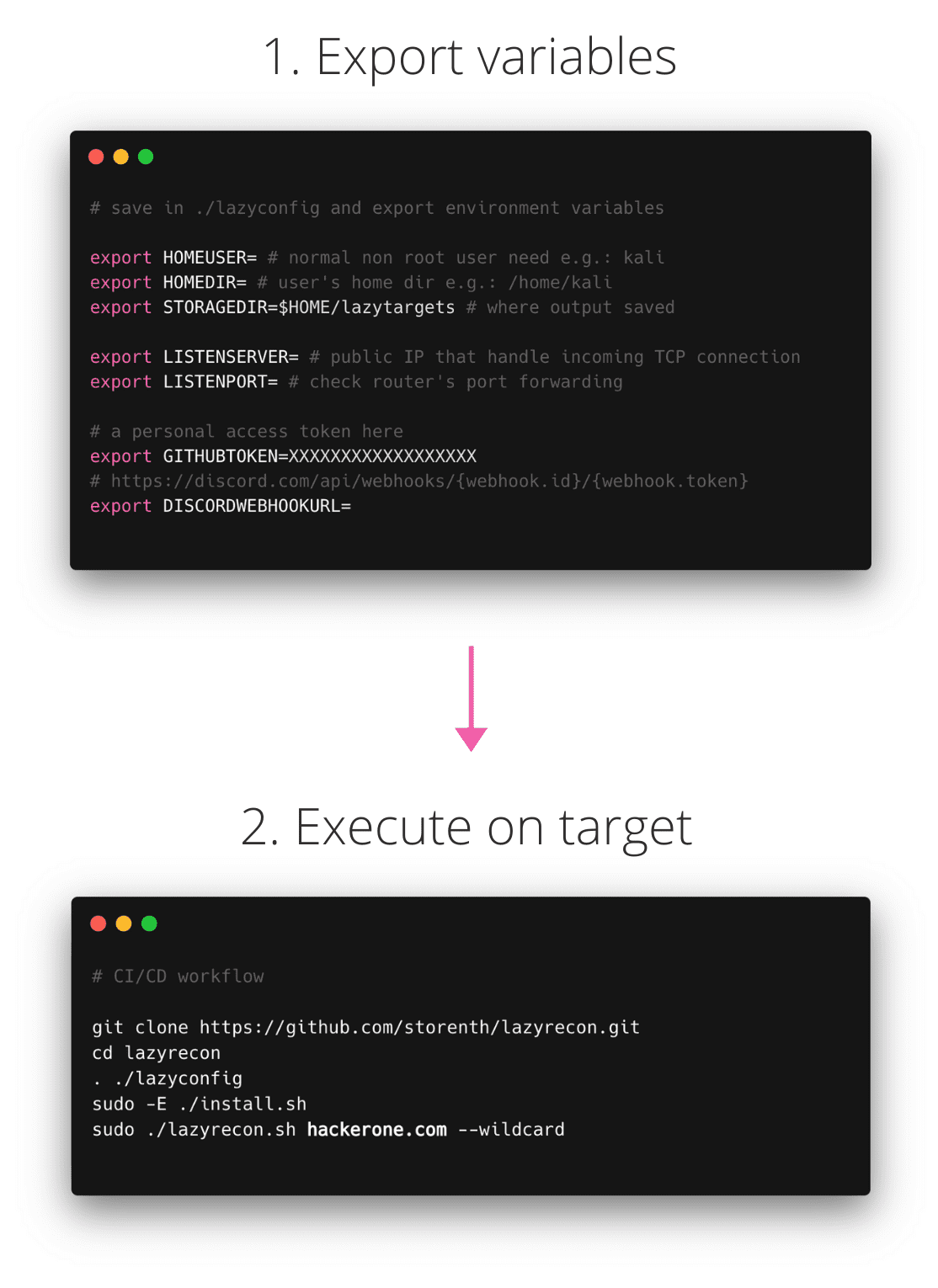
lazyrecon
Lazyrecon is a subdomain discovery tool that discovers and resolves valid subdomains then performs SSRF/LFI/SQLi fuzzing and port scanning. It has a simple modular architecture and is optimized for speed while working with github and the wayback machine.
Features
- Superfast asynchronous execution
- CI/CD ready
- HTML/pdf reports
- Discord integration
- Background listen server
- Domain name, list of domains, IP, CIDR input notations support
- Teardown and program exit housekeeping
This script is intended to automate your reconnaissance process in an organized fashion by performing the following:
- Create a dated folder with recon notes for target
- Grab subdomains using
subfinder,assetfinder,gau,waybackurls,github-subdomains - Subdomain discovery through alterations and permutations using
altdnsanddnsgen - Filtering out live subdomains from a list of hosts using
shuffledns - Check 1-200,8000-10000 for http(s) probes using
httpx - Get visual part using
aquatone - Perform
masscanon live servers - Automatically brute-forces services with default credentials using
hydra - Scanning for known paths and CVEs using
nuclei - Shot for SSRF/LFI/SQLi based on wayback machine’s data
- Check for potential request smuggling vulnerabilities using
smuggler - Perform
ffufusing custom WordList based on the top10000.txt - Generate reports and send it to Discord
The point is to get a list of live IPs, attack available network protocols, check for common CVEs, perform very simple directory bruteforce then use provided reports for manual research.
Methodology
- Use dnsperftest to know your best resolvers
- Run ./lazyrecon.sh
- Check output reports of aquatone, nuclei, nmap, hydra, server_log, ffuf
- Explore file upload vulnerabilities
- Perform Google, Trello, Atlassian, Github, Bitbucket dorking
- Check JS sources for credentials, API endpoints
- Investigate
XHRrequests, fuzz parameters, and variables - Check exploit-db.com for target-specific CVE
- GET/POST Bruteforce for directories: fuzbo0oM-top10000 –> raft –> target specific
- Continue bruteforcing using custom Headers (X-Custom-IP-Authorization: 127.0.0.1; X-Original-URL:)
- Try bypass 401/403 errors using notable methods (%23, /%2e/, admin.php%2500.md etc)
- Look for XSS xsscrapy.py or XSSTRON