Post by Signum Capital identifying the scam
The world of blockchain and angel investing can be thrilling but also fraught with risks. Security experts from Hunt are currently tracking a sophisticated phishing scheme aimed squarely at entrepreneurs operating within Telegram communities focused on these exciting industries. The tactics uncovered bear a striking resemblance to the methods commonly employed by Lazarus Group, a notorious North Korean state-sponsored hacking operation.
The Phishing Playbook

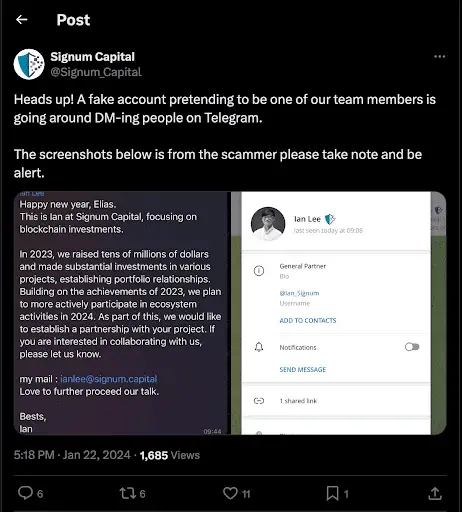
On January 22, 2024, Signum Capital, a venture capital firm caught in the crosshairs of this campaign, raised the alarm on Twitter, warning of an impersonator lurking in Telegram’s shadows. This revelation came on the heels of a December exposé by the SlowMist team, who detailed a similar scam attributed to the Lazarus Group, further thickening the plot.
The scheme unfurls with the creation of a decoy Telegram profile, through which the attacker, posing as a “GP” (General Partner), initiates contact under the guise of exploring a potential collaboration. This is social engineering at its finest, with the attacker weaving a tapestry of trust through casual conversation, only to ensnare the victim with the promise of a scheduled call via Calendly—an online scheduling tool akin to Google Calendar.
What the victim receives isn’t a standard meeting invite, but a roadblock – a deliberately crafted error message claiming access restrictions. The attackers, feigning helpfulness, then swoop in offering a technical solution in the form of a malicious Apple Script. Under the false pretense of “fixing” the issue, they convince the target to download and run this dangerous code.
The script, named IP_Request.scpt, is a masterstroke of deception, leveraging the shell command ‘curl’ to fetch malicious code under the guise of troubleshooting. The stage is set, the actors in place, and the tragedy unfolds as unsuspecting victims execute the script, unwittingly compromising their devices.
The Malicious Code Unveiled
The so-called “fix” is, in fact, a wolf in sheep’s clothing. Let’s break down what this script does:
- Suspicious Domain: A dubious domain (
support[.]internal-meeting[.]site) is assigned to a variable for later use. - Downloading the Payload: A command is executed, instructing the system to download a script from the assigned domain.
- Stealthy Execution: The downloaded script is immediately executed, unleashing its harmful intent.
This seemingly innocent “troubleshooting” measure is the key to gaining control over the victim’s device.
The Infrastructure’s Trail of Clues
Security researchers, following the digital breadcrumbs left by these attackers, have uncovered a tangled web of domains, IP addresses, and certificates. Close analysis of these elements reveals a pattern strikingly consistent with the known playbook of North Korean hackers:
- Servers of Choice: Repeated use of Hostwinds ASN dedicated servers, a common tactic in Lazarus Group campaigns.
- Cheap and Fast Certificates: Preference for Let’s Encrypt SSL certificates, offering attackers quick and convenient cover.
- The Domain Registrar Connection: A reliance on Namecheap (along with other registrars) to purchase domains for their malicious activities.
- Unique Signatures: Specific 403 & 404 HTTP response hashes, acting as identifying fingerprints for these threat actors.