Kaspersky Lab specialists have uncovered a Trojan module within modifications of the popular messenger WhatsApp, widely disseminated via Telegram channels. This espionage software, dubbed CanesSpy, masquerades as a regular messenger, yet the infected Android versions harbor covert tracking capabilities.
This revelation came to light following a meticulous analysis of the application’s manifest, where discrepancies from the original version were discovered, including an added third-party service and receiver not present in the legitimate application.
The broadcast receiver, configured to listen for system events such as device charging or SMS receipt, activates a service that initiates the spy module’s operation. The malicious code then establishes communication with a command and control (C2) server, transmitting the victim’s device information, including IMEI, phone number, and other identifiers. Moreover, the spyware dispatches data on the victim’s contacts and accounts every five minutes.

In its continued operation, the malicious software periodically solicits new commands from the C2 server to carry out actions on the infected device. Analysts discovered that the commands on the server were in Arabic, suggesting the malware developer’s likely Arabic-speaking origins.
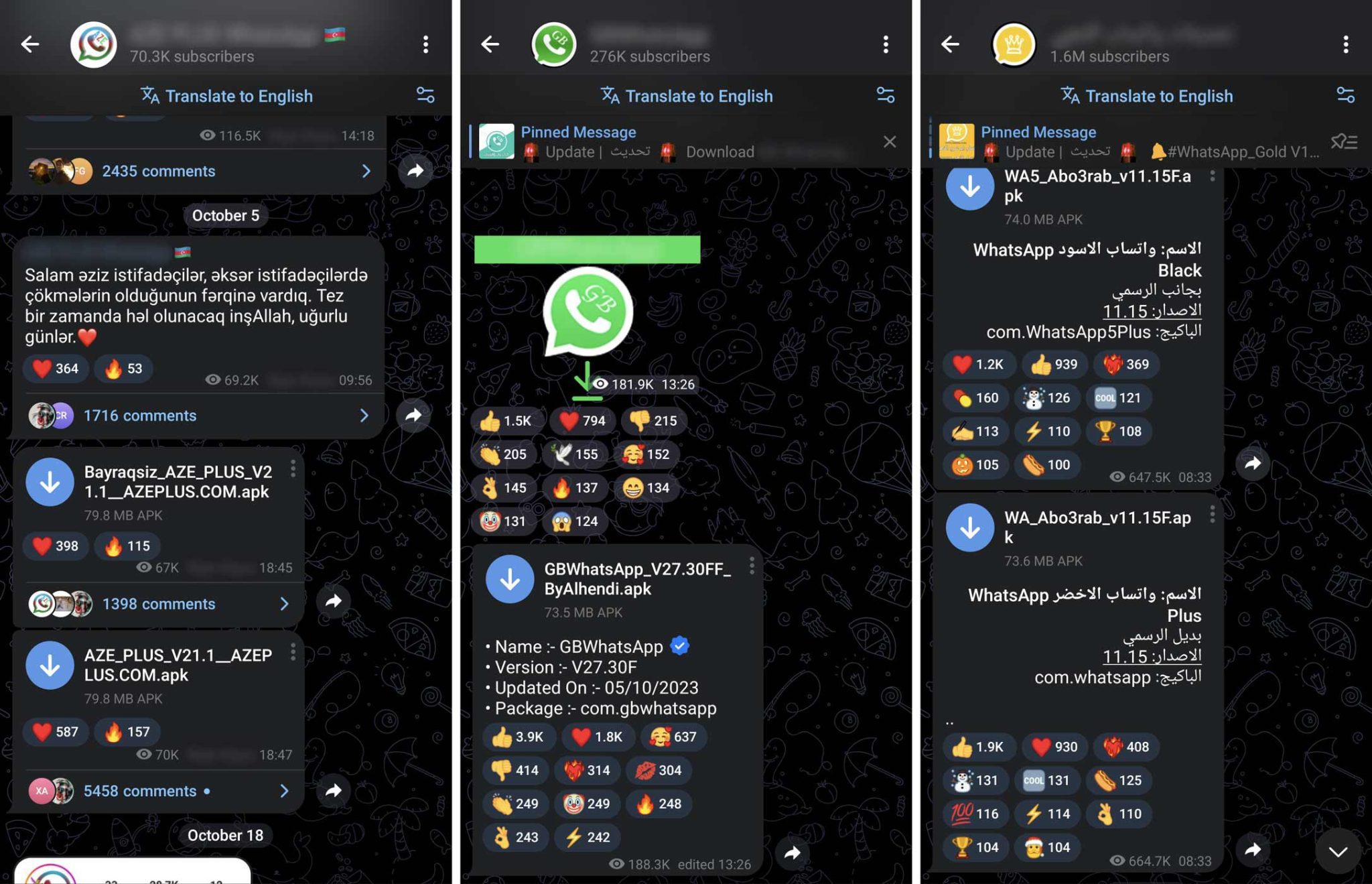
The investigation revealed that Telegram channels, predominantly featuring Arabic and Azerbaijani texts, are the primary dissemination vectors for the modified WhatsApp, with the most popular channels boasting nearly two million users. The channel creators have been warned about the presence of malware in their materials.
