Image: Teppei Fukuda
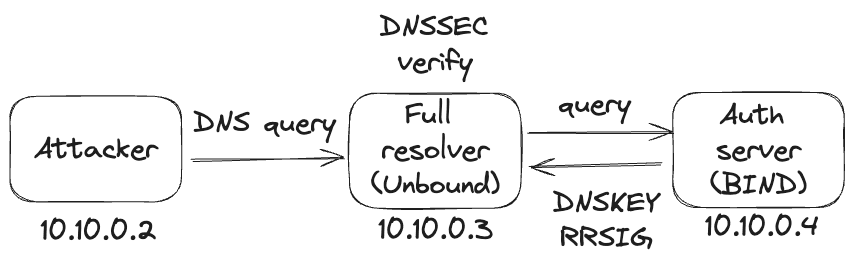
A proof-of-concept (PoC) was disclosed for a severe design flaw (CVE-2023-50387) in Domain Name System Security Extensions (DNSSEC), leaving DNS infrastructures vulnerable to widespread denial-of-service (DoS) attacks. Known as “KeyTrap“, this exploit targets DNSSEC-validating resolvers, which function as the internet’s address verification system.
Discovered by the vigilant researchers at the ATHENE National Research Center for Applied Cybersecurity in Germany, KeyTrap enables a nefarious actor to trigger a prolonged denial-of-service (DoS) condition in affected resolvers with just a single DNS packet. This packet, meticulously crafted, can exhaust CPU resources, bringing services to a grinding halt.

The potential consequences of a large-scale KeyTrap attack are significant. Researchers indicate that over one-third of DNS servers are vulnerable, translating to the potential for substantial impact on individuals and businesses globally. Over 31% of web clients, as of December 2023, were found to be at risk, relying on DNSSEC-validating DNS resolvers. DNS service providers such as Google and Cloudflare, while not immune, have initiated mitigations.
KeyTrap works by sending maliciously crafted DNS responses that trigger excessive CPU resource consumption within the DNSSEC validation process. This prolonged overload could render resolvers unresponsive, impacting accessibility to essential internet services such as web browsing, email, and other online applications. The attack’s simplicity and efficiency have led some DNS vendors to label it as the most devastating attack method ever identified.
Fortunately, impacted vendors alerted months prior, have been releasing patches, with the final fixes rolled out by mid-February. However, the resolution of this vulnerability is not as straightforward as issuing patches. Addressing KeyTrap at its root requires a fundamental reevaluation of DNSSEC’s design philosophy—a daunting task that underscores the complexity of securing the Internet infrastructure upon which the world relies.
With the proof of concept (PoC) for CVE-2023-50387 now published by security researcher Teppei Fukuda, organizations must prioritize the immediate application of these security updates to mitigate the risk posed by KeyTrap attacks.