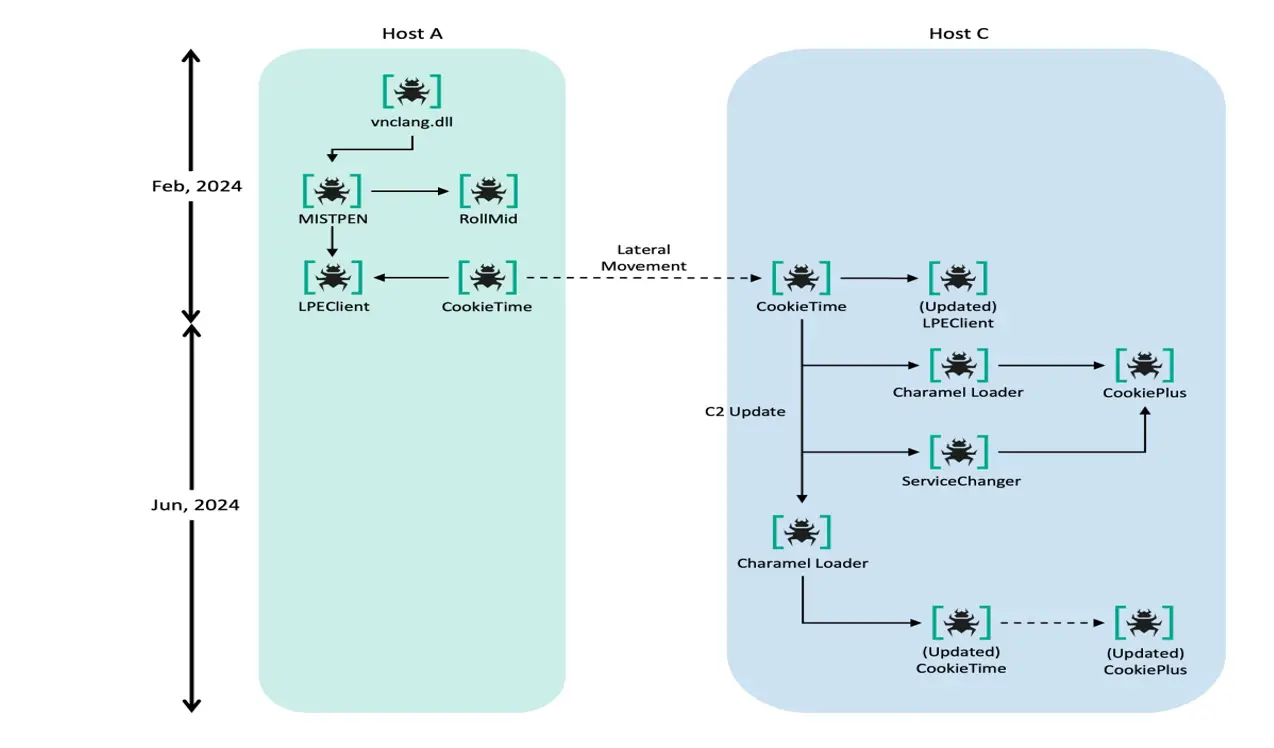
Overall malware-to-malware flowchart | Source: Kaspersky
In a recent analysis by Kaspersky Labs, the infamous Lazarus Group continues to refine its strategies, blending old tactics with new malware to create advanced and stealthy attack chains. Dubbed the DeathNote Campaign, or Operation DreamJob, this operation primarily exploits fake job opportunities to infiltrate industries such as defense, aerospace, cryptocurrency, and nuclear sectors.
“The Lazarus group has been distributing its malicious software by exploiting fake job opportunities targeting employees in various industries,” Kaspersky researchers noted. In their latest campaign, Lazarus used malicious archive files disguised as skill assessments for IT roles, delivering malware to employees of a nuclear-related organization. These attacks employed a mix of trojanized tools and advanced loaders, showcasing an evolving sophistication.
The infection chain uncovered by Kaspersky highlights several key components:
- Trojanized Utilities: Tools like AmazonVNC.exe and UltraVNC Viewer were modified to execute malicious payloads. AmazonVNC.exe, a trojanized version of TightVNC, decrypted and executed the Ranid Downloader to advance the attack chain.
- Sophisticated Loaders: Using malicious DLLs, such as vnclang.dll, attackers sideloaded malware like MISTPEN, RollMid, and the newly identified LPEClient, enabling lateral movement and further payload delivery.
- New Modular Malware: A standout in this campaign was CookiePlus, a plugin-based downloader designed to fetch and execute additional malicious components. CookiePlus acts as a successor to MISTPEN, supporting more execution options and behaving just like a downloader, making it challenging to investigate its full capabilities.
To bypass detection, Lazarus delivered its malware through compressed ISO files, which are less scrutinized than ZIP archives. Victims were tricked into executing these files via social engineering on platforms like LinkedIn, Telegram, and WhatsApp. Once executed, the malware utilized XOR keys and sophisticated decryption techniques to unpack payloads.
Additionally, CookiePlus leveraged ChaCha20 encryption for its communications, disguising its activity as legitimate. “The group consistently masquerades malware as public utilities like Notepad++ plugins to evade defenses. This approach allowed the group to persist undetected while launching subsequent attacks.
The Lazarus Group’s ability to pivot and evolve its tools illustrates the persistent and adaptive nature of advanced threat actors. “Throughout its history, the Lazarus Group has used only a small number of modular malware frameworks, but introducing new tools like CookiePlus signals ongoing innovation in their arsenal,” Kaspersky concludes.
Related Posts
- Temptation from Money: Lazarus APT extended to cryptocurrencies
- From Spear-Phishing to Zero-Day: Lazarus Group’s Latest Cyber Strategies
- North Korea’s Lazarus Group: A Persistent Threat to the Defense Sector
- Fake Crypto Game Hides Chrome Zero-Day CVE-2024-4947 Attack by Lazarus APT
- North Korean Hackers Launch Job Interview Scam to Deploy BeaverTail and InvisibleFerret Malware