Experts note that the spy modules have been activated since mid-August 2023, and all software versions downloaded since then have contained the malicious code. However, in one channel, the latest viral modification was replaced with the original version. Besides Telegram channels, the infected messenger versions are also distributed on websites specializing in WhatsApp modifications.
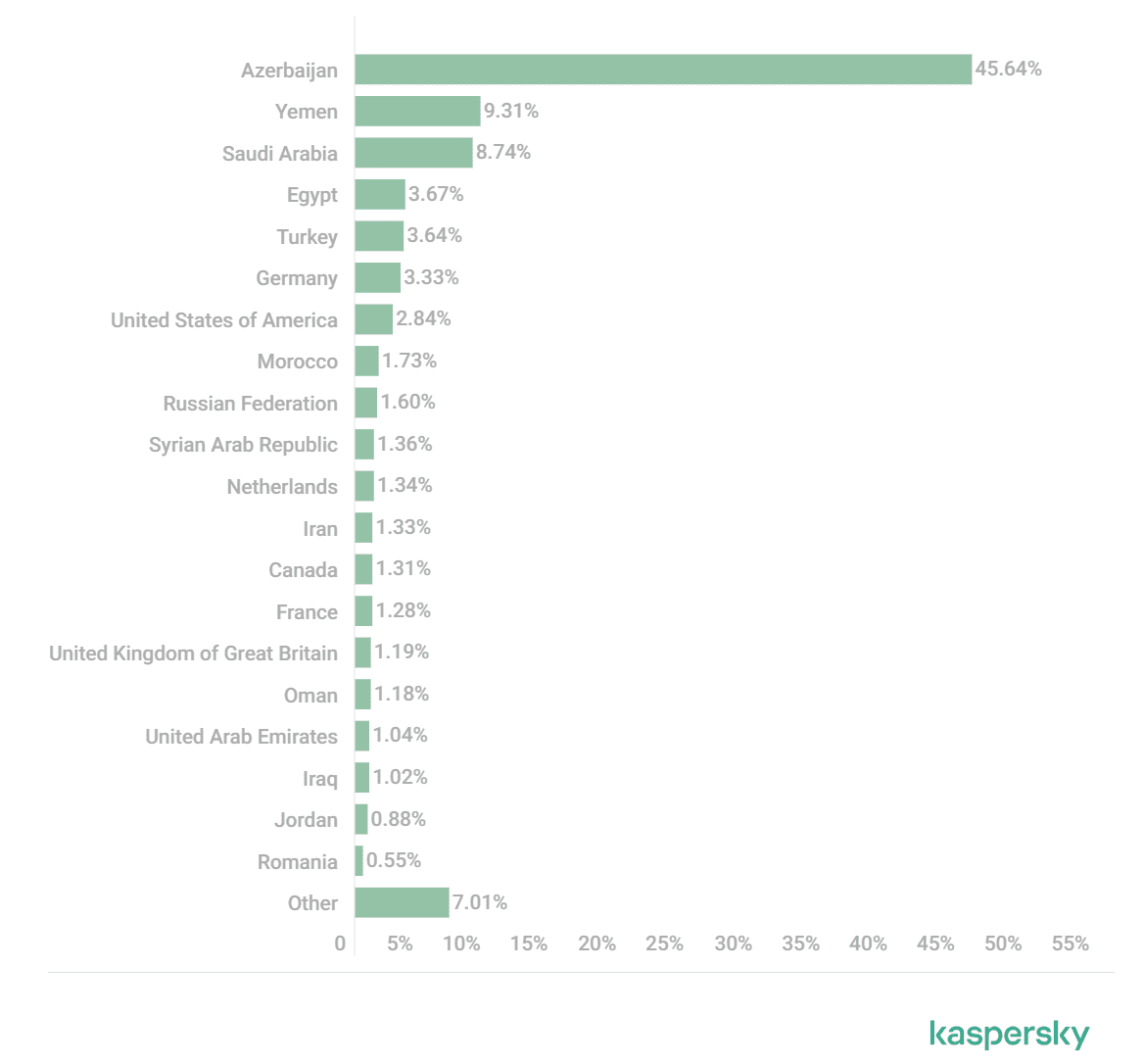
Between October 5 and 31, Kaspersky Lab blocked over 340,000 attack attempts via the modified WhatsApp across more than 100 countries worldwide. Nonetheless, given the distribution methods, the actual number of spyware installations could be significantly higher. Azerbaijan, Yemen, Saudi Arabia, Egypt, and Turkey top the list of countries with the most attacks.
Users are strongly advised to avoid downloading messenger apps from unverified sources and to use only official services for installing applications.