenal is the LPEClient malware. Initially detected in a defense contractor attack in 2020, this malware operates predominantly in system memory, ensuring stealth. The recent versions of LPEClient have been enhanced to avoid detection, like disabling user-mode syscall hooking and restoring system library memory sections, indicating the group’s intent to enhance their malware’s efficacy.
The employment of LPEClient malware has been consistent across Lazarus group campaigns. Despite different initial infection vectors and chains, LPEClient remains pivotal in delivering the final payload. This trend was evident in campaigns targeting defense contractors, nuclear engineers, and the cryptocurrency sector in 2023.
The Lazarus group’s ever-evolving tactics underline the profound challenges faced by cybersecurity professionals today. Their diverse targets, ranging from software vendors to various industry sectors, emphasize their vast capabilities and adaptability. The recurrent compromise of the same software vendor indicates the relentless pursuit of their objectives. The introduction and sophistication of malwares like SIGNBT and LPEClient exemplify their advanced technical capabilities.
In conclusion, the Lazarus group, with its sophisticated methods and unwavering motivations, continues to be a formidable adversary in the digital realm. Vigilance, regular patching, and advanced threat detection are more critical than ever in combating such advanced threats.