LaZagneForensic: Decrypt Windows Credentials from another host
The LaZagne Project !!!
Description
The LaZagne project is back !!!
LaZagne uses an internal Windows API called CryptUnprotectData to decrypt user passwords. This API should be called on the victim user session, otherwise, it does not work. If the computer has not been started (when the analysis is realized on an offline mounted disk), or if we do not want to drop a binary on the remote host, no passwords can be retrieved.
LaZagneForensic has been created to avoid this problem. This work has been mainly inspired by the awesome work done by Jean-Michel Picod for DPAPICK and Francesco Picasso for Windows DPAPI laboratory.
Note: The main problem is that to decrypt these passwords, the user Windows passwords are needed.
Installation
git clone https://github.com/AlessandroZ/LaZagneForensic.git
cd LaZagneForensic
pip install -r requirements.txt
Usage
First way – Dump configuration files from the remote host
- Using the powershell script
- Using the python script
- Launch Lazagne with password if you have it
- Launch Lazagne without password
Second way – Mount a disk on your filesystem
- The file should be mounted on your filesystem
- Launch Lazagne with password if you have it
- Launch Lazagne without password
Note: Use -v for verbose mode and -vv for debug mode.
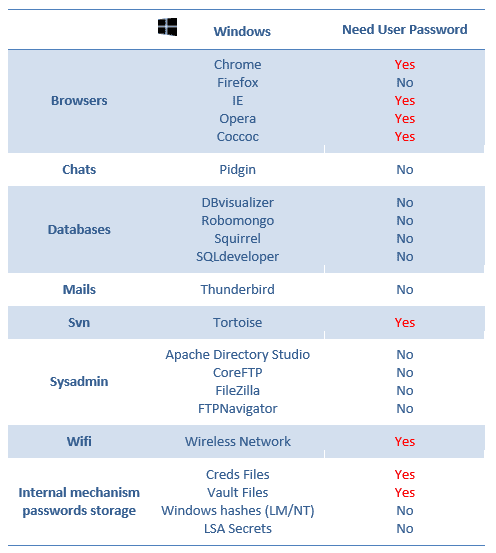
Supported software
Note: Check the following image to understand which passwords you could decrypt without needed the user windows password. All credentials found will be tested as Windows password in case of the user re-uses the same password.
Donation
Do not hesitate to support my work doing a donation, I will appreciate a lot:
- Via BTC: 16zJ9wTXU4f1qfMLiWvdY3woUHtEBxyriu
Source: https://github.com/AlessandroZ/